Medusa Extorts Construction Service Provider O’Shea Builders Demanding $350,000 in Ransom
- The Medusa ransomware group named O’Shea Builders, a construction service provider in Central Illinois
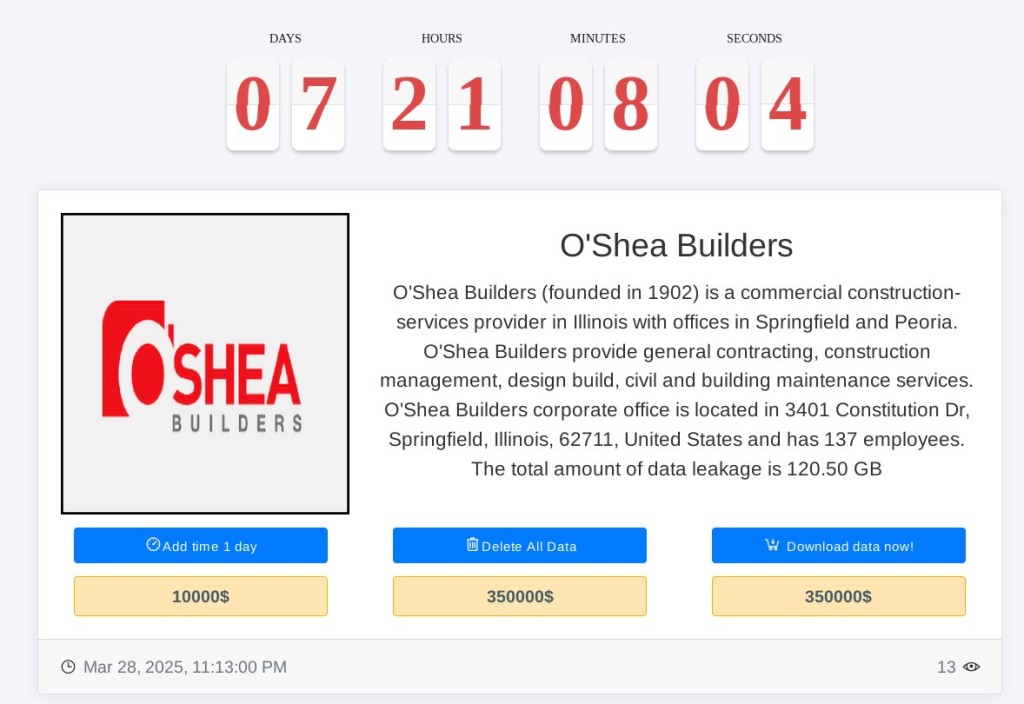
- They demanded a ransom of $350,000 to be paid in 7 days and an additional $10,000 for extending the deadline
- The group exfiltrated 120.50 GB from the company's systems and posted samples as proof
A leading construction company in Central Illinois has been named a victim by the Medusa ransomware group. They demanded a ransom of $350,000 with a 7-day deadline to make the payment.
They allegedly exfiltrated 120.50 GB of data from O’Shea Builders.
The threat intelligence platform Dark Web Informer posted the above screenshot and stated Medusa disclosed sample files as proof of the data breach.
The samples included spreadsheets, diagrams, and invoices among other file types. Medusa also made bargain offers to increase the payment deadline by a day. They demanded an additional $350,000 each to delete all the data without leaking or downloading all the information immediately.
TechNadu approached the construction services provider for a statement. We will update this report after receiving a response.
Medusa was discovered in June 2021 and has since been actively exploiting organizations. The group follows a double-extortion tactic by exfiltrating the company’s data and threatening to publicly release it if the ransom is not paid.
They use Telegram for communication and leaking stolen information. The ransomware-as-a-service variant has targeted over 300 companies however, is unrelated to the MedusaLocker variant, a joint CISA advisory noted.
Keeping the increasing number of cyber-attacks by Medusa impacting critical infrastructure sectors in mind, the FBI, CISA, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint advisory this month.
The advisory detailed the mitigation techniques, the tactics, techniques, and procedures followed by the group, and the indicators of compromise to help organizations stay alert and prevent threats.