New ‘Man-in-the-Disk’ Android Vulnerability Affects Via External Storage Devices
- Researchers from Check Point Team revealed an Android vulnerability caused via external storage devices.
- Use of external storage devices like SD cards, USB OTG drives can lead to malicious apps being installed on your Android device.
- The infections occur as the core Android Sandbox protection does not work on external storage devices and is limited to devices memory only.
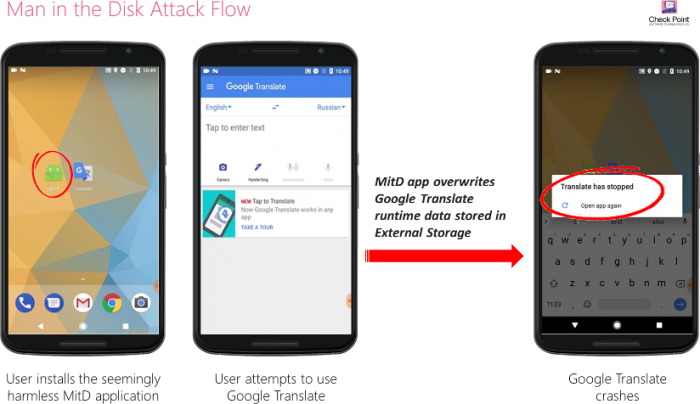
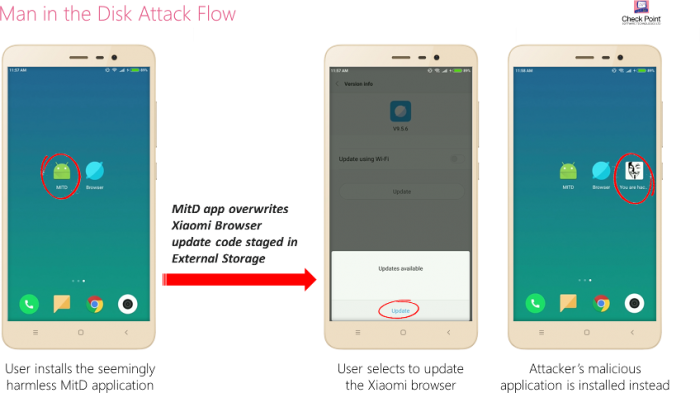
Security research company Check Point revealed a new vulnerability that can affect any Android device that is capable of using external storage devices. Google’s OS has a Sandbox protection protocol in place that constantly monitors device activity and prevents all known malicious apps from affecting devices. However, with the ability to connect to external storage devices like SD cards, partitioned internal storage, USB OTG cables, hard drives and other storage devices the Sandbox protection does not work on said external devices. The security team at Check Point has termed the method ‘Man-in-the-Disk’.
Image Courtesy of Check Point
The security flaw can potentially allow cybercriminals to conduct various malicious activities which can result in the installation of unrequested apps, denial of service, forced file encryption, crashes, ransomware and more. While some manufacturers offer non-expandable storage, a large number of Android users have access to phones and tablets that offer SD card support making most devices vulnerable. Most apps install on internal storage by default but some memory hogging apps and games install a large part of their data on external partitions.
Image Courtesy of Check Point
According to the research team, attackers who take advantage of the Android exploit can “Monitor data transferred between any other app on the user’s device and the External Storage, and overwrite it with his own data in a timely manner, leading to the unwelcome behavior of the attacked application”.
After discovering the application vulnerabilities in several Android apps, the developers were contacted. Updates to the vulnerable apps have already been released by developers, and several unnamed apps are still being patched and their names will be revealed after the process is complete. Until Google patches Android’s underlying problems, app developers need to be careful about using external storage for apps.
What do you think about Check Point’s findings? Let us know in the comments below. Also, to get instant tech updates, follow TechNadu’s Facebook page, and Twitter handle.