Massive Database Belonging to ‘Fractal Analytics’ Offered for Purchase
- A hacker who spotted a misconfigured Cassandra instance is selling the exfiltrated data on a forum.
- The database belongs to ‘Fractal Analytics,’ a marketing and targeted advertising data analytics firm.
- The seller claims that the firm hasn’t realized anything and that the cluster remains accessible.
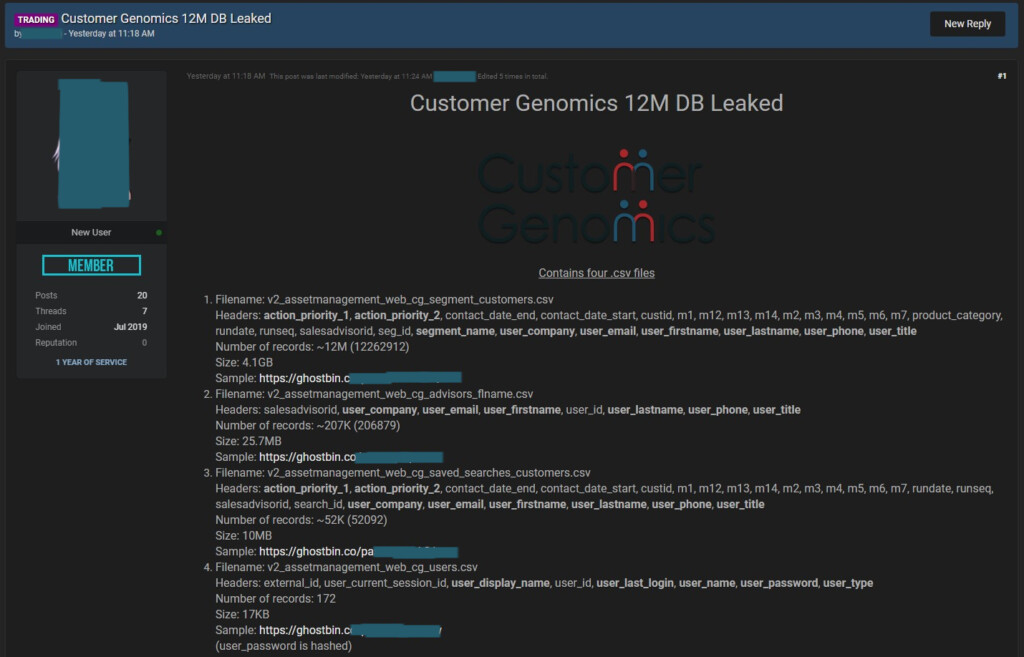
A hacker was able to obtain a database containing 12 million entries that belongs to ‘Fractal Analytics,’ an international artificial intelligence company based in New York. The database is branded after 'Customer Genomics,' a trademark of Fractal Analytics dedicated to integrating enterprise, geo-location, and open social media data to deliver personalized and contextual offers in real-time on mobile platforms. All in all, this is a marketing and targeted advertising analytics platform, and the data that it uses appears to involve full names, email addresses, phone numbers, and more.
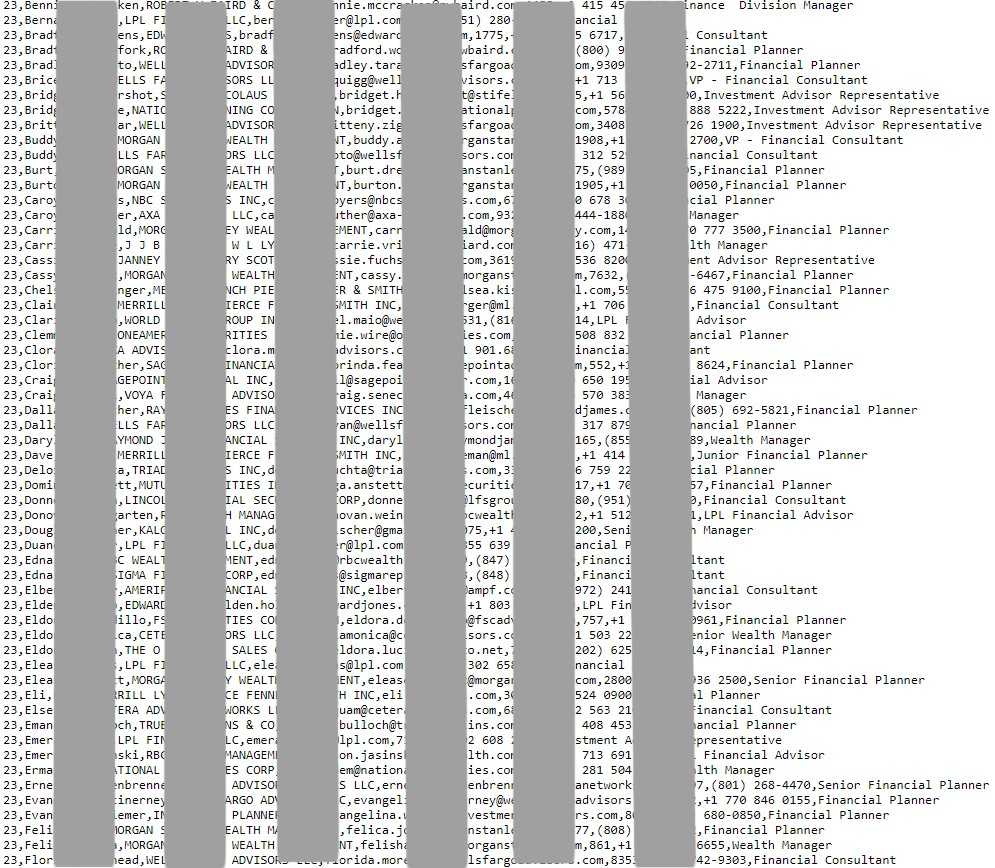
The seller is giving away four samples of the database in CSV form to prove the claims made in the listing. The typical assurances about the freshness of the data are also included (the compromise date is May 2021).
We have taken a look at the content of some of these samples, and the information in there appears to be valid. We were also able to see job titles, and in some cases, there are pairs of credentials, albeit with hashed (base64) passwords. This detail tells us that the entries don’t concern only marketing targets but also users of the platform, either employees of Fractal Analytics or their partners/clients.
TechNadu has contacted the seller directly to ask for more details about the breach, and the hacker told us that the leak originated from an exposed Apache Cassandra instance. In total, the seller claims to be holding 12 million entries corresponding to unique individuals, totaling a size of 3.83 GB. The asking price is either $100 or a trade with other databases of equal value. The hacker also told us that Fractal Analytics is almost definitely unaware of the breach, as access to the exposed cluster is still open for anyone.
We have reached out to Fractal Analytics to comment on this, but we haven’t heard back from them yet. Considering that we’re already well into the weekend, the company may not respond with a comment and data securing action until Monday - and so hackers scanning for exposed instances will have ample opportunity to exfiltrate those 12 million entries for themselves.
Unfortunately, this is not the first time that we see a marketing analytics firm holding the data of millions exposing it through an unprotected server access blunder. Some impressive recent examples of similar incidents include the database leak of Tetrad back in February 2020 that exposed 120 million Americans, the exposure of the details of 200 million property owners in the U.S. that appeared online in March 2020 and remained accessible for a full month, and the massive exposure of 1.2 billion individuals after OxyData misconfigured its Elasticsearch server and let out 4TB of sensitive data.