Hackers Deploy Babylon RAT Targeting Malaysian Government and Politicians
- Political figures and government entities in Malaysia were targeted with data-stealing and surveillance malware.
- Hackers used fake official documents as a lure, which hid malicious payloads.
- The threat actor and the distribution method have not been identified yet.
A sophisticated malicious campaign was seen targeting political figures and government officials in Malaysia with Babylon RAT. Active since July, this campaign employs malicious ISO files designed to infiltrate and compromise high-profile individuals and institutions, the latest report from Cyble Research and Intelligence Lab (CRIL) said.
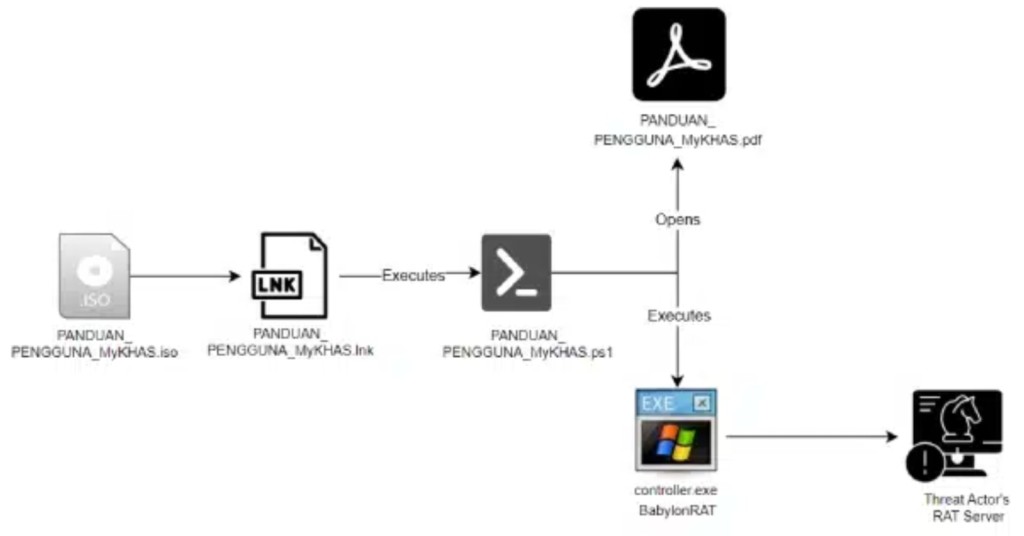
The attack mechanism involves ISO files that package several malicious components, including a shortcut file, a hidden PowerShell script, a malicious executable, and a decoy PDF file crafted to mislead users into believing they are engaging with legitimate documents.
While the initial infection vector is unclear, the lure documents include topics such as political concerns in Malaysia and the Majlis Amanah Rakyat (MARA), a Malaysian government agency. Other documents targeted Malaysian government officials who use the MyKHAS platform.
Once executed, these files initiate a series of actions culminating in the deployment of the Babylon RAT (Remote Access Trojan). This Trojan is known for its robust surveillance and data theft capabilities—keylogging, clipboard monitoring, password exfiltration, and remote command execution—while also maintaining persistence and evading detection by security tools.
The RAT can also launch Distributed Denial-of-Service (DDoS) attacks and make the host act as a SOCKS proxy to capture network traffic from multiple infected hosts, bypassing network security measures.
Security researchers have seen a recurring pattern associated with the threat actor behind this campaign, as previous attacks targeting Malaysian entities have utilized Quasar RAT, another open-source remote access Trojan. This aspect indicates a sustained focus on high-profile targets within the region.
Quasar RAT is an open-source RAT widely used by malicious actors, mainly in phishing campaigns. It offers a rich set of capabilities and is freely available on public repositories.
A modified version of the espionage Quasar RAT was used as a banking Trojan to target customers of financial institutions in Colombia.