Loda RAT Now Comes Upgraded & Stealthier Than Ever Before
- Researchers warn about a new version of the Loda RAT which is harder for AV tools to detect.
- The authors behind the malware have re-written large chunks of the code to improve its obfuscation.
- The infection begins with a phishing email that drops a malicious document, triggering an Office exploit.
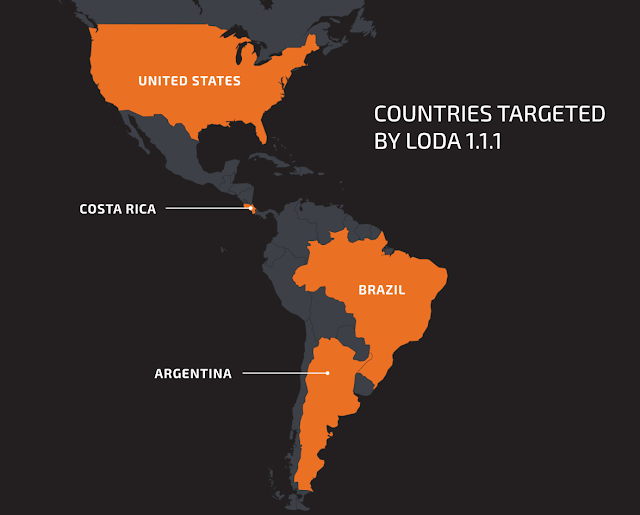
A new version of the Loda RAT (Remote Access Tool) is in the spotlight of Cisco Talos researchers, who have been observing its activity during the last couple of months. The new Loda (version 1.1.1) is used in fresh malware-spreading campaigns that target the United States, as well as Central and South America. Compared to previous versions of the notorious RAT that first appeared in 2017, the latest iteration features more advanced obfuscation based on new AutoIT scripts, additional persistence mechanisms, and the leveraging of WMI for the purpose of enumerating antivirus solutions in the target system.
Source: Talos Blog
The infection begins with the delivery of a malicious document (filename: "comprobante de confirmación de pago.docx") through a phishing email that links to another document (rich-text) via an OOXML relationship. This second file contains the exploit that fetches and unpacks an MSI file (fkrkdn.msi), which in turn contains the Loda RAT. Once this is done, the RAT activates and tries to steal user credentials present in Web browsers, parse the stored cookies, record sound, take screenshots, indulge in key-logging activities, and even support the sending of messages from the actor to the victim.
The exploit that is triggered by the second, "RTF" document, is CVE-2017-11882, which leads to arbitrary code execution on outdated Microsoft Office suites. The obfuscation method in the OLE object that contains the exploit and payload is based on the "control word" technique. This involves the use of sets of characters (control words) that translate to specific actions such as "ignore" or "stop her". This way, the actor can plant false control words and thus achieve a higher level of obfuscation.
Source: Talos Blog
According to the tests conducted by the Talos team, this significantly lowers the detection rates of Loda by AV solutions. The decision to pack the malware inside an MSI archive was also aiming at the same goal, as this alone reduces the detection rate of malicious executables by up to 50% on VirusTotal. This obfuscation was precisely the main point of developing version 1.1.1, as the Loda RAT remains more or less the same in terms of its functionality. However, there has been an extensive code rewrite under the hood, and the sole reason for this was to make it stealthier.
The Loda RAT remains a simple yet powerful tool in the hands of malicious actors, and this is exactly why they care to upgrade it into one that can’t be detected as easily. Once Loda finds its way into a system, the problem becomes huge for the compromised individual. That said, be very careful with how you treat unsolicited messages that arrive in your inbox and don’t try to open any attachments that accompany them. Finally, update your Office, Windows, and AV tools by applying the latest available patches. This would automatically render Loda useless in the case of these recent campaigns.