Masslogger Trojan Campaigns Oomph Their “Mass” Aspect
- New Masslogger trojan campaigns can steal user credentials from a wider set of applications.
- The infection begins with a tricky email that plants a malicious HTML file on the victim’s system.
- Through obfuscation and volatile memory reliance, the actors achieve good levels of detection avoidance.
Researchers at Cisco Talos warn about the evolution of Masslogger trojan campaigns, as threat actors are bettering their obfuscation, detection evading, and credential harvesting methods. Also, the targeting scope is constantly widening, collecting sensitive info from an ever-increasing number of potential targets.
As Talos analysts explain, the most notable problem in the field right now is a new variant of the “Masslogger” trojan, which is capable of retrieving user credentials from multiple sources, including Microsoft Outlook, Google Chrome, and various instant messenger apps.
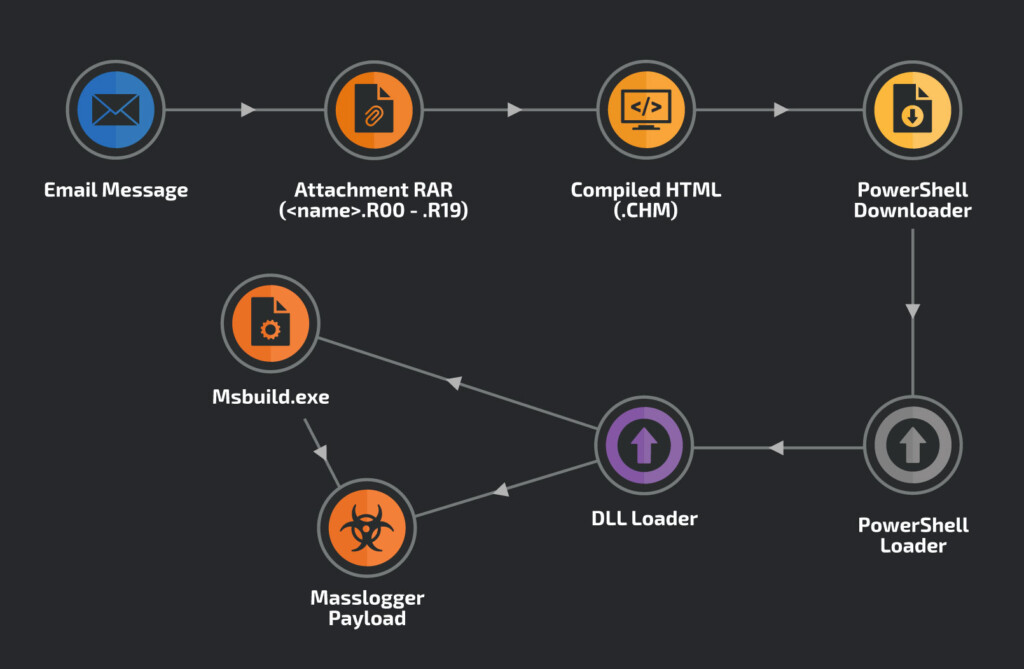
First of all, the new Masslogger trojan is using a compiled HTML file to get the infection chain rolling. The file contains malicious JavaScript, which launches the malware process and arrives via a suspicious email with a business-related topic.
The email contains a RAR archive file, which in turn contains the HTML. Upon launch, the JS runs to load a PowerShell script, which deobfuscates into a downloader, fetching the main loader. These are hosted on compromised hosts that are otherwise legitimate, so in general, the victim is unlikely to see any security alerts.
The main payload is a new variant of the Masslogger trojan, which is written in .NET and can steal user credentials from the following applications:
- Pidgin messenger client
- FileZilla FTP client
- Discord
- NordVPN
- Outlook
- FoxMail
- Thunderbird
- Firefox
- QQ Browser
- Chromium-based browsers (Chrome, Chromium, Edge, Opera, Brave)
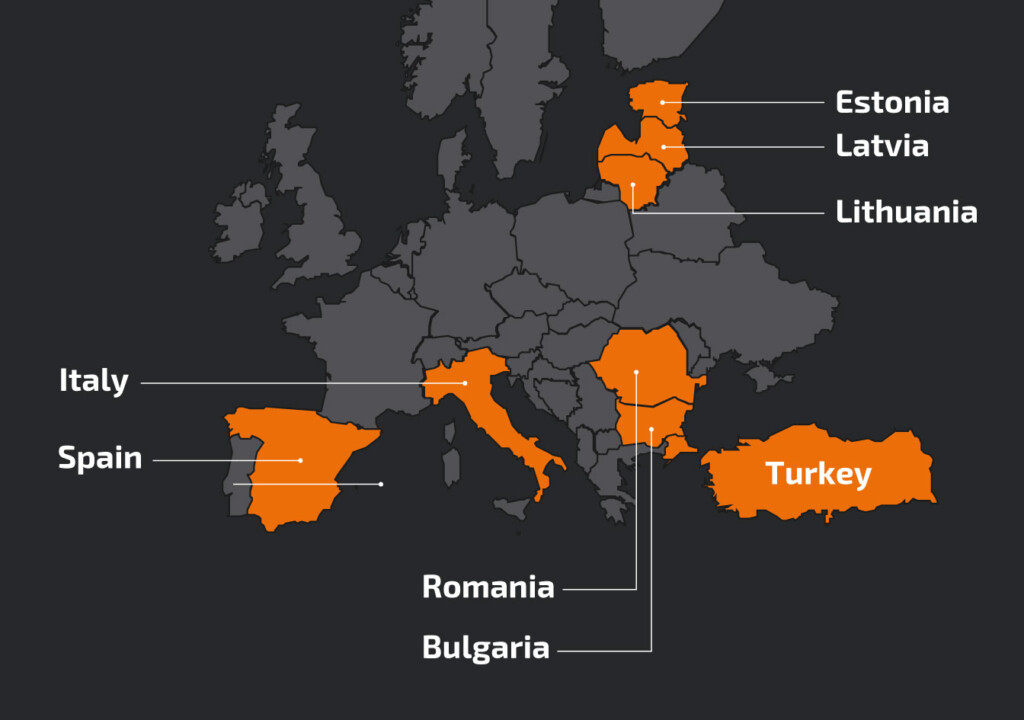
The latest campaigns seem to target mostly European countries, including Italy, Latvia, Turkey, Bulgaria, Lithuania, Hungary, Estonia, Romania, and Spain. However, the targeting scope may widen at any time, as all that the actors need to do for that is to create and use new phishing emails written in the targeted locales.
Because the current campaign isn’t planting any components on the disk, except for the HTML file, they manage to evade detection very effectively. Everything takes place in volatile memory, and not many people care to run background memory scans to identify malicious processes.
What users can do to protect from these risks is to configure their systems to prevent PowerShell script execution. Of course, treating incoming emails with extra care would also be key in this case - and in most cases of this kind.