Massive “Terracotta” Scam Operation Uncovered on the Android Space
- An ad-clicker malware for Android has found its way inside 65,000 devices, generating billions of fake impressions.
- The authors of the malware disseminated it via fake apps that promised sneakers giveaways.
- The malware is characterized by advanced features, mostly around detection evasion.
When it comes to “Free / Giveaways,” you can always safely assume that they’re either scams or just looking to collect your email address for marketing or plain spamming. In the case of the “TERRACOTTA” operation that happened on the Android ecosystem, researchers of the Satori threat intelligence team discovered that it is the former case with an additional sprinkle of an ad-clicking malware.
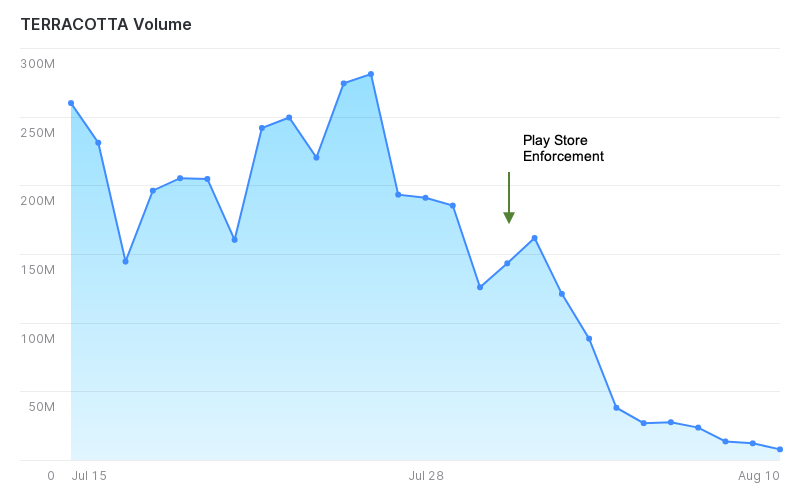
The operation involved 65,000 unwitting participating devices, spoofed 5,550 Android apps, and generated 2.4 billion fraudulent bidding requests.
Source: WhiteOps
The lure was simple yet effective. Users browsing the Google Play Store were urged to download an app, fill their details (name, address, shoe size), select a pair of sneakers, and have them mailed to their house for free in about two weeks. No hidden fees, no charges, and no suspicious requests. Just download the app and get the sneakers delivered on your doorstep.
Instead of shoes, though, the victims got a malware payload delivered on their devices, often staying dormant for two weeks before it activated. What this particular malware does is to generate fake ad impressions, so the app authors’ goal is to make money through ad-click fraud.
Source: WhiteOps
Until the last week of June 2020, when Terracotta seized operations, it had generated 2.4 billion impressions from 65,000 devices that bit the shoe lure. Terracotta was able to spoof its traffic to avoid detection and used a custom Android Web View to render the ads. Also, Terracotta contains a probabilistic model in its code, to manipulate the Chrome web browser version to make the traffic appear as it comes from v80.
Finally, Terracotta sports bot mitigation defenses through an advanced tag evasion system, essentially blocking the loading of content from ad-verification domains.
Source: WhiteOps
The end of the operation came when Google removed the fake apps from the Play Store, so from that moment and on, the actors could rely only on the existing installations and unofficial APK sources. WhiteOps has provided a list of 40 spoofed apps that distributed the Terracotta malware, so go ahead and check that list now.
Of course, there have been a lot more apps carrying the ad-clicker, but these 40 were the most widely downloaded. Next time you are met with a promise of something for nothing, think about the chances of it being legitimate. However you see it, they are zero.
Read More:
- Hackers Use Malicious 3ds Max Plugin for Cyber-Espionage
- At Least 1,200 iOS Apps Constitute a Privacy Risk for Users
- New QakBot Campaign Is Showcasing Novel Detection Evasion Techniques