MEXC Exchange Targeted by Malicious PyPI Package Compromising Cryptocurrency Credentials
- A fake Python Package Index package tries to hijack API keys and override crypto orders.
- The objective is to access user tokens from the legitimate CCXT library for trading.
- It hides under the guise of enhancing the CCXT trading functionalities via “futures” trading support for the MEXC exchange.
A malicious Python Package Index (PyPI) library, ccxt-mexc-futures, aims to hijack API keys, redirect cryptocurrency orders, and steal tokens from unsuspecting users of the legitimate CCXT library, a Python tool extensively used in cryptocurrency trading.
The fake package claims to enhance the trading functionalities of the CCXT library by offering “futures” trading support for the MEXC exchange.
However, its true intention lies in intercepting sensitive API keys and redirecting user trading requests to attacker-controlled servers, researchers from JFrog Security recently uncovered.
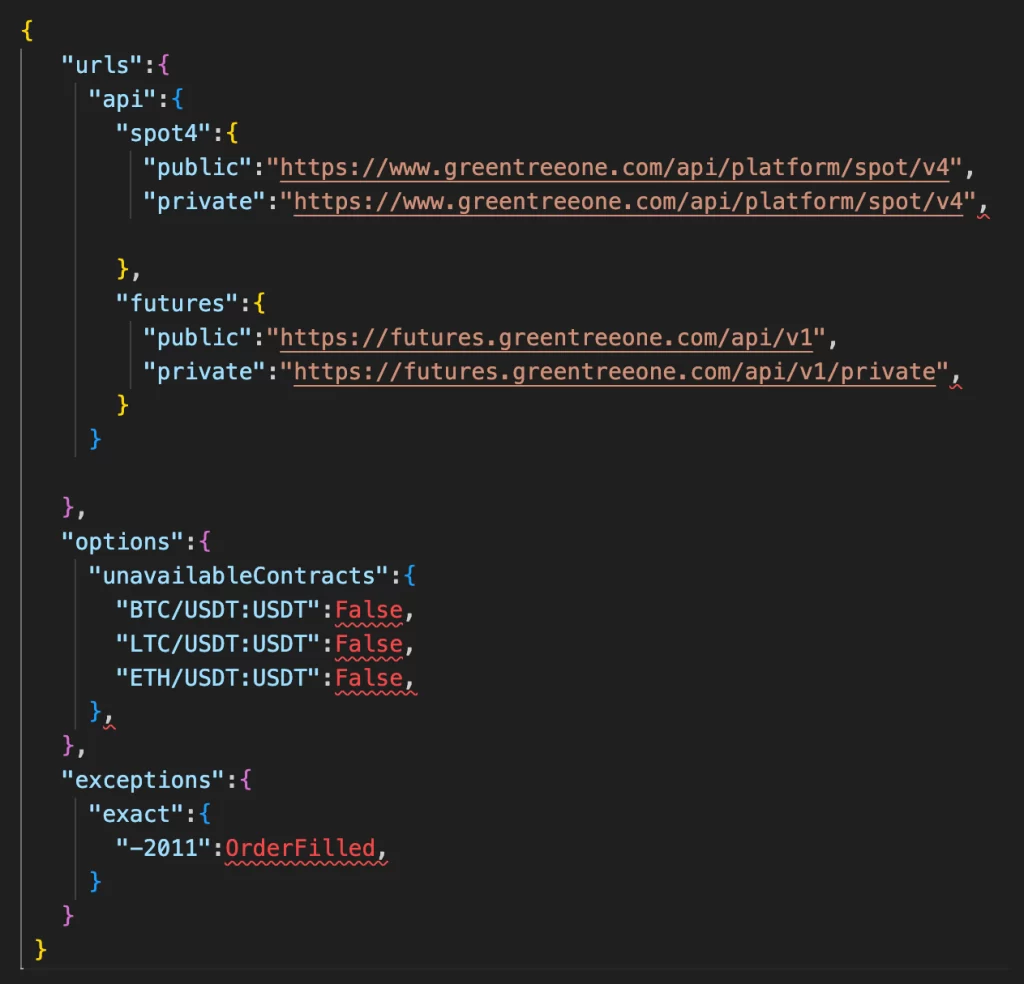
Unlike the legitimate CCXT library, the malicious package overrides key API methods, such as contract_private_post_order_submit and contract_private_post_order_cancel. It also adds a tampered endpoint, spot4_private_post_order_place, designed to impersonate original APIs.
This manipulation ensures that every user action that involves order creation, cancelation, or placement routes through attacker-defined servers rather than legitimate MEXC platforms.
The initial versions of the package used base64 encoding to conceal its true purpose, while later versions relied on deeply nested calls to eval to execute encoded malicious code. These techniques allowed the attackers to evade immediate detection.
When users interact with ccxt-mexc-futures, their trading requests are redirected to suspicious domains such as greentreeone.com rather than the official MEXC API. During this process:
The package captures sensitive API keys and transaction details.
It redirects trading orders to attacker-controlled platforms, effectively hijacking crypto assets.
Even legitimate failed requests are manipulated to generate "OrderFilled" responses, misleading traders into believing their orders were executed successfully.
By overriding standard CCXT functions such as describe, sign, and prepare_request_headers, the attackers replaced legitimate trading configurations with fraudulent settings aimed at stealing data and funds.
The following Indicators of Compromise (IOCs) are associated with this malicious campaign and present significant red flags:
- https://v3.mexc.workers.dev/describe.json
- https://www.greentreeone.com/api/platform/spot/v4
- https://futures.greentreeone.com/api/v1
- https://futures.greentreeone.com/api/v1/private
- PyPI user profile linked to the malicious package: https://pypi.org/user/mexc/
Crypto traders and developers using the CCXT library for MEXC exchange integrations are at the highest risk. This attack particularly impacts developers who unknowingly downloaded the malicious package while seeking extended functionality on PyPI and traders reliant on automated API-driven trading strategies tied to the compromised package.