Malicious Wedding Invitation Campaign Distributing Tria Stealer Targets Android Users
- The Tria Stealer malware is disseminated through fake wedding invitations that ask targets to install a malicious APK.
- Victims are approached using compromised accounts via personal and group chats in Telegram and WhatsApp.
- The malware can access app notifications from WhatsApp, Google Messages, Gmail, and more for data theft.
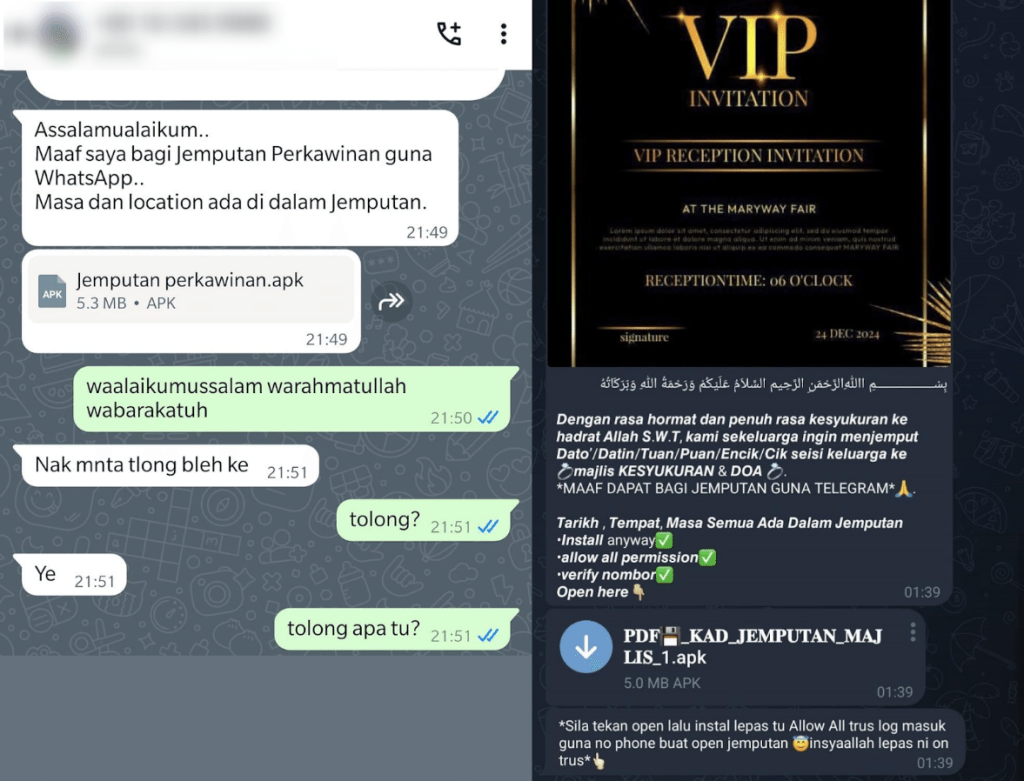
A malicious Android campaign targeting Android users lures victims with fake wedding invitation messages shared via personal and group chats on WhatsApp and Telegram, asking people to download a malicious Android app (APK), Tria Stealer.
Operating since mid-2024, this sophisticated campaign aims to gather sensitive information, including SMS and WhatsApp data, call logs, and emails, compromising victims' accounts and facilitating exploitation, according to the latest Kaspersky security report.
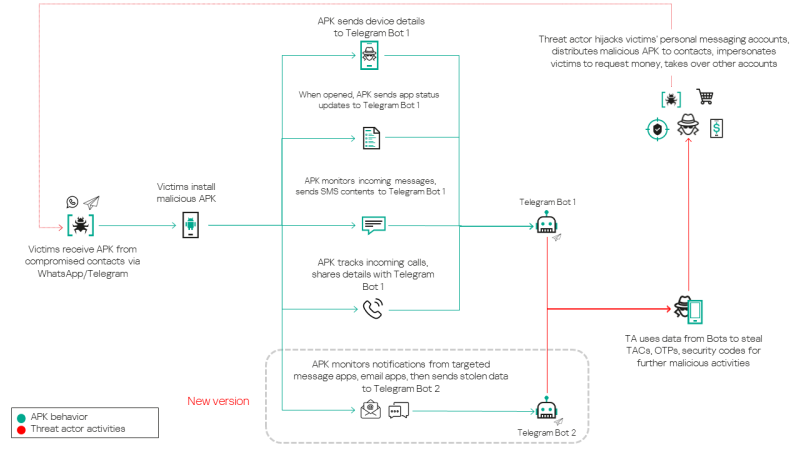
The malware can also intercept notifications to steal messages and authorization codes and exfiltrate the stolen data via Telegram bots.
The spam messages are distributed via personal and group chats in Telegram and WhatsApp, asking the receiver to download a malicious app to allegedly see the wedding invitation. Once installed, the APK requests permissions to access SMS, notifications, and other private data disguised as a legitimate system settings app.
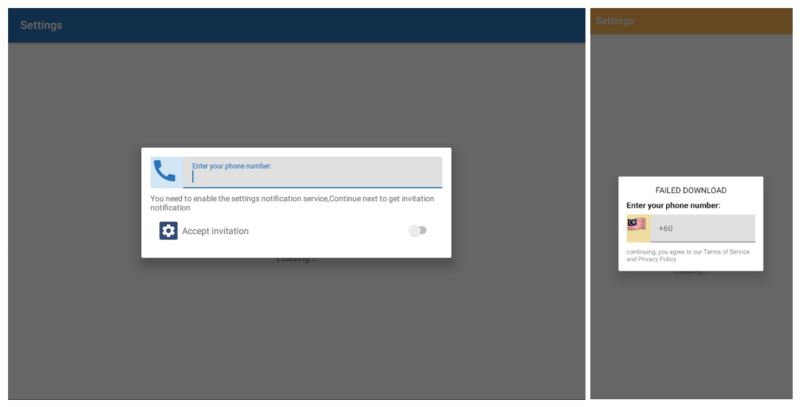
The first-time app launch verifies whether the malicious app has been used previously. If it's the initial launch, the app requests access to SMS messages, and victims are prompted to enter their phone numbers to access the invitation.
The malware contains components like SMSMonitor and CallMonitor, which intercept SMS and call activity data, including message content and sender details, call logs, and SIM slot information.
Newer variants of Tria Stealer have enhanced functionality, intercepting notifications from popular apps such as WhatsApp, Google Messages, Samsung Messages, Default MMS, Gmail, Outlook, and Yahoo Mail.
These expanded features allow attackers to harvest broader sets of data, such as notification content tied to specific apps, device details (e.g., brand and model), and victims' phone numbers.
With this information, the threat actor combines stolen data into a formatted string and transmits it via Telegram bots. Separate bots handle various data categories, such as SMS messages or app notifications.
The campaign updates include two distinct malware versions, with an evolved variant emerging in August 2024, added functionality for intercepting app notifications in newer versions, and consistent use of separate Telegram bots for different categories of stolen content.
While the campaign does not seem to focus on a specific geographical area, the most affected targets are Malaysia and Brunei. Security researchers believe the threat actor may be Indonesian-speaking based on language artifacts found in the malware and naming patterns of Telegram bots.