The Lazarus Group Accused of Being Behind the Widespread Redbanc Cyber Attack
- Redbanc security breach was probably conducted by the Lazarus Group, according to a local media outlet.
- The breach was achieved through the use of a malware that has been modified by the North Korean hackers so that anti-virus tools don’t detect it.
- The infection was the result of methodical work that spoofed a Redbanc employee.
According to an investigation conducted by a Chilean tech news site, the cyber attack that hit Redbanc last December was likely carried out by the North Korean hacker group known as “Lazarus”. The evidence that points to the especially prolific team of threat actors is the utilization of the “PowerRatankba” malware strain that has been repeatedly used by the particular group. This revelation comes almost a full month after the actual attack, and an interesting story unfolding with it.
Redbanc is an inter-banking network that collaborates with 21 Chilean banks, being responsible for all of the country’s 3688 ATMs. The hacking incident was kept secret until the Chilean Senator Felipe Harboe publicly asked them to disclose the breach, and shortly after they did. Their press release though didn’t disclose any details on the incident, while it highlighted that the event had no impact on their operations. Redbanc states that these incidents are common for all companies and that by operating with high-security standards, they managed to detect the issue immediately and isolate the problem.
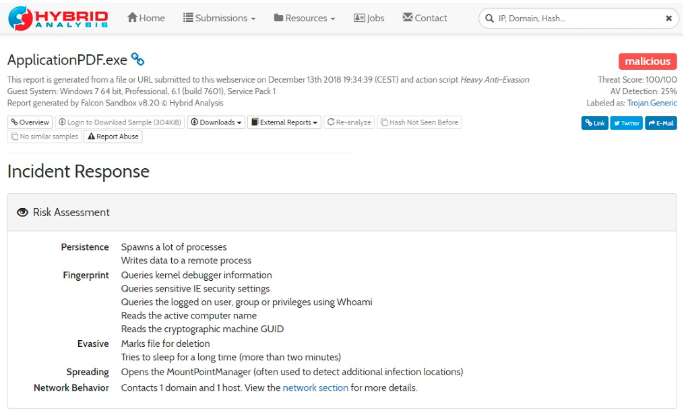
As revealed by TrendTIC though, the breach was actually achieved by channeling through a single Redbloc computer that was infected with the malware. The Lazarus Group posted a lucrative software developer position on Linkedin, setting the bait for someone to get hooked. One of Redbloc’s employees applied for the job, and the hackers contacted him through Skype, conducting an interview in Spanish, so everything seemed perfectly legit. Once the employee was entirely convinced that the job offering is real, they asked him to install a program named “ApplicationPDF.exe”, supposedly as part of the application process. The antivirus on the local system didn’t detect any problems with it, so the program that contained the “PowerRatankba” was installed on the computer. This opened up the gates of the whole company’s network for the hackers, giving them access to information such as PC usernames, OS details, proxy settings, running processes, RPC and SMB shares, and RDP connection status.
Image Source: trendtic.cl
According to Redbloc’s press release, the hackers didn’t get the chance to take the infection to the next level, delivering more intrusive scripts to the infected machine, as they identified the infection and isolated the malware-ridden PC. However, announcements like these should be always taken with a grain of salt, especially when the company didn’t want to reveal anything about the incident in the first place.
Do you have any opinion on the above? Let us know in the comments below, and don’t forget to also visit our socials of Facebook and Twitter, to be among the first to get fresh tech news.