Major Crypto-Stealing Malware Campaign Infects 28,000 Users Across Eurasia
- People in Russia, Ukraine, Turkey, and more are the target of a malware campaign designed to steal cryptocurrency.
- Hackers use lures such as legitimate software advertisements that are actually trojans.
- Once the victim extracts the false archive files, the target systems are compromised.
A large-scale cryptocurrency-stealing malware campaign has compromised over 28,000 users in Russia, Turkey, Ukraine, and other Eurasian countries. The campaign represents a sophisticated attack disguising trojans as legitimate software via YouTube promotions and fraudulent GitHub repositories.
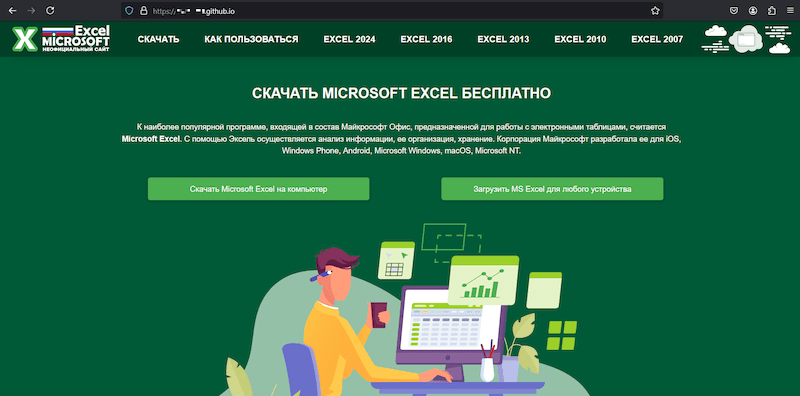
Initially reported by cybersecurity firm Dr. Web, the malware primarily affects users in Russia, with significant infections also detected in Belarus, Uzbekistan, Kazakhstan, Ukraine, Kyrgyzstan, and Turkey. Victims are lured into downloading password-protected archives disguised as pirated office software, game cheats, hacks, and automated trading bots.
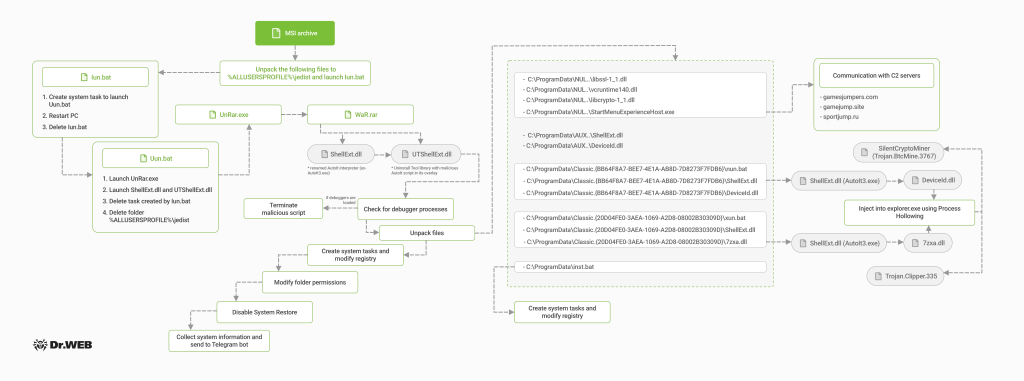
The attack begins by evading antivirus scans using password-protected self-extracting archives.
Upon extraction, the archive deploys obfuscated scripts and DLL files with an AutoIT interpreter to launch the malware's main payload.
The malware terminates if it detects debugging tools, indicating an analyst's environment.
It employs the Image File Execution Options (IFEO) technique to modify the Windows Registry, ensuring persistence by hijacking legitimate Windows services and browser update processes.
The malware disables Windows Recovery Service and revokes "delete" and "modify" permissions on its files to thwart cleanup attempts and establishes communication with a command and control (C2) server via the Ncat network utility.
Executed using "Deviceld.dll," the SilentCryptoMiner payload utilizes victims' computational resources for cryptocurrency mining. Then, Clipboard Clipper replaces copied wallet addresses in the Windows clipboard with those under the attacker's control, resulting in $6,000 worth of hijacked transactions thus far.
To prevent falling prey to such campaigns, users are advised to only download software from official project websites, avoid clicking on promoted results in Google Search, and exercise caution with shared links on platforms like YouTube or GitHub, as these do not guarantee safe download destinations.
Recently, a sophisticated Lua-based malware campaign was seen leveraging people’s interest in game cheats, and the hackers use a similar tactic, hosting and distributing malicious payloads through GitHub ZIP archives.