Malware Authors Now Focus on the Emerging Apple Silicon ARM Architecture
- The first malware written specifically for the M1 chip is out there, already having infected macOS users.
- The particular finding is just annoying adware, but more nasty stuff will pop up as time passes.
- For malware authors, native execution currently brings a set of important advantages.
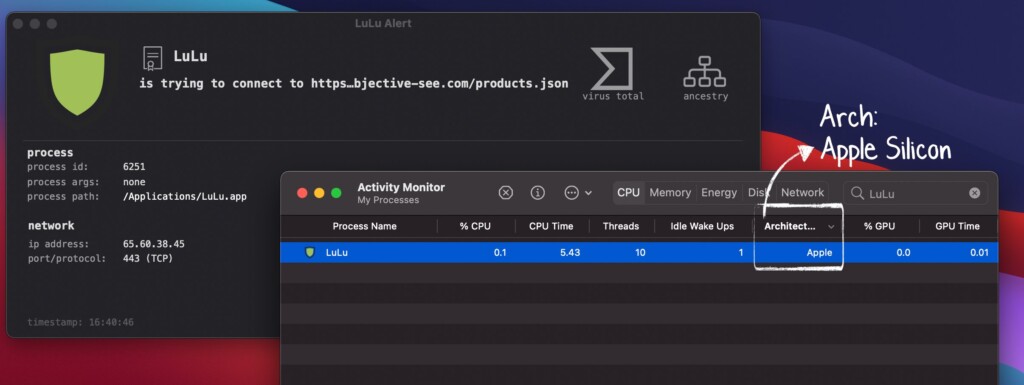
The days when your M1 Macbook is safe from malware threats will soon be history, as authors of malicious tools are turning their attention to the emerging ARM platform by Apple. As security researcher Patrick Wardle reports, the first M1-optimized malware has been spotted in the wild, so it has already begun.
Called “LuLu,” the particular malware runs natively on Apple Silicon by supporting the arm64 instruction set. This means LuLu doesn’t need to pass through Rosetta for a translation from x86_64, which is something that would complicate the infection process.
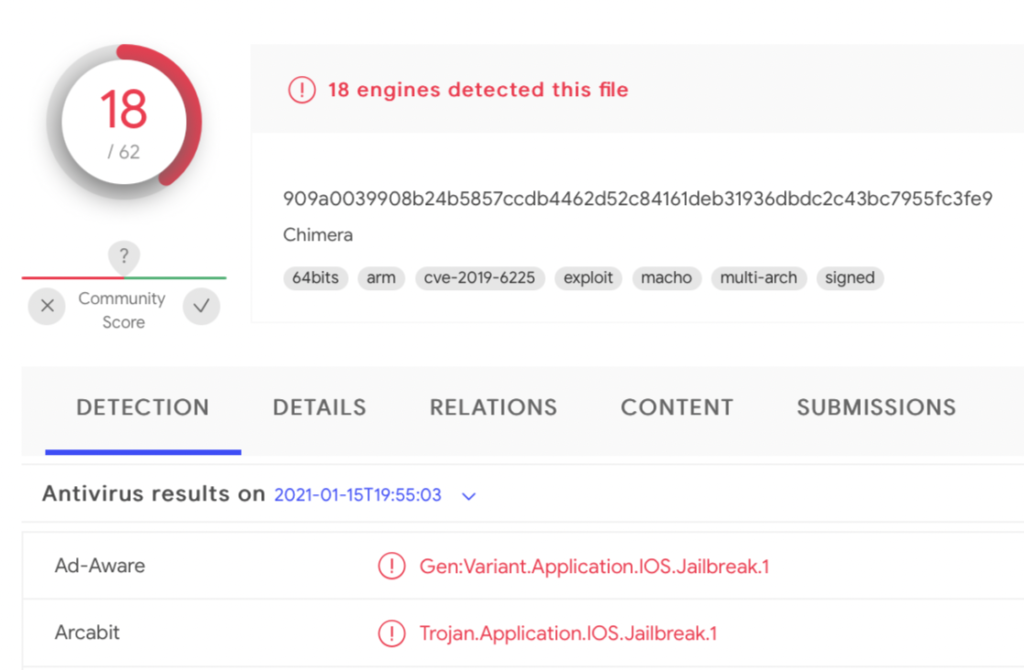
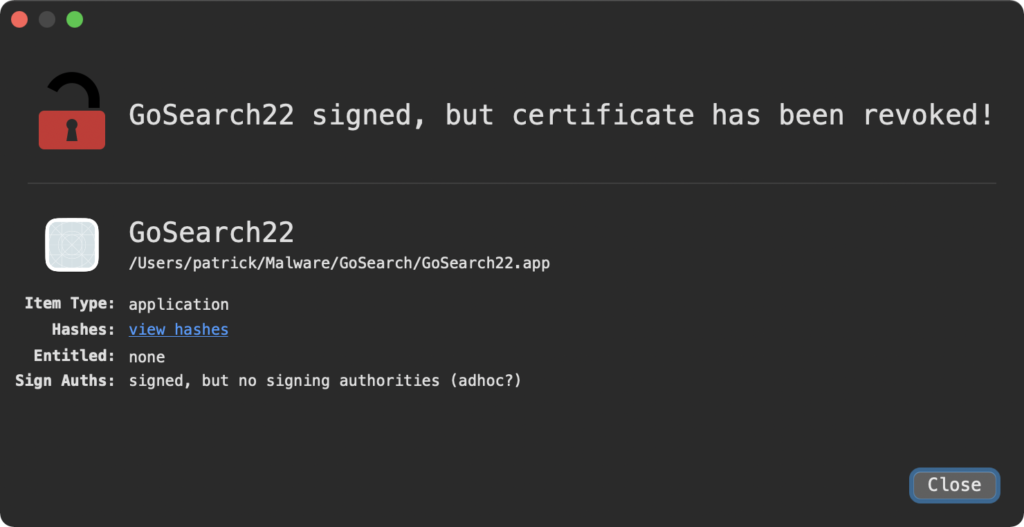
LuLu checks if it runs in a virtual machine, and if not, it launches its malicious activities. These are mainly related to adware, and LuLu is planting a Safari extension named “GoSearch22” for this purpose. Upon analyzing the component, the researcher figured that it is a variation of the Pirrit adware, which is one of the most prevalent types of malware tormenting macOS users.
Besides the gain in speed and performance that the author achieves by having the malware run natively on M1 macs, and apart from reducing the complexity of having to invoke Rosetta without raising alarms, LuLu is also achieving a certain level of detection avoidance. Most static analysis tools and AV engines don’t have very sophisticated heuristic systems for arm64 binaries. While this may change in the future, right now, these binaries can fly largely undetected.
On the matter of Apple notarization, which is mandatory for macOS software, it is unknown if the author somehow exploited a bug in the process or tricked Apple’s reviewers, but the certificate has been revoked now. Whatever happened in that stage of the process, what matters is that a number of macOS users were infected.
Security through obscurity is undeniably a powerful thing. Like Linux users who can enjoy a relative peace of mind because no malware authors care to target such a small user-base, those who bought the first M1 devices will go through a period of lull.
However, the macOS platform has about ten times the number of Linux users, and they are all “great” targets in the sense that they’re a lot more open to spending money to buy products and services. From that perspective, malware authors will devote time and effort to developing tools specifically for the Apple Silicon, and it is already underway.