Legitimate Sypex Dumper Database Backup Utility, Used for Backdoors in WordPress Framework
- Attackers injected the Sypex Dumper database backup utility into the WordPress files for malicious purposes.
- A suspicious file located in the fonts directory masqueraded as a legitimate font-related file.
- This tool served as a backdoor for attackers to exploit the website’s database.
Attackers used the Sypex Dumper legitimate software in a malicious capacity within WordPress site files. They exploited outdated or overlooked software to create backdoors and gain unauthorized access to websites.
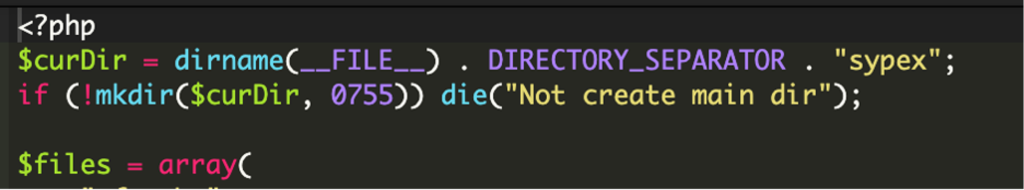
A recent investigation by Sucuri cybersecurity analysts identified the compromise during a routine integrity check of WordPress core files, where a suspicious file located in the wp-content/fonts/ directory appeared to mask itself as a legitimate font-related file, font.php.
Upon further scrutiny, it was revealed to be a modified version of the legitimate Sypex Dumper database backup utility. This tool, once embedded in the WordPress files, served as a backdoor for attackers to exploit the site’s database.
The attackers had ingeniously combined various components of the Sypex Dumper utility (such as sxd.js and cfg.php) into a single file. When the compromised font.php file was accessed, it initiated a function to recreate the original utility's structure, giving bad actors unauthorized access to sensitive database content.
Sypex Dumper, no longer maintained by its original developer, became the perfect target for cybercriminals due to its lack of security patches and updates. This is a recurring trend, where attackers repurpose outdated software to exploit vulnerabilities and gain entry into systems.
According to other reports, outdated Adminer scripts have been leveraged to steal database credentials and spread malicious code across websites. Similarly, a vulnerability in the File Manager plugin for WordPress left over 700,000 websites vulnerable to complete takeovers.
Even legitimate tools, when exploited or used improperly, can pose a significant security risk. Attackers often lean on outdated or unmonitored software to extract sensitive data such as admin credentials, stored user transactions, and other valuable information.
Sucuri underscores that while tools like these may not interfere with a site’s functionality, they are frequently employed as footholds for larger, more destructive attacks.