Lumma Stealer Campaign Targets WordPress Sites via Fake ‘Fix It’ Cloudflare Verifications
- WordPress is leveraged to disseminate Lumma Stealer, which exfiltrates login credentials and crypto wallet details.
- Cybercriminals employ false messages that pretend to be Cloudflare checks in “fix it” campaigns.
- Users are persuaded to execute Powershell commands under the guise of running Windows Defender.
Cybercriminals are increasingly exploiting WordPress websites to propagate the Lumma Stealer trojan, leveraging fake Cloudflare verifications to trick users into executing malicious commands on their Windows devices.
Lumma Stealer, also referred to as LummaC2, is an information-stealing malware designed to covertly harvest sensitive data such as login credentials, browser cookies, cryptocurrency wallet details, and personal or system information.
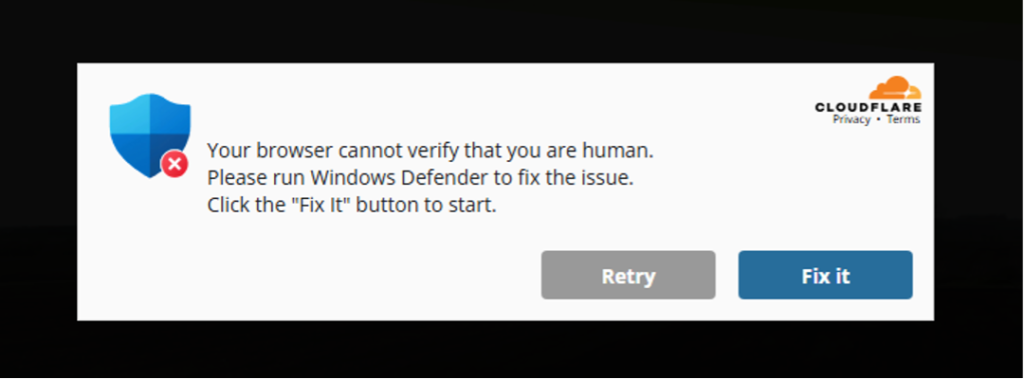
This sophisticated malware campaign continues to evolve, the latest Sucuri report says. The attackers utilize fake human verification systems, which have become commonplace to reduce server load and prevent unauthorized bot traffic.
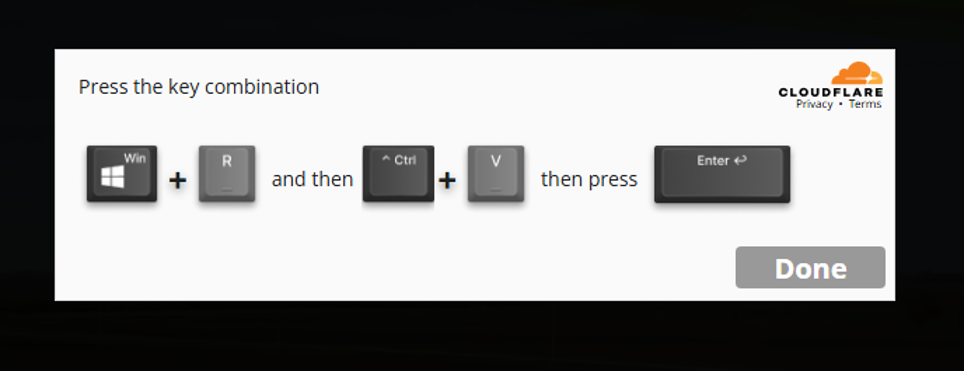
However, instead of legitimate verifications, users are confronted with deceptive prompts instructing them to execute Powershell commands under the guise of running Windows Defender.
This approach exclusively targets Windows users, leaving those on macOS or Linux unaffected. Once the malware is installed, it grants attackers full access to the victim's system, compromising bank information, social media logins, cryptocurrency wallets, and other data.
On the backend, cybercriminals deploy malicious WordPress plugins to enable the scam. Recently identified fraudulent plugins include:
- /wp-content/plugins/SwiftPress/SwiftPress.php
- /wp-content/plugins/nwPostSaver/nwPostSaver.php
These files are heavily encoded using hexadecimal and Base64 methods to mask malicious payloads. When deconstructed, they reveal links to dubious domains. These links are used to host payloads, including a trojan installer that runs on Windows systems.
While some of these shortened URLs have been taken down, they illustrate the attackers’ use of legitimate services like short[.]gy to obscure their malicious intent.
Separately, attackers are injecting malicious JavaScript into legitimate WordPress files, such as jquery-migrate.min.js. Unlike the plugin-based variant, this injection embeds the entire fake verification prompt, complete with malicious commands, directly into the file.
This approach avoids reliance on external URL shortening services, minimizing the chance of takedowns.
Key features of the attack include the creation of hidden admin users, as malicious plugins generate unauthorized admin accounts in WordPress, concealing these users from the admin panel while sending login credentials to the attacker’s domain.