Magecart Skimmers Intercept Payment Data in Over 277 Websites
- Almost three hundred Magecart e-commerce platforms have had their customers’ payment data stolen.
- The hackers behind the skimming process are “Magecart Group 12”, a new team that took advantage of a JavaScript library.
- The attacks occurred between January 1 and 5, catching the protection mechanisms off guard.
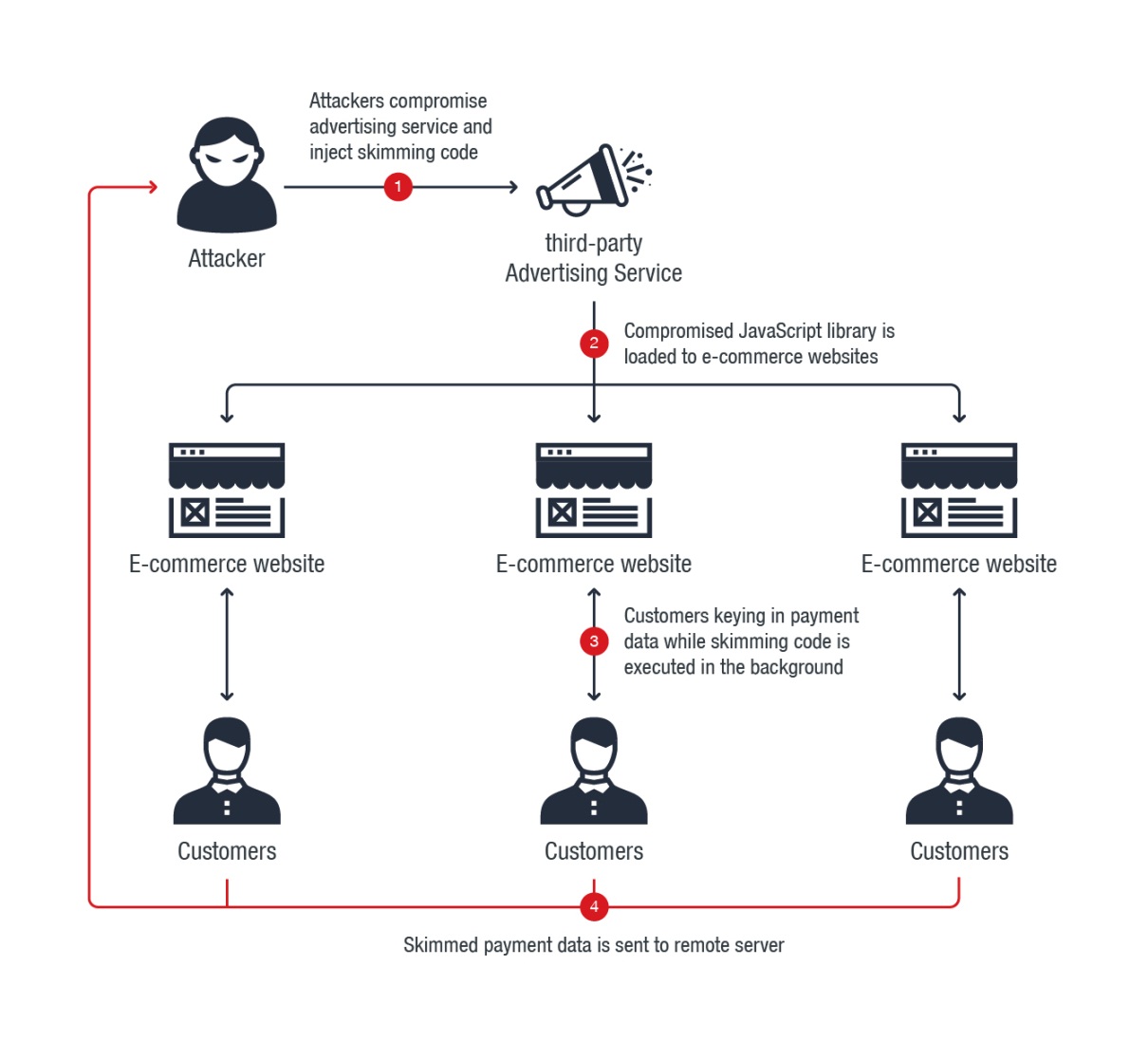
According to a Trend Micro report, a group of hackers that compromised an advertising supply chain tool called “Adverline” have intercepted the payment data of visitors of more than 277 e-commerce websites. Following this indirect attacking path, allowed the group (Magecart Group 12) to skim data from online shopping platforms without the latter realizing the existence and operation of their malicious code. Adverline is a JavaScript library that delivers publishing services on Magecart platforms, and JavaScript has the capacity to monitor and store any information that is displayed or inputted onto a webpage by the visitor. In this case, the information that was inputted was the payment details such as names and credit card numbers.
From the Trend Micro report
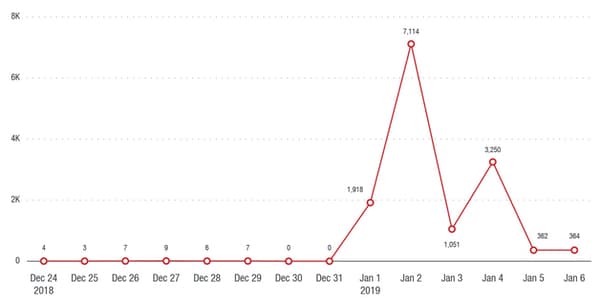
The skimming activities didn’t occur in a random day of the year, but between January 1 and 5, culminating in the first day of 2019. The obvious reason for this timing is the fact that most e-commerce platforms have their IT understaffed on January the 1st, and so are many security auditing and attack monitoring firms. For hackers, staying concealed is vital, and whatever way strengthens this factor is applicable. Magecart Group 12, however, didn’t just rely on timing, but they also incorporated two obfuscated scripts in their skimming toolkit, one of which is specifically developed to play an anti-reversing role.
From the Trend Micro report
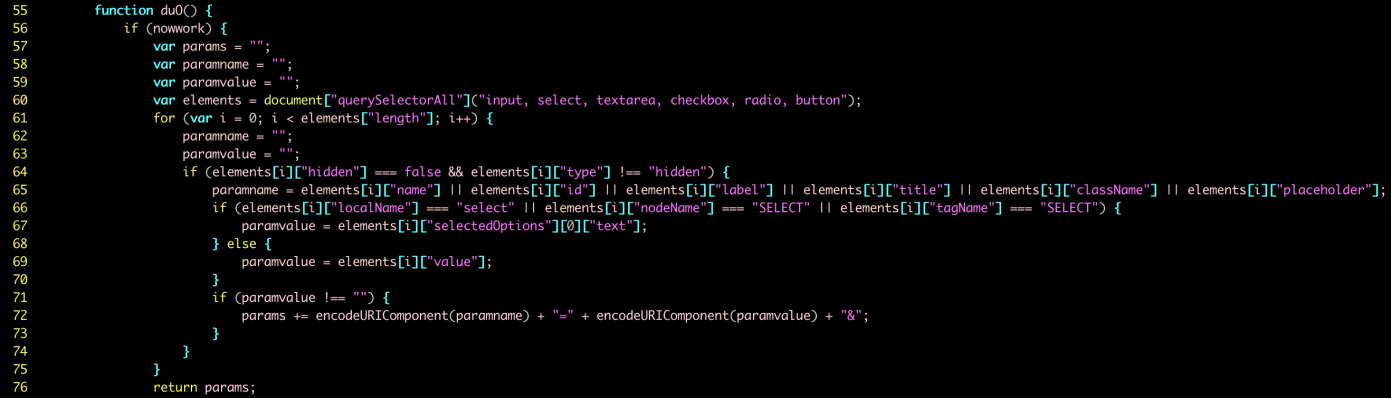
The second script is the one that does the skimming, performing the required URL string checks and deciding whether the information will get intercepted or not. The data that is entered onto the e-commerce platform by the customer/victim is then copied along with the form name, and all is neatly bundled and stored as a JavaScript LocalStorage “cache”, while it also gets encoded with the Base64 format. The victim is automatically given an identification number to enable the hackers to distinguish them, and when the user closes the payment form page, the script sends everything to a remote server through HTTP POST.
From the Trend Micro report
From the 277 e-commerce platforms that were affected, the vast majority are French websites (79%), but various websites from other European countries have also leaked the payment data of their customers. The number of affected customers is estimated to be on the level of millions, and the platforms are now expected to inform their customers of the fact that their payment card details have been stolen, also involving the financial institutions on the issuing of new payment cards. This process will hurt the reputation of the particular platforms and will undermine the trust that their customers may have towards them, even though they may not be directly liable for failing to assure the safety of their customers’ data. British Airways and Newegg suffered similar attacks in recent times, and are still on the way to recover their trustworthiness to their customers.
Do you double-check the running JavaScript processes when entering payment details on online forms? Let us know in the comments below, and don’t forget to share this story by visiting our socials on Facebook and Twitter.