Malicious Coronavirus Tracking App Locks Android Smartphone Screens
- A malicious Android app promoted as a Coronavirus map tracker is, in reality, a screen locker.
- Users are tricked into granting admin access to the malicious app, resulting in a password change.
- For now, there’s a code that can unlock the affected devices, but this may soon be rendered useless.
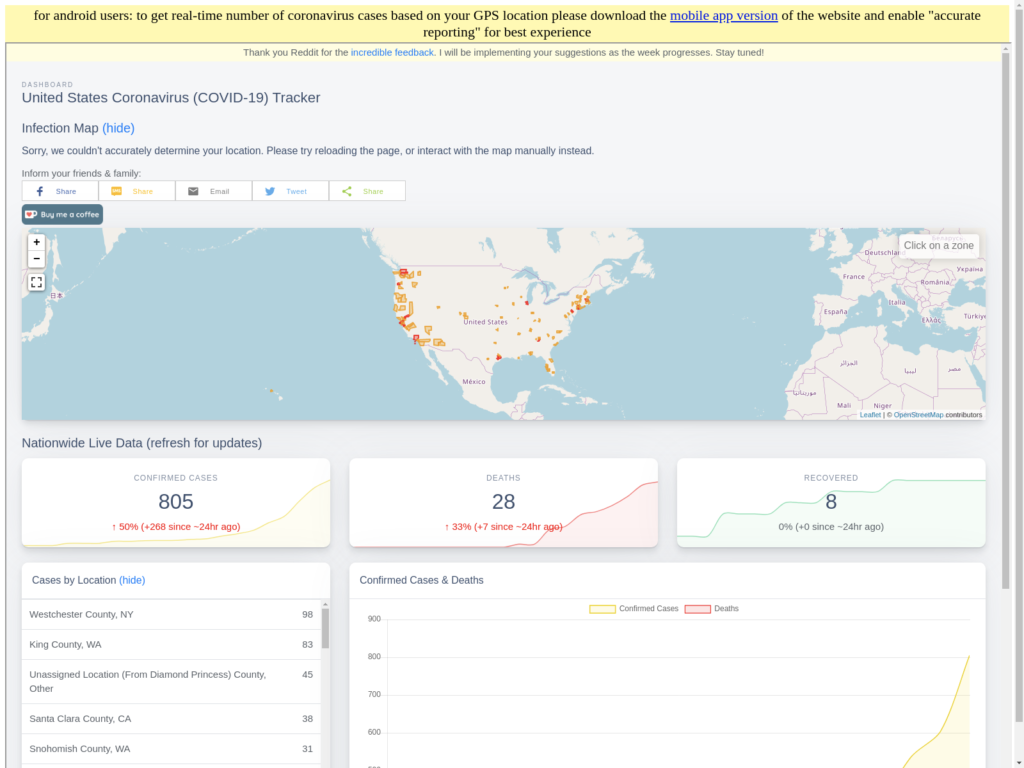
The exploitation of the COVID-19 outbreak is done on multiple levels and affects all fields, essentially making everything related to the virus outbreak risky. The latest example comes from the mobile app world. This time it’s a malicious Coronavirus infection tracking app that, in fact, acts like ransomware when installed on a smartphone. The domain that spreads the malware is "coronavirusapp[.]site," and it prompts the visitors to download an Android app that is supposedly a live map providing infection stats, and featuring heat-map visuals. What the victims will get, though, is ransomware in disguise, called "CovidLock."
Source: domaintools.com
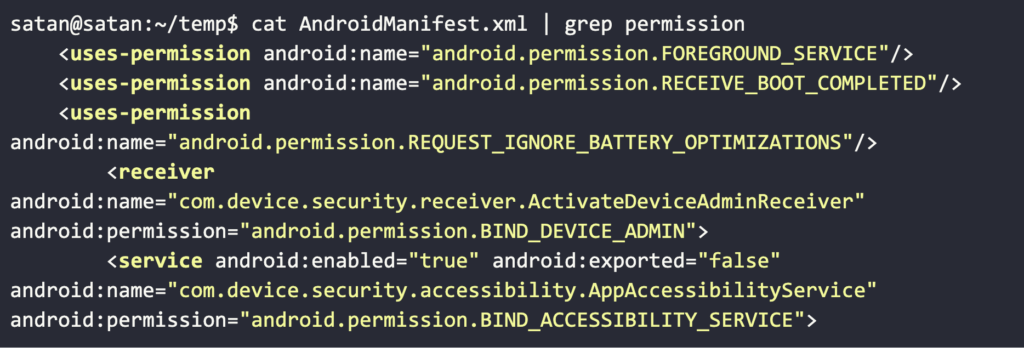
Upon installing the app, a forced password change locks the victim's phone, known as "screen-lock attack." The only thing required from the user is to grant access to the "BIND_DEVICE_ADMIN" permission. If the user tries to circumvent the lockdown by forcing a reboot, the app is launched immediately upon the system restart as it listens for the "BOOT_COMPLETED" broadcast.
Source: domaintools.com
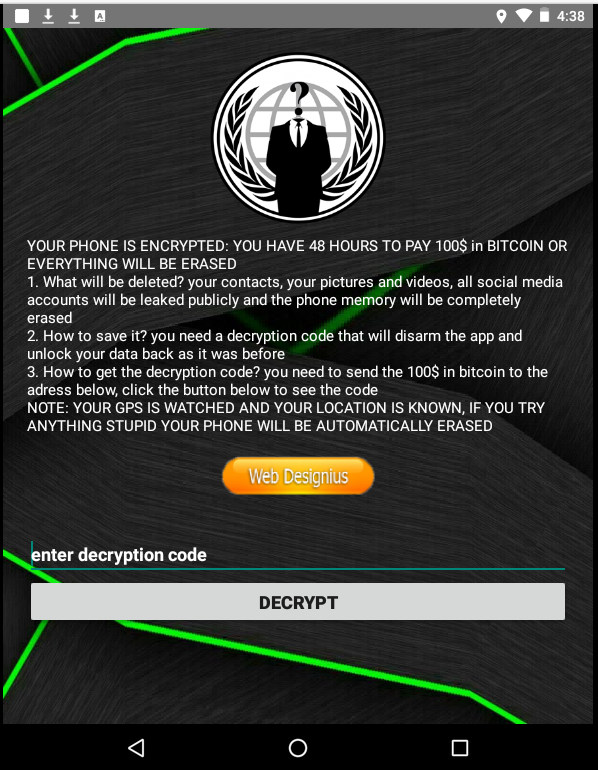
The users who got tricked have 48 hours to pay $100 in Bitcoin. Otherwise, they will supposedly have all of their files, contacts, and social media accounts irreversibly deleted. The actors also claim that they have access to the GPS sensors of the device, warning the victims that "if they try anything stupid, their phone will be automatically erased." Of course, all of this is entirely made up, and nothing other than the lock screen is real. For the time being, you can unlock it entering this code: "4865083501."
Source: domaintools.com
This key is hardcoded into the Coronavirus tracker app and was revealed after DomainTools Security researchers conducted reverse engineering on the app's code. Now, the malicious actors could respond by changing it to something else, or by even removing hardcoded keys altogether. For this reason, you are advised to avoid installing applications of this kind, as they are all coming from unofficial sources. Google has banned all COVID-19 apps from the Play Store in an effort to tackle misinformation, the spreading of panic, and essentially deal with violations of the "sensitive events" policy. Apple did the same on the App Store, so there are no COVID-19 apps that you can really trust out there.
The original domain has been taken down following its discovery and reporting. Still, the investigation that followed revealed that the particular actor has a lot more going on than just this app. The domain registrant details pointed to another website ("dating4sex[.]us)", which links to an individual in Morocco. The email used for the registration of that domain is "rolling8dice@gmail[.]com," which, in turn, ties to a list of 158 domains that have been previously linked to scamming and malware distribution campaigns.