Malicious Actors Create “Frankenstein Monsters” by Combining Open Source Components
- Actors are increasingly utilizing open source tools and components to launch effective attacks.
- The advantage is the zero cost and the inability of security firms to correlate tools with actors.
- Campaigners want to infect people with malware through the malicious macro code in documents.
Cisco Talos has identified a series of activities and made-up tools that seem to originate by the same group of malicious actors. According to the researchers’ report, the main goal of the crooks was to install malware onto the victims’ machines by using malicious documents as the wagon. The particular operations occurred between January and April 2019, and the risk is still ongoing. The reason for the “Frankenstein” name given by the researchers to this campaign is the fact that the actors combine several unrelated open source tools and components and deploy them creatively to reach their goals.
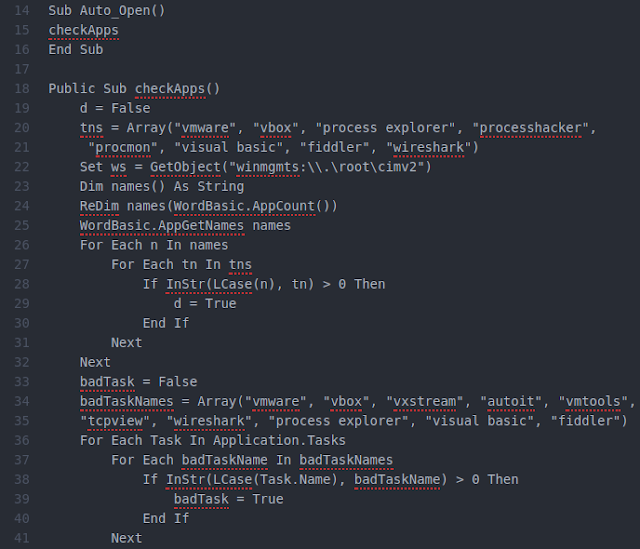
Examples of these open source and freely available components include a tool that leverages MSBuild to execute a PowerShell command, another GitHub hosted project called Fruityc2 that is used to build stagers, the “PowerShell Empire”, and an article to help the attackers detect whether their software is running in a virtual machine or not. The reason for using open source tools is not only because they are free and readily available, but also because they feature higher operational security and make the malicious activities and the group behind them harder to detect. Custom tools on the other side leave unique traces, as they are developed by specific groups of hackers.
image source: blog.talosintelligence.com
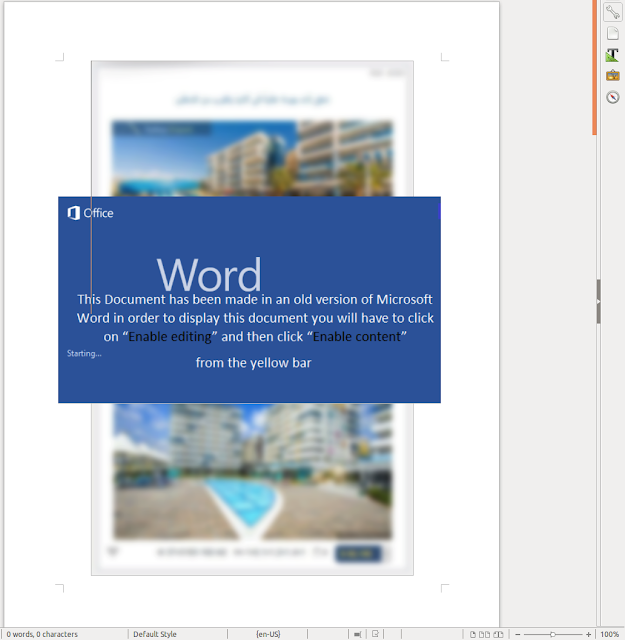
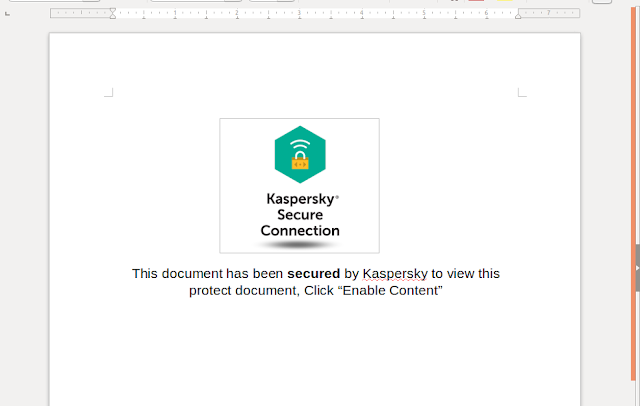
The campaign that is organized by the “Frankenstein” actors usually involves a document named “MinutesofMeeting2May19.docx”, which contains an image with the flag of Jordan. The document is exploiting the CVE-2017-11882 MS Office vulnerability to execute arbitrary code in the machine. In this case, it sets up a scheduled task named “WinUpdate” which runs PowerShell commands that serve as a stager. Other documents used in the same campaign are also displaying flags from other Middle Eastern countries, as well as logos and letterheads from governmental agencies, obviously to make the documents look important and drive the recipient to open them and enable the macros. To ease any possible suspicion, the actors even claim that the document has been secured by Kaspersky and that you’re safe to “enable content”.
image source: blog.talosintelligence.com
After checking the host machine, the malware is stealing information such as the username, the machine name, the public IP address, the user privileges, the running processes, the OS version, and the SHA256 HMAC, and sends everything to the C2 server via AES-CBC communication. As always, to stay protected against this type of dangers, don’t download and open documents that you weren’t expecting, don’t enable macros on your MS Office suite, and keep your AV, OS, and all software up to date.
image source: blog.talosintelligence.com
Have you received a document that matches the description above? What was its filename? Let us know in the comments down below, or share your story on our socials, on Facebook and Twitter.