“Maze” Ransomware Adopts the “Ragnar Locker” VM Wrapping Trick
- "Maze" is now using virtual machine files wrapped in Windows installers to deliver its payload.
- This method was first spotted on "Ragnar Locker", but Maze has evolved it to become more capable.
- It is clear that VM is now becoming a widespread detection evasion method, so security solutions need to adapt accordingly.
The "Maze" ransomware, one of the most catastrophic groups of malicious actors right now, has adopted a detection evasion technique that involves wrapping the payload in a stripped-down virtual machine. This is the same technique that we saw back in May by "Rangar Locker", and its success in hiding from endpoint security solutions has convinced Maze to take note. Whatever these actors can do to increase their chances of success, it's a good move, so using virtual machines is a necessary complication for them.
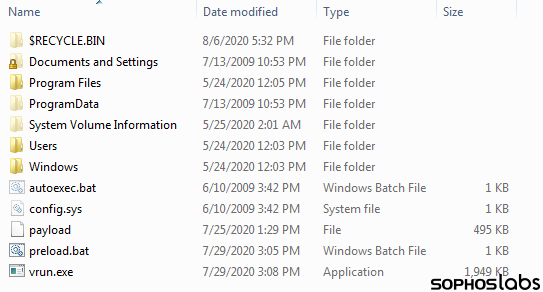
The relevant report comes from Sophos, the same team of researchers who had discovered the Ragnar Locker trick a few months ago. As they detail now, Maze actors used a VirtualBox disk image file (.vdi), which was delivered by a Windows installer file (.msi). Contrary to Ragnar Locker's choice, which was Windows XP, Maze's virtual machine is running Windows 7 SP1. Further analysis by the researchers showed that Maze was present on the compromised network for six days before they eventually delivered the ransomware payload.
Source: Sophos
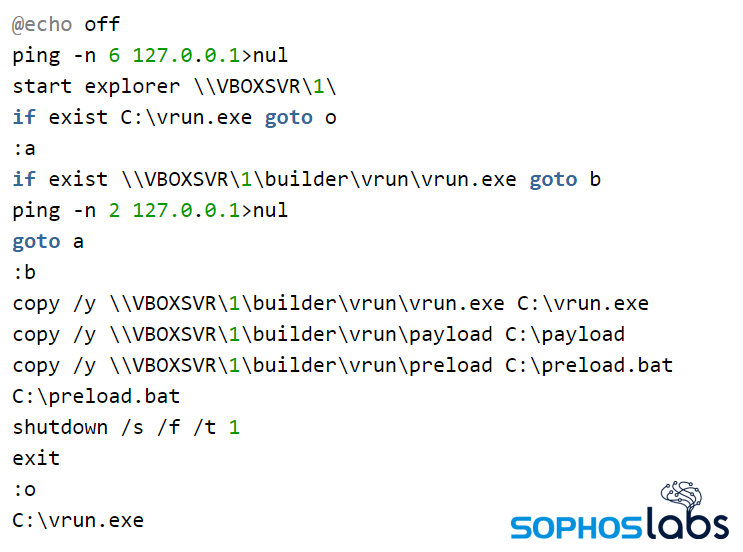
The attackers attempted to create scheduled tasks that launched the ransomware, and which they named as "Windows Update Security" and "Windows Update Security Patches". The payload itself was named "license.exe", so all in all, the hackers tried their best to do the "basic stuff" right. They even executed a script that disabled the real-time monitoring system of Windows Defender. The time of the scheduled task was set to midnight in the local time zone of the penetrated systems so that the chances of success increased even more.
Source: Sophos
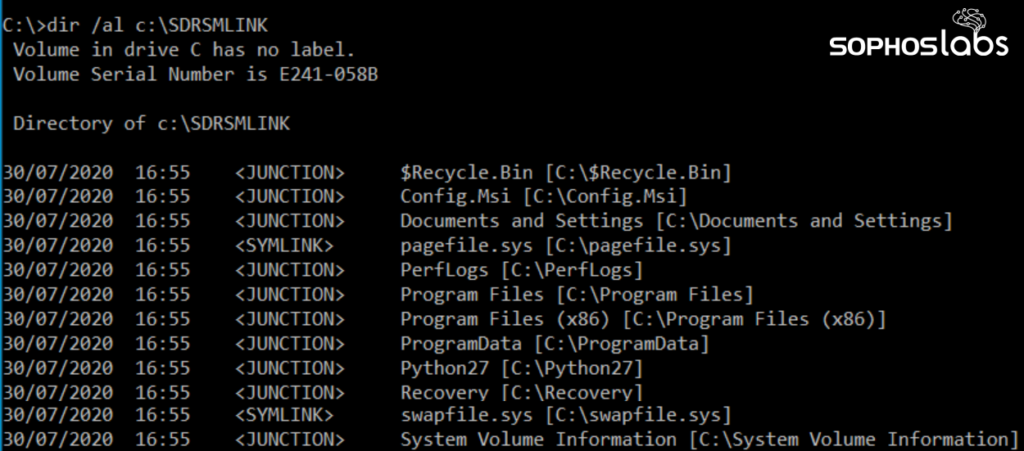
The six-day delay mentioned previously is that the virtual machine is configured based on parameters that relate to the victim's network. For example, the "micro.xml" file maps the drives used as shared network drives in the target network, a prerequisite for effective encrypting action. One difference between the Ragnar Locker and Maze's approach is that the latter can launch the attack from within the virtual machine, although this requires significantly larger VDI, payload, and MSI installer file sizes.
Source: Sophos
Seeing Maze using the VM trick is a ringing bell for AV developers and endpoint security solution providers. This detection evasion technique is now being adopted by more actors, so defending against it is a new requirement that arises from the situation. For a full list of the indicators of compromise as these were collected and confirmed by Sophos, you may check out this GitHub page.