McAfee Products Vulnerable to Self-Defense Bypassing Attacks
- Three McAfee security products have been found to be vulnerable to system-takeover attacks.
- The attack method is similar to what we’ve seen on other products recently, based on the absence of digital signature validation.
- Users are advised to update their products immediately, with a fix coming three months after the discovery.
SafeBreach Labs and their security researcher Peleg Hadar, pull one more out of their drawer, and this time it concerns three McAfee products, the Total Protection, Anti-Virus Plus, and the Internet Security. The problem with these products is a common vulnerability (CVE-2019-3648), which enables an attacker to bypass McAfee’s self-defense mechanism and achieve defense evasion and persistence. The method is similar to the one that we discussed previously regarding the HP Touchpoint Analytics, the Trend Micro Password Manager, and the BitDefender Antivirus 2020 Free.
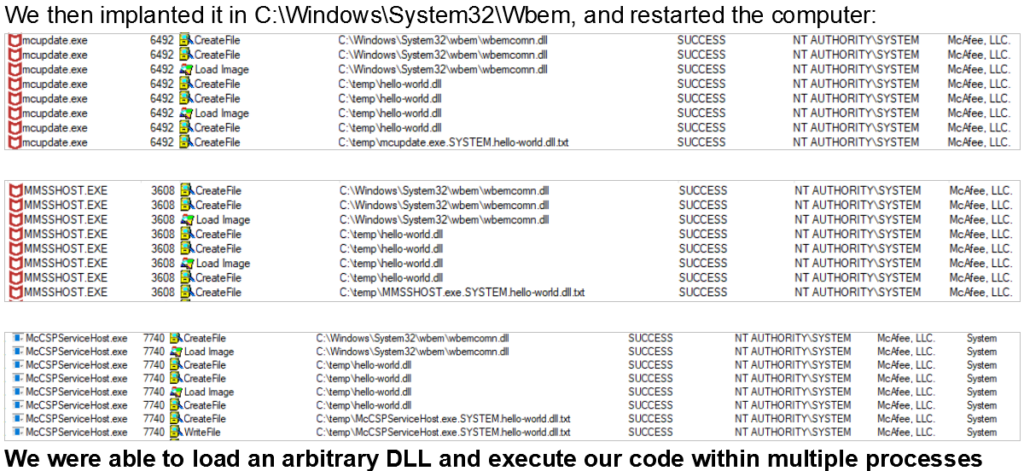
For those of you who don’t remember, it is an attack based on the loading of an arbitrary unsigned DLL into services that run as “NT AuthoritySystem”, which gives the actor powerful permissions on the target system. SafeBreach has developed the proof of concept code and was able to load an arbitrary DLL that opened the way to executing multiple processes that are signed by McAfee. This essentially bypasses the self-defense mechanism of the software. As we saw in the other cases of this kind, the main problem here is the absence of digital signature validation made against the binary. The DLL that the actor is trying to load should be validated, but it isn’t.
This attack may result in the execution of payloads every time the McAfee services are loaded, which would cause an enormous headache to the victim. To avoid dealing with such a complicated scenario, make sure that you grab the version 16.0.R22 Refresh 1 that McAfee released today, fixing the vulnerability. The company was informed of the details of this attack on August 5, 2019, confirmed it on September 3, 2019, and provided the fixing timeline on October 8, 2019. This may not seem like a speedy resolution of the problem, but considering how many products McAfee handles and that this flaw affected three of them, there was a respectable amount of investigation that had to take place.
As for what else is on the revelation pipeline of SafeBreach, we already have a similar report on our hands about another reputable vendor. Due to ideological barriers, we can’t disclose which product it is right now, but we will on November 15, so stay tuned. Until then, make sure to update your software and operating system, apply all available patches as soon as possible, and try not to expose yourself to unnecessary online risks.
Do you trust McAfee products for the protection of your systems? Share your thoughts and experience with us in the comments down below, or on our socials, on Facebook and Twitter.