Lazarus Hackers Exploit Google Chrome Zero-Day in Fake DeFi Game Attack
- Lazarus APT employed fake DeFi games to abuse a Google Chrome zero-day vulnerability.
- The attack involved social media ads, spear-phishing, and LinkedIn to lure in high-value individuals in cryptocurrency.
- The threat actor used a fraudulent NFT-based MOBA with stolen source code from a legitimate game.
North Korean Lazarus hackers have exploited a Google Chrome zero-day vulnerability using a fake decentralized finance (DeFi) game. This attack targeted high-value individuals in cryptocurrency through social media ads, spear-phishing, and LinkedIn, likely for cryptocurrency theft, according to a Kaspersky report.
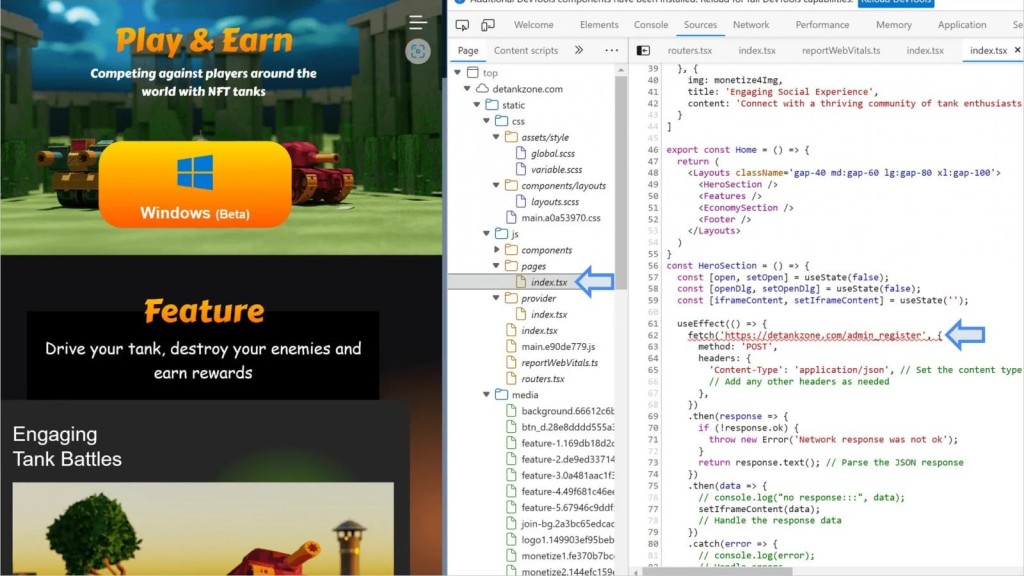
The zero-day flaw tracked as CVE-2024-4947 was exploited via the "detankzone[.]com" website, which promoted a fraudulent NFT-based multiplayer online battle arena (MOBA), "DeTankZone," which used stolen source code from a legitimate game, DeFiTankLand.
The attackers utilized Chrome's V8 JavaScript engine's type confusion vulnerability. By leveraging the JIT compiler, Maglev, they corrupted Chrome’s memory, gaining access to cookies, authentication tokens, saved passwords, and browsing history.
A second, previously fixed V8 flaw was exploited to escape Chrome's V8 sandbox, achieving remote code execution by executing shellcode in the system's memory.
The hackers also conducted reconnaissance. The shellcode collected system data and transmitted it to Lazarus’ C2 server to assess the machine's value for further attacks.
The attack was discovered by Kaspersky on May 13, 2024, months after it began in February 2024, due to detecting a new variant of the "Manuscrypt" backdoor malware on a customer's computer in Russia. Google issued a fix for the zero-day vulnerability on May 25, with Chrome version 125.0.6422.60/.61.
The attack demonstrates not only the technical sophistication of threat actors like Lazarus but also their strategic use of social engineering and repurposed legitimate assets to penetrate systems.
In other recent news, cyber-espionage actors associated with North Korea targeted the energy and aerospace sectors with a sophisticated new malware dubbed MISTPEN. This campaign was attributed to the cyber group UNC2970, also known as TEMP.Hermit, Lazarus Group, or Diamond Sleet (formerly Zinc).
Also, threat actors affiliated with North Korea deployed the COVERTCATCH malware through deceptive job recruitment schemes via LinkedIn, targeting developers in DeFi and the wider Web3 sector.
Meanwhile, the FBI warns that North Korean hackers increasingly target DeFi, crypto companies, and connected entities with sophisticated social engineering tactics, impersonating prominent people or entities via fake websites.