Lazarus Group Deploys New Backdoor Against Energy and Aerospace Sectors
- Lazarus Group was seen delivering a new backdoor that targets professionals from the aerospace and energy sectors worldwide.
- The threat actor uses fake job offers as a lure, contacting victims via email and WhatsApp.
- A ZIP archive is used to deploy the previously undocumented backdoor.
Cyber-espionage actors associated with North Korea have been seen targeting the energy and aerospace sectors with a sophisticated new malware dubbed MISTPEN. This campaign was attributed to the cyber group UNC2970, also known as TEMP.Hermit, Lazarus Group, or Diamond Sleet (formerly Zinc).
The group has been leveraging job-themed phishing attacks, masquerading as recruiters from prestigious companies. By crafting spear-phishing lures, they manipulate potential victims—primarily senior-level employees—into engaging through email and WhatsApp.
UNC2970 primarily targets various entities located in the U.S., the U.K., the Netherlands, Cyprus, Sweden, Germany, Singapore, Hong Kong, and Australia.
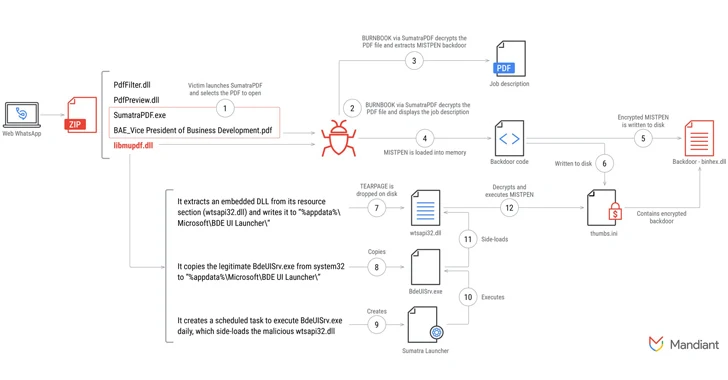
The ultimate goal is to deliver a malicious ZIP archive containing a deceptive job description that requires a compromised version of Sumatra PDF to open, thereby executing the backdoor malware.
The spear-phishing strategy involves instructing targets to use a trojanized version of Sumatra PDF, referred to as BURNBOOK, to read the job description PDF. This compromised reader deploys a malicious DLL file known as TEARPAGE, which launches the MISTPEN backdoor upon system reboot.
MISTPEN is a trojanized version of a legitimate Notepad++ plugin, binhex.dll, which contains a backdoor. The malware is built on a lightweight C framework, enabling it to download and run additional executable files via a command-and-control server using Microsoft Graph URLs.
Researchers from Mandiant have identified that the malicious actors are iterating on MISTPEN's capabilities, enhancing its features to evade detection, including using compromised WordPress sites as command and control (C2) domains.
This campaign highlights the persistent threat North Korean cyber actors pose to global industries. By targeting high-level employees and using sophisticated malware delivery mechanisms, these groups aim to acquire sensitive information valuable to North Korean interests.
In the latest news, threat actors affiliated with North Korea have been seen deploying the COVERTCATCH malware through deceptive job recruitment schemes via LinkedIn, targeting developers in decentralized finance (DeFi) and the wider Web3 sector.
Meanwhile, the FBI warns of aggressive North Korean cryptocurrency hackers using social engineering.