Microsoft’s August 2021 Patch Tuesday Brings 44 Security Fixes Across a Range of Products
- Another monthly fixing update has been released for Windows and various other Microsoft products.
- The patch brings 44 fixes for a variety of vulnerabilities, with nine of them being rated as critical.
- In seven cases, the flaws would be trivial to exploit or at least worth the hackers’ effort.
Microsoft has released this month's ‘Patch Tuesday’ security update for Windows and a range of other software products, and the pack brings 44 fixes for a variety of vulnerabilities. Of the flaws that have been addressed, one has already been disclosed previously, and another one is under active exploitation. There are nine critical bugs, among which seven have a high potential for exploitation to achieve remote code execution. As such, applying the patch as soon as possible is imperative.
The actively exploited flaw is “CVE-2021-36948”, which is an elevation of privilege in the Windows Update Medic service. Although Microsoft has detected exploitation in the wild, no PoC has been published, and so the attacks leveraging the particular bug are limited in scope and number. Most likely, it is only used by sophisticated ransomware actors who want to maximize the damage by stealthily creating user accounts on the infiltrated network before initiating the encryption process.
The already-disclosed problem is “CVE-2021-36942,” which gives away more details about the ‘PetitPotam’ attack vector, which is likely to be exploited although not weaponized and targeted by malicious actors yet. Remember, Microsoft has also released an advisory about this last week, so if applying the patch is impossible, you should at least follow the mitigation advice.
Then there’s also “CVE-2021-36936”, a remote code execution flaw in Windows Print Spooler that has proven to be a persistent issue for Microsoft’s engineers. However, it is not clear if this is just a variant of the same vulnerability or a new, unique flaw.
Other bugs that are very likely to be exploited are:
- “CVE-2021-34480” – Scripting Engine memory corruption flaw
- “CVE-2021-26432” – Memory corruption vulnerability on the kernel driver for Windows Services for NFS
- “CVE-2021-26424” – Remote code execution flaw in Windows TCP/IP
- “CVE-2021-34535” – Remote code execution in Windows Remote Desktop Client
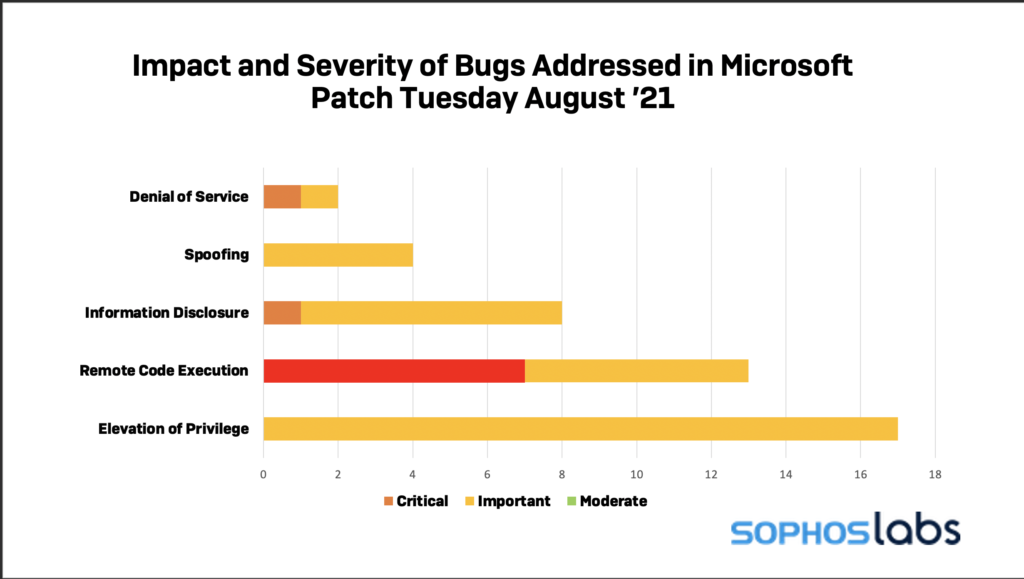
Most of the bugs fixed this month are elevation of privilege flaws, but most of the critical ones belong in the RCE category. Information disclosure, spoofing, and denial of service are also included in the mix.
As always, experiencing problems during the update procedure is nothing unheard of, and a failure to apply the patch could result in a corrupt filesystem that would be impossible to restore. As such, make sure to backup your data before you hit the update button just to be on the safe side.