Magecart Skimmers Strike Again – 65,000+ Data Theft Attempts Blocked in July Alone!
- Malwarebytes reports an astonishing increase in the number of Web skimming attacks in July, with this trend likely to continue to rise.
- Web skimming is oriented toward stealing your personal and payment information by infecting websites, primarily related to e-commerce.
- Be safe when shopping online, use a trustworthy and capable anti-malware tool and stay away from lesser-known online stores.
As you surely already know, new types of malware are appearing on a daily basis. Just recently, we wrote about different types of malware including BrushaLoader, Anubis, and the Fallout exploitation kit, all of which have the power to steal precious data and even inflict damage to your device. However, even though many of these quickly reach the peak of their popularity (and then slowly disappear over time), there are some malware types that simply refuse to let go. With this said, one of the most active types of stealing information is via Web skimming – directly related to a group called Magecart.
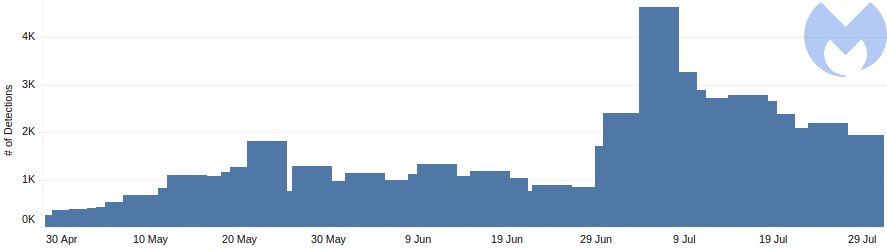
Web skimming is a process of stealing payment information directly within a Web browser, usually related to e-commerce websites. And even though skimmers (sniffers, or swipers as well) have been causing damage for a long time, Magecart is the best-known group of this kind, directly associated with many of these types of attacks. As previously reported, Magecart skimmers have targeted 200+ campus stores in the USA and Canada, over 270 websites across Europe, and even some big-name retailers were affected, including Newegg. And even though cyber-security companies have been issuing warnings about Magecart, it looks like the group has decided to strike yet again. As per the recent blog post published by Malwarebytes, this vendor had blocked over 65,000 data theft attempts in July only, the largest number ever - within a single month.
Image Courtesy of Malwarebytes.
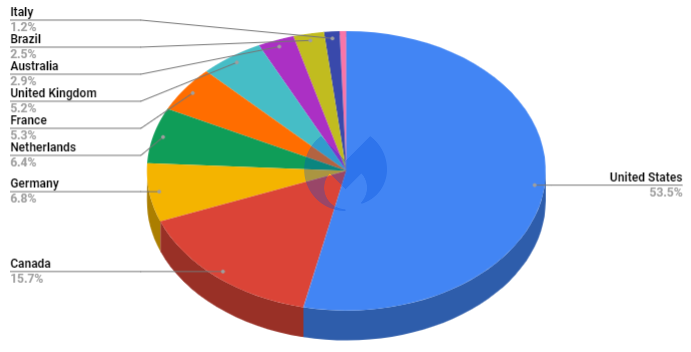
As per the report, 53.5% of these Magecart attacks happened in the USA and another 15.7% in Canada. These two countries are followed by Germany, the Netherlands, France, the United Kingdom, Australia, Brazil, and Italy. As we can see, this is a widespread infection affecting many countries, especially those markets with highly active e-commerce industries.
Image Courtesy of Malwarebytes.
One of the possible reasons for this sudden increase in online attacks is the fact that many malware kits are being sold underground, mostly on the Dark Web. One of the most popular ones is the Inter Kit, and it’s said that the Dark Web is filled with different variations of this kit, used by different types of threat actors. This is why it’s becoming hard to identify which group is behind certain attacks, even though the core part of any Web skimming-process is the same. That’s because Web skimming relies on a malicious JavaScript code that comes with some form of obfuscation.
By visiting an infected online store, you could easily have your personal and your payment data stolen. In some cases, this stolen data is being transferred to ‘blank payment cards’, even though there are many other ways your payment data can be misused. Of course, there’s always a possibility of someone selling that data on hacking forums, as happens far too often.
To stay protected from Magecart and Web skimming, it’s recommended to use a trustworthy and proven anti-malware solution. In addition, it’s recommended to use well-known e-commerce websites, instead of relying on smaller and unknown online stores.
Are you being careful when submitting your payment details over the Web? Do you stick to well-known e-commerce websites? Let us know in the comments section below, and don’t forget to follow us via our social media profiles, on Facebook and Twitter. Thanks!