New Linux Hadooken Malware Campaign Targets Oracle Weblogic for Crypto-Mining
- Hackers were seen abusing Oracle's WebLogic servers to compromise victim systems.
- The attack deploys a second payload and a tool for unauthorized cryptomining.
- Security researchers believe the threat actor may also deal with ransomware attacks.
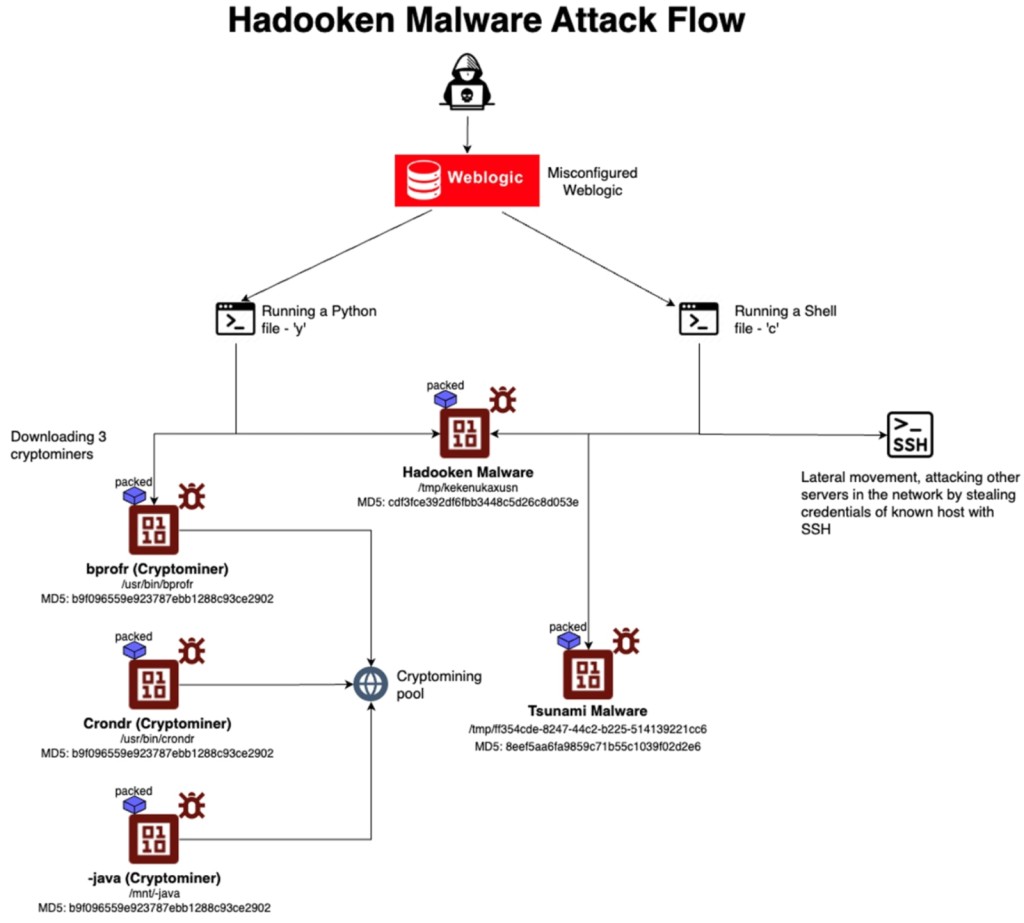
A new malware campaign targeting Oracle's WebLogic servers hinges on a Linux-based malware known as "Hadooken," according to a report from cloud security firm Aqua Nautilus. Upon execution, Hadooken drops the Tsunami malware and deploys a crypto miner.
This sophisticated exploit is primarily designed to infiltrate the enterprise-grade Java EE application server and deploy a cryptominer that leverages compromised systems for illicit cryptocurrency mining.
WebLogic Server is widely used across industries such as banking, e-commerce, and other business-critical systems and offers robust support for Java technologies, transaction management, and scalability.
The security weaknesses in WebLogic, such as deserialization flaws and improper access controls, often invite exploitation. Additionally, misconfigurations like weak credentials or exposed admin consoles can result in severe vulnerabilities, including remote code execution (RCE), privilege escalation, and data breaches, if not adequately secured or patched.
When deployed, the Hadooken malware executes a dual-stage attack. It first drops Tsunami malware, a known DDoS tool, onto the host system. Subsequently, it deploys a cryptominer, diverting valuable system resources for unauthorized cryptocurrency mining.
The hackers use a Unix Shell script, a Python script for malicious execution, and a PowerShell script to distribute malware. Tsunami creates cron jobs to maintain persistence by executing malicious payloads periodically.
The IP addresses used for Hadooken are registered under the hosting company AEZA – one inactive IP in Russia and one active IP in Germany. The latter was linked to TeamTNT and Gang 8220 in the past.
Some reports say that one of the IP addresses employed by the threat actor to download Hadooken malware is used to disseminate this ransomware, so the threat actor may be targeting Windows endpoints to execute a ransomware attack, as well as Linux servers to target software often used by big organizations to launch backdoors and crypto-miners.