The “Lazarus Group” Is Targeting Aerospace Companies on LinkedIn
- North Korean hackers have returned to abusing LinkedIn, targeting employees of large firms with job offerings.
- The actors are sending malicious files to their victims, silently infecting them with malware.
- The techniques demonstrated in this campaign are top-notch, which is a characteristic of the “Lazarus.”
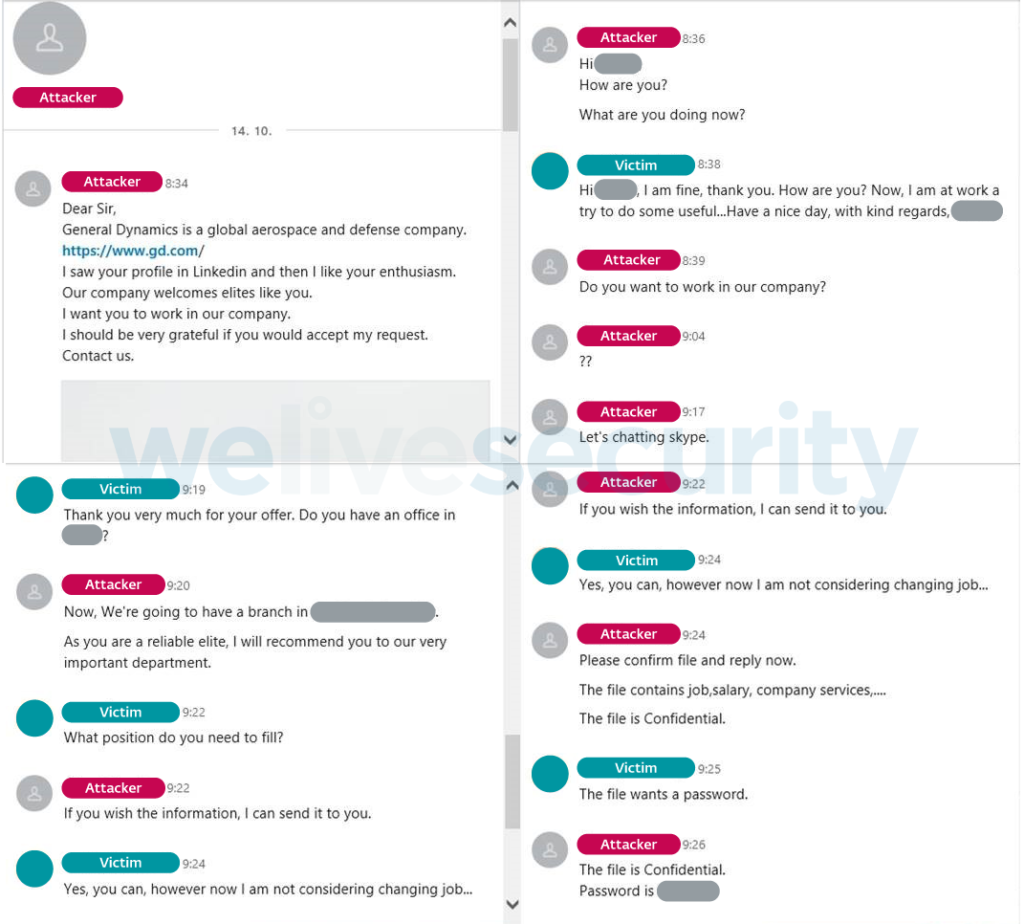
ESET researchers warn about a new BEC (business email compromise) campaign launched by the North Korean “Lazarus Group,” which they call “Operation In(ter)ception.” The hackers are using fake LinkedIn accounts impersonating high-ranking HR personnel from well-known aerospace and military equipment manufacturers. They then connect with their targets who work for competitors and send them direct messages that supposedly relate to a job opening they’re fit for. In these conversations, the Korean hackers are dropping malicious documents that allegedly contain useful information about the position in question.
Source: ESET
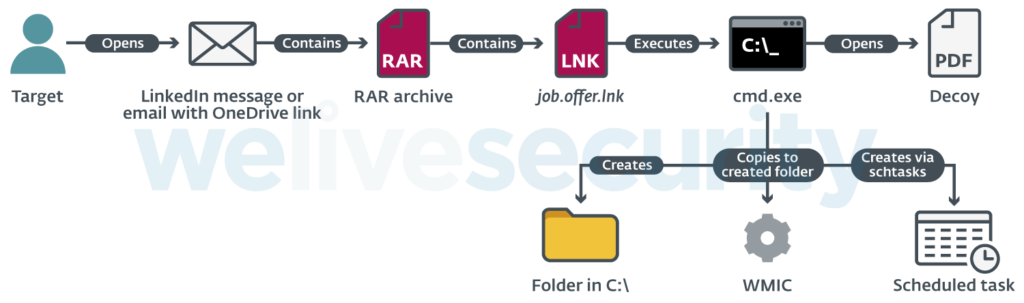
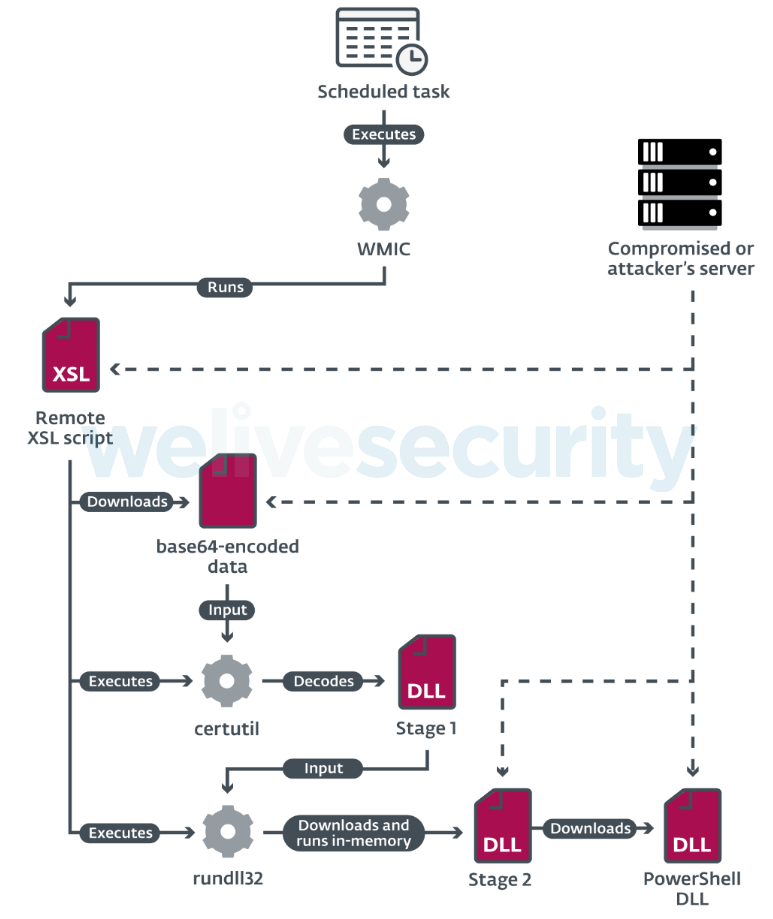
The shared file is a password-protected RAR archive that contains an LNK file which opens a remote PDF on the target’s browser. The victim is given the password on LinkedIn and is advised that this is confidential information and so they shouldn’t share it with others. Indeed, the file contains a listing of job positions with salary information, but this is just what the victim sees. In the background, a folder is created through the Command Prompt, and the WMIC utility is dropped inside. At the same time, a scheduled task is added to execute a remote XSL script. From that point, the target’s computer can be considered compromised.
Source: ESET
ESET has recorded the deployment of various downloaders, backdoors, DLL loaders, beacon DLLs, etc. The attackers followed “living off the land” methods, and in several cases, they differentiated their workflow to evade detection. This is the Lazarus group we’re talking about, so these are highly skillful actors who deploy custom tools and can maneuver as required. In many cases, the actors renamed the newly created folders and the malicious files to resemble software from Intel, Nvidia, Skype, Mozilla, and OneDrive. Moreover, they implemented control-flow flattering and dynamic API loading to keep their custom malware safe from the analysis.
Source: ESET
The goal of the actors is data exfiltration and business email compromise. They steal the victim’s email account password, send messages to the company he/she is currently working for, and either infiltrate deeper or divert payments to bank accounts they control. This is not the first time that the Lazarus Group has abused LinkedIn to do their thing. Back in January 2019, we reported about how the Korean hackers managed to breach in Redbanc’s systems after they approached an employee of the company with a job offer on LinkedIn. The result was the compromise of 3688 ATMs with custom malware, affecting 21 banks and a significant number of people.