Microsoft 365 Anti-Phishing Measures Bypassed by Altering ‘First Contact Safety Tip’ via CSS
- Microsoft 365’s anti-phishing measures can be tampered with using simple CSS.
- An attacker could alter an email’s HTML code to hide the First Contact Safety Tip feature.
- This feature is designed to display a message to warn users about incoming emails from lesser-known or unknown addresses.
Attackers with sufficient knowledge of CSS could bypass Microsoft 365's measures for preventing phishing by manipulating the email’s HTML code, according to a report from Certitude security researchers. Formerly known as ‘Office 365,’ the Microsoft tool relies on the First Contact Safety Tip for anti-phishing.
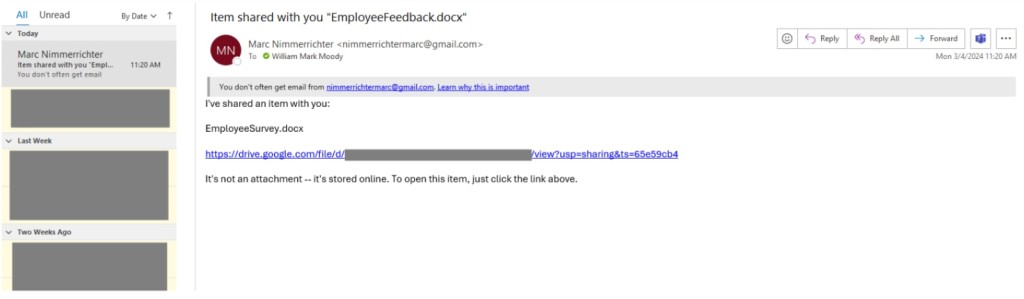
Microsoft 365’s First Contact Safety Tip feature is available via Exchange Online Protection (EOP) and Microsoft Defender to all organizations using Office 365. It alerts users when they receive a message from an email address with which they rarely or never communicate.
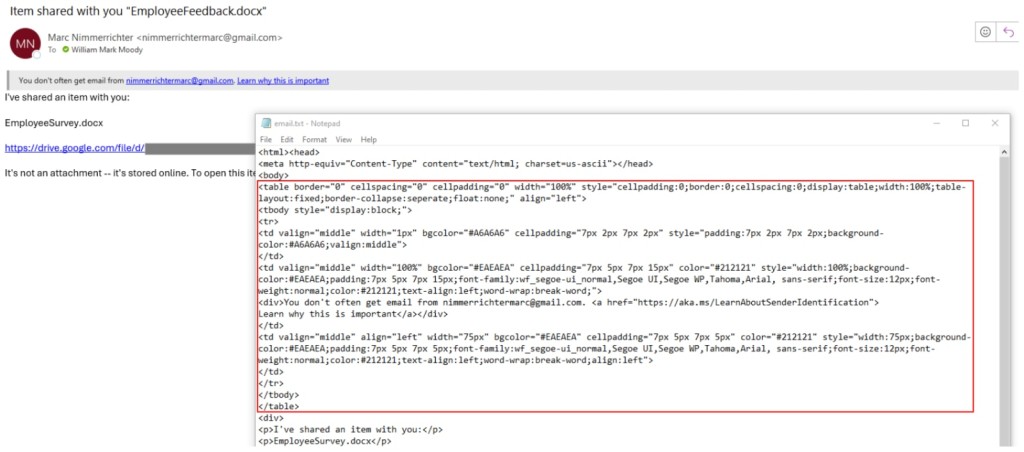
However, a proof of concept (PoC) shows that hackers could reduce the visibility of the Safety Tip by altering the HTML code of the email using CSS style tags.
Changing the background and font colors to white can effectively make the safety tip invisible to users unless they select the entire email content. This did not affect the email preview, which started with the Safety Tip message.
Moreover, security researchers were able to spoof Outlook’s icons, which allow users to recognize encrypted and/or signed emails. In the 'Signed By' section, the period in the email address is actually a Unicode character to prevent Outlook from automatically detecting the email address and generating a 'mailto' link.
Microsoft MSRC responded to the disclosure, saying the finding is valid, but they do not consider this a priority due to its use in phishing attacks.
Recently, a critical in-the-wild exploit of Proofpoint’s email protection service allowed threat actors to steal funds and credit card details via millions of perfectly spoofed phishing emails impersonating Proofpoint customers, which circumvented significant security protections via authenticated SPF and DKIM signatures.