Microsoft 365 Defender Researchers Disrupted Large-Scale BEC Campaign
- Microsoft’s researchers have uncovered a large BEC operation ran by diligent and careful actors.
- The group of hackers relied upon multiple cloud infrastructure providers and spread their activities thin for stealthiness.
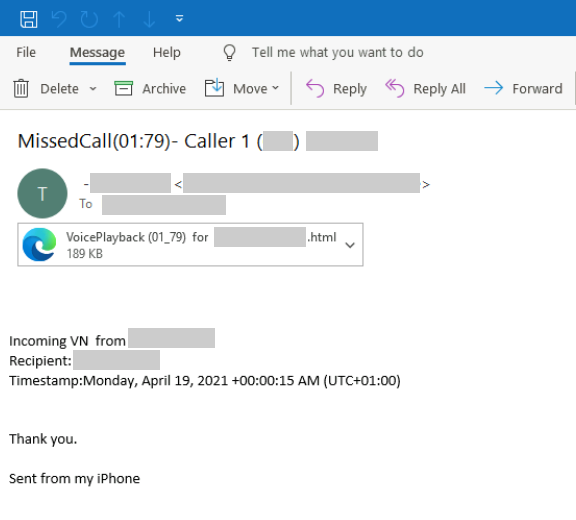
- The compromise started with a phishing email claiming to contain an important voice message for the recipient.
Microsoft’s 365 Defender team has announced the disruption of a large-scale BEC (business email compromise) campaign, using cross-domain threat data to identify and stop the malicious operation. The attackers used cloud-based infrastructure to compromise the target mailboxes by using credentials they stole through spear-phishing and added forwarding rules, eventually accessing valuable financial transaction information.
More specifically, the actors relied upon multiple web services in order to operate stealthily, using different IPs and timeframes to raise the minimum possible number of flags. This approach is also hampering the efforts of white-hat researchers, who find it quite hard to correlate the various activities and connect the fragments into a complete picture pointing to a single actor. Of course, Microsoft’s team has enough data collection and analysis points to be able to identify even the most diligent and careful BEC actors.
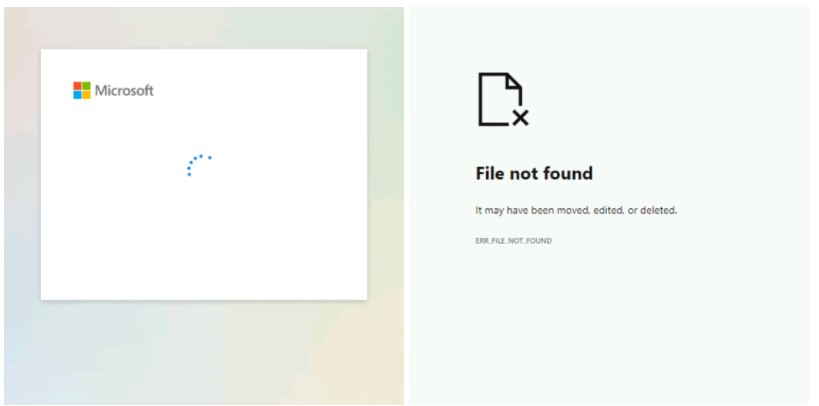
The phishing attack takes place through the typical voice message notification that we have seen many times before. The HTML attachment that comes with these emails contains JavaScript that dynamically decodes to pop up a phony Microsoft sign-in page that automatically populates the username to trick the recipient.
If the victims enter their credentials, they get a login animation and then a “File not found” error. Their password is still transmitted to the crooks in the background, though.
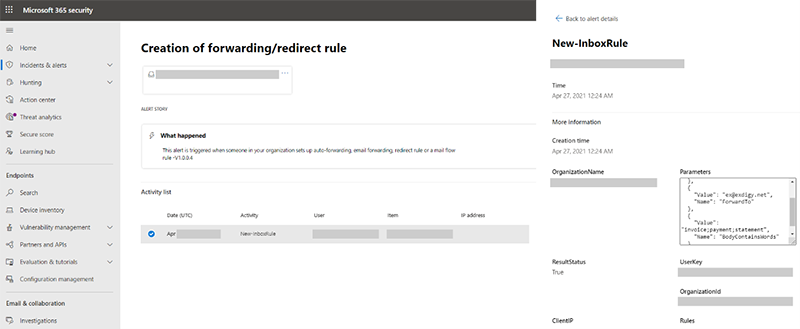
The next step is to set the email forwarding rules, now receiving sensitive data without the victims having realized the breach. The forwarding conditions concern the inclusion of terms like “invoice,” “payment,” and “statement” in the mail body, so the actors are only interested in financial information and the diversion of the transactions.
Even though the actors used different cloud-based infrastructure for their operations, Microsoft’s researchers were able to identify the following commonalities in the user agents:
- Credentials checks with user-agent “BAV2ROPC”, which is likely a codebase using legacy protocols like IMAP/POP3, against Exchange Online. This results in an ROPC OAuth flow, which returns an “invalid_grant” in case MFA is enabled, so no MFA notification is sent.
- Forwarding rule creations with Chrome 79.
- Email exfiltration with a POP3/IMAP client for selected targets.
Also, all of the above activities came from a specific set of IP address ranges, so Microsoft could identify cloud providers. Then, from correlating the same pattern of activities and attack methods, they were able to link the operation to other accounts on more providers, so the veil was lifted.