Malicious Actors Are Extensively Using CypherIT to Package Their Malware
- Malware campaigns are increasingly relying on obfuscating crypters and malware wrappers.
- The most popular choice right now is the $33/month CypherIT, which is an anti-reverse-engineering tool.
- The crypter is periodically changing its encryption method so that AV tools cannot detect the malware.
As reported by Check Point Research, malicious actors are using a service called "CypherIT" to wrap their malware samples and benefit from high levels of obfuscation. According to the firm’s telemetry data, about 13% of all malware executables that were sent via email between August and October 2019 were packed with the CypherIT crypter. The particular tool is a perfectly legal piece of software that is meant to be used by developers who want to protect their binary files from being reverse-engineered. However, crooks love it too, as it helps them encrypt their malicious executables and avoid AV detection.
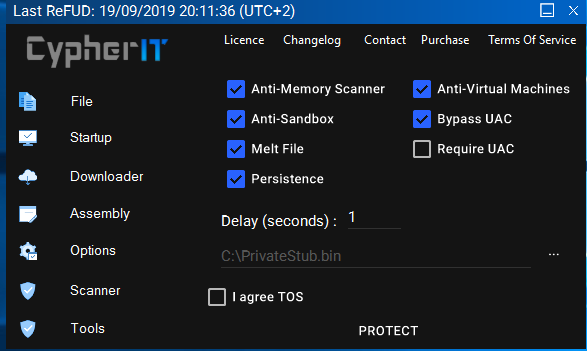
CypherIT is not only providing encryption, but also persistence, anti-sandboxing, and UAC bypassing. As it is shown in the following screenshot, the actor may comfortably select what they need via a friendly user interface and have the wrapped file ready within a couple of seconds. At a cost of $33 per month, this tool is becoming a must-use for malicious actors, as it is increasing their level of success exponentially. The whole point in malware distribution campaigns is to infect as many targets as possible, and the rate of infection is precisely what CypherIT is boosting.
Source: Check Point Research
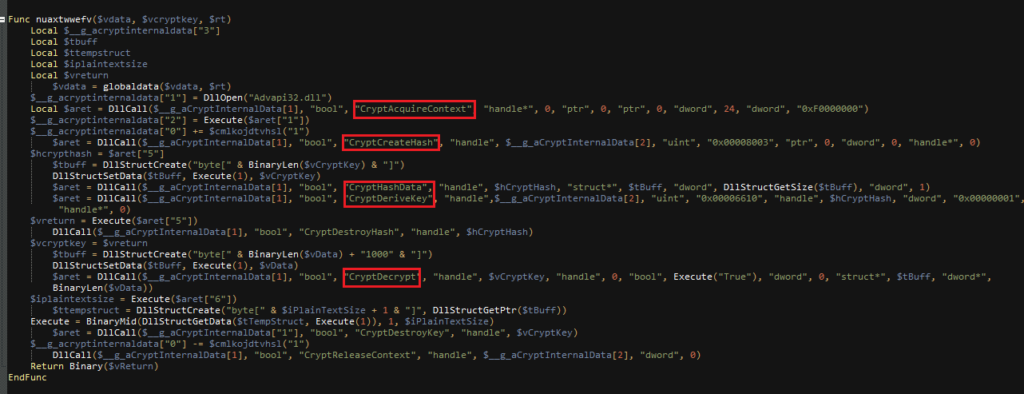
The researchers have also highlighted a rise in the use of the AutoIt scripting language, which is becoming very popular among malware writers. More specifically, 18% of all malware that was sent via email between July and September was written in AutoIt, and about 68% of all executable files shared online during the same period were malicious. CypherIT achieves obfuscation on these scripts via the following functions:
- Change the character order;
- Change the strings to hexadecimal;
- XOR with constant values;
- Rotate the strings;
- Embed many non-ASCII characters.
Source: Check Point Research
The most annoying thing for security engineers is that CypherIT is rotating its encryption methodology every now and then, which helps to make the obfuscation stronger and the detection harder. Most of the analyzed samples use the AES256 encryption algorithm, while some were found to be using the RC4 algorithm. All of this makes crypters a valuable weapon in the malware actors' arsenal, while at the same time, crooks are becoming a crucial clientele for "packer as a service" providers. Right now, Remcos, NanoCore, NJRat, AZORult, AgentTesla, NetWire, and Lokibot, are all packed with CypherIT. As this trend will continue to rise, security solutions will need to implement smarter and more targeted scanning systems that can identify samples that have been packed with known crypters.
Have something to comment on the above? Feel free to do so in the section down below, or on our socials, on Facebook and Twitter.