Luscious Left a Database With 1.2 Million User Accounts Unprotected
- Luscious left their code database unprotected, risking sensitive information about their users.
- The adult content website is one of the most successful of its kind but has now blundered.
- Users should change their usernames and email addresses and should use a VPN from now on.
As reported by vpnMentor’s researchers Noam Rotem and Ran Locar, the pornographic image website Luscious could have had their core database accessed by hackers who would easily steal a galore of information. The accessible data includes the usernames, email addresses, user activity logs, country of residence, and gender of about 1.2 million people who have registered with the platform. Luscious is an adult content website that focuses heavily on user-uploaded content, so the images and videos are not coming from professionals working for big porn studios, but people who have every reason to want to protect their privacy.
While the real names of the users were not part of the compromised database, some were found to be using email addresses that clearly indicate their name. Other unveiling details include the video uploads of each user, their blog posts, their comments, their favorites, a list with their followers, and their ban status. With this information being exposed now, all blog posts can be associated with a person or at least an email address, whereas previously, they were published without even the username showing up.
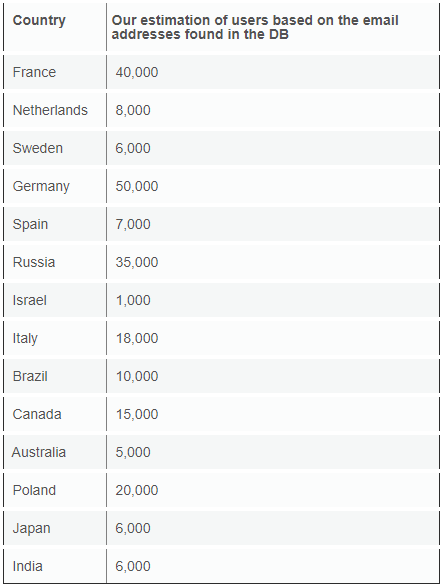
The researchers discovered the database five days ago, while the securing action took place just yesterday. Upon a more in-depth analysis, the researchers figured out that the locations of the users are very widely spread around the globe, with Europe taking the lion’s share. Another interesting detail that surfaced is that quite a few users joined Luscious by using official email addresses that carry the “.edu” or “.gov” domain. This is really unthinkable, yet it’s true, showing the level of incompetence and illogical paths that some people follow, considering none of the grave risks involved. All users of Luscious are urged to change their account details (username and email address) and to use an email that doesn’t contain any hints about their real identity. Also, using a VPN will help you change your location to a fake one. If you don’t, you are running phishing, extortion, and doxing risks.
image source: https://www.vpnmentor.com
As for Luscious, they have really screwed up by leaving their Elasticsearch database unprotected and unencrypted. If the database was exfiltrated and will be made available for sale on the dark web, competitors of the specialized adult content site will be more than willing to pay for this data bundle. This is because it will help them analyze user behavior, find out what people want, and get insight on what makes Luscious so successful.
Have something to comment on the above? Feel free to do it in the section beneath the post, or on our socials, on Facebook and Twitter.