Microsoft 365 Accounts Targeted by Massive Chinese Botnet Password Spraying Attacks
- Large-scale password-spraying attacks launched by a huge botnet targeted Microsoft 365 accounts.
- The botnet executes its attacks via non-interactive sign-ins with Basic Authentication.
- The malicious activity showed similarities to Chinese cyber-espionage groups.
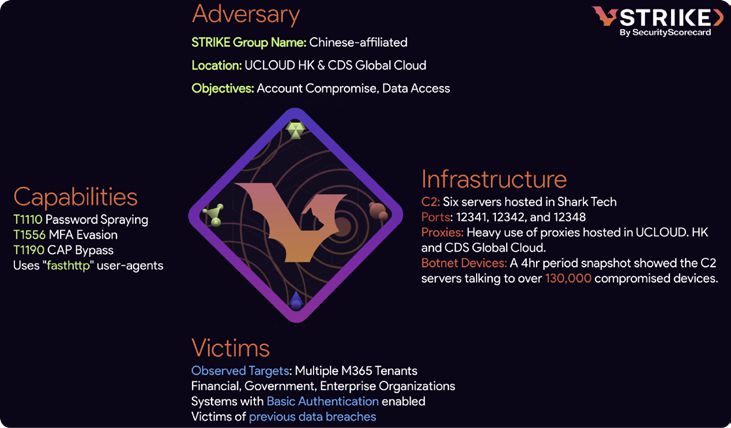
A suspected China-linked botnet comprising more than 130,000 compromised devices has been identified targeting Microsoft 365 accounts through large-scale password-spraying attacks. The botnet employs non-interactive sign-ins with Basic Authentication for execution.
Unlike interactive sessions, non-interactive sign-ins often bypass multi-factor authentication (MFA) in many configurations, making them a vulnerable target, according to a report by cybersecurity firm SecurityScorecard.
Basic Authentication allows credentials to be transmitted in plain text, which further simplifies exploitation for attackers. Despite Microsoft's ongoing effort to phase out Basic Authentication, its use persists in some environments, leaving these configurations exposed to immediate threats.
SecurityScorecard warns that the attacks are difficult to detect as they are logged in non-interactive sign-in records, which are often overlooked by security teams.
The botnet uses credentials gathered by information stealers to test against Microsoft 365 accounts. Over a monitored 4-hour period, SecurityScorecard observed approximately 130,000 devices communicating with six U.S.-based command-and-control servers linked to the botnet.
Successful account compromises allow threat actors to access sensitive data, disrupt business operations, and potentially move laterally within an organization’s network.
The report indicates the botnet may be controlled by a China-linked threat group. This attribution aligns with previous findings from Microsoft, which in October 2024 highlighted multiple Chinese actors leveraging credentials from password spray operations, including networks dubbed CovertNetwork-1658, Xlogin, and Quad7.
While attribution is ongoing, SecurityScorecard’s preliminary analysis suggests similarities between this botnet’s techniques and past actions attributed to Chinese cyber-espionage groups.
Steps to be taken to mitigate botnet attacks:
- Monitor Non-Interactive Sign-In logs to detect unauthorized attempts.
- Continuously scan for leaked user credentials on the dark web and set monitoring services to track their activities.
- Enable password resets and session invalidation when an account is compromised.
- Automated alerts for rapid response.
- Proactive monitoring and swift containment for defending large-scale botnet-driven threats targeting M365 environments.
- Monitor and assess your software supply chain for vulnerabilities.