Is MAC Address-Based Smartphone Tracking Still Possible?
- Mobile operating systems have made leaps to strengthen Wi-Fi privacy, but is it enough?
- Researchers have conducted a large study and found that recent models are indeed better protected.
- The fragmentation of the Android space remains a problem that creates privacy-undermining inconsistencies.
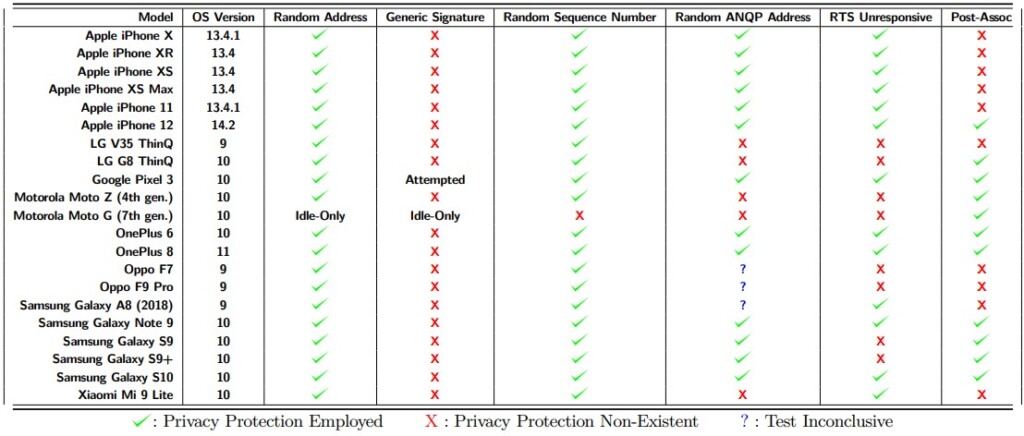
Back in 2018, developers of Android 9 Pie detailed the important security and privacy-enhancing features of the latest version of the popular mobile OS, with MAC address randomization being touted as one of the most important. Randomizing a device’s MAC address prevents malicious actors from abusing it to achieve persistent tracking and compromising the user’s privacy. Three years after this important step, a team of American researchers has revisited the landscape to test 160 mobile phone models and determine what percentage is resistant to common methods of MAC address tracking.
The study's main conclusion is that every smartphone vendor is following their own MAC address randomization technology, leading to fragmentation and weak implementations in general. Devices that run on Android 7, 8, or 9 were responding to abusive probing unpredictably, but those running Android 10 and above showcase a trend of convergence that helps in security. Even then, however, the situation isn’t perfect, as shown in the following table:
It is worth noting that the researchers also tested devices that were released in 2018 and later, so there are no heavily deprecated models in the study. The devices that scored pretty well include Google Pixel 3, iPhone 12, OnePlus 6 and 8, Samsung Galaxy Note 9, and Galaxy S10. This is another indication that the implementation of MAC address randomization systems isn’t consistent even among devices of the same manufacturer.
This is in line with the recommendations given by the researchers, which are the following:
- Devices should deploy privacy protections consistently, no matter the device state.
- Manufacturers should agree on a fixed, small, low-information device signature for probe requests.
- Post-association MAC address randomization should be on by default, and random MAC addresses used for a given SSID should be rotated regularly without user interaction. (iOS 14).
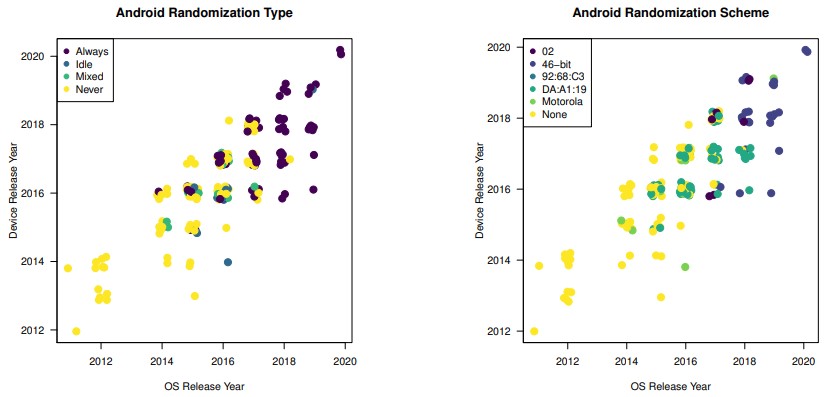
With the release of Android 10, MAC address randomization switched to being enabled by default for client mode, SoftAp, and Wi-Fi Direct. Still, the deployment of 46-bit randomization at all times isn’t enforced on smartphone vendors. This goes to show that there’s still work left to be done in order to achieve a respectable level of Wi-Fi privacy, especially on Android, and the fragmentation of the space is once again at the epicenter of the problem.
Still, the researchers concluded that the manufacturers had made huge steps, and it is now a lot harder for someone to track a smartphone user persistently using nothing other than Wi-Fi information. Even where this is possible, the deduced information is limited in exploitation value on its own.