Lengthy Ransomware Campaign Already Compromised 83K MySQL Servers
- Thousands of MySQL servers have already fallen victim to a new ransomware campaign that wipes databases.
- The data is exfiltrated on the actors’ server and then resold, bartered, or leaked on the dark web.
- The attackers haven’t made a lot of money yet, but they create an increasingly problematic situation.
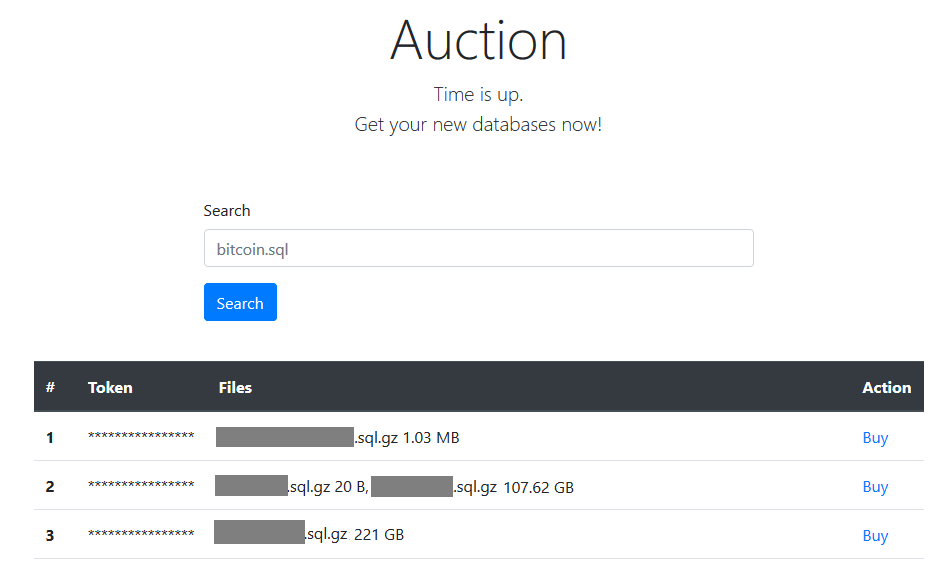
There’s a large-scale and lengthy ransomware campaign going on since January 2020, and it has already compromised 83,000 MySQL servers. According to a detailed report compiled by researchers of Guardicore, the malicious actors have stolen about 250,000 databases with the sole purpose of making money by extorting the victims.
What they do is to demand a ransom of up to 0.08 BTC ($1,420), threatening to publish the stolen data online. Through this way alone, the actors have made $24,900 so far.
But this isn’t the only way they’re making money from the campaign. The hackers are planting a backdoor on the compromised database so they can reaccess it any time in the future. To monetize on this, they sell access to other hackers on the dark web. Additionally, they publish some of the data and ask for additional ransom payments from the victims. And finally, they are offering this data for purchase on dark web marketplaces.
Guardicore has recorded a sharp increase in the number of attacks since October, with at least 11 different IP addresses serving as launch points. The attackers have even set up a payments website on the TOR network now, so the extortion and payment process has been automated. Also, there’s a repository of stolen databases that is accessible by the victims, serving as a convincing factor.
The attack begins by brute-forcing the MySQL admin password, accessing the server and the contained databases, and scraping the stored data. Everything is archived in a zipped file and exfiltrated, while the original files are wiped from the database. What is left is a ransom note in the form of a table named “WARNING.” For the backdoor, the actors are creating a new user “mysqlbackups’@’%” added for persistence.
This campaign is a splendid example of automated targeting, and its scope includes all five millions of MySQL servers out there. It is not particularly sophisticated, can’t be considered persistent, but it can still be quite damaging.
That said, if you are a MySQL admin, you should use a password that’s impossible to brute force. Additionally, you may want to disable remote logins, limit or disable “show databases,” alter host access, change the default port mappings, remove users without passwords, remote anonymous accounts, audit plugins, and remove the test database.
Also, encrypting transiting data using SSL, and also the stored data, of course, would render their exfiltration worthless. That is as long as you keep regular backups handy, as the local data will get wiped in the process.