Massive “Malsmoke” Malvertising Campaign Keeps Going for Months
- “Malsmoke” continues to plague adult sites even months after it was first reported.
- The actors behind the malvertising campaign have now passed to social engineering using fake Java download requests.
- Thousands are tricked, getting infected with Zloader malware and various additional payloads that come with it.
A sizable malvertising campaign called “Malsmoke” continues its operation by evolving and optimizing its methodology. According to a Malwarebytes report, the actors behind the particular campaign have been active since the beginning of the year, targeting highly popular adult websites like “bravoporn” and “xhamster.”
In September, a surge in malvertising activity was recorded. By mid-October, the actors passed from using exploit kits for delivering malware to setting up social engineering schemes, which opened up their targeting to a much wider scope.
“Malsmoke” isn’t your average malvertising campaign in the sense that it remains present on high-traffic portals like “xhamster” for months, managing to fly under the radar and trick thousands of visitors throughout extended periods of time. The researchers have noticed that in November, the actors have added new decoy sites like “pornislife[.]online/B87F22462FDB2928564CED” and “pornguru[.]online/B87F22462FDB2928564CED”.
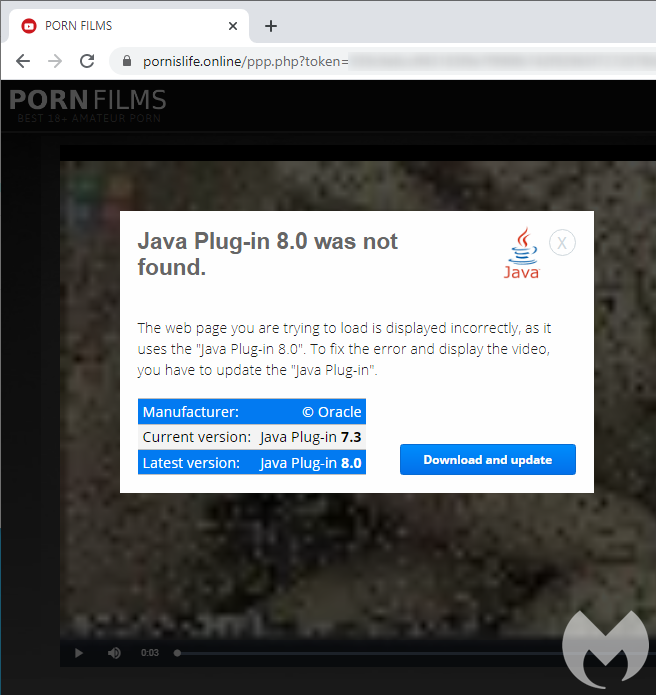
The trick used by the actors here is simple. The user is led to believe that a video they’re looking for is available on these decoy sites and is asked to download and install a supposed Java update.
A pixelated video even plays for a few seconds with sound in the background before a message is overlaid to inform the user that the “Java Plug-in 8.0” - which is allegedly required for the playback - was not found on the system.
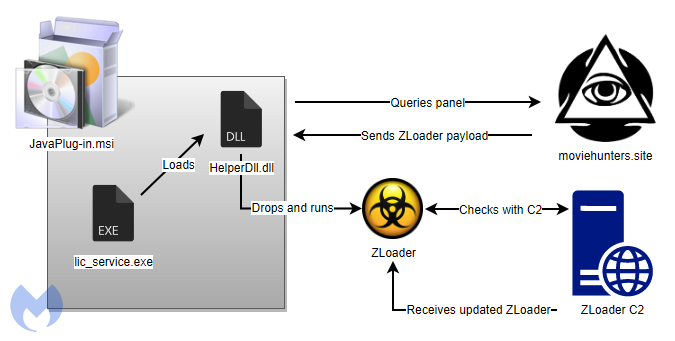
What the download really drops onto the victim's machine is the Zloader malware, which is then injected into a new “msiexec.exe” process and establishes communication with the C2 (at least 10 domains were identified) via DGA. From there, additional modules can be fetched, giving actors the capacity to steal browser cookies, banking login credentials, email passwords, and more.
Notably, the MSI file used as a decoy for the fake Java update is digitally signed, and the majority of the installer’s contents are legitimate. This definitely plays a big role in managing to get past many AVs during the installation process.
If you are ever met with a Java plugin request while browsing online, consider it almost certainly an attempt to infect you with malware. Java used to be a necessity back in the day, but right now, and especially for browsing the internet and playing any media on your web browser, it absolutely isn’t.