Latest Version of ‘Plantronics HUB’ Vulnerable to Privilege Escalation
- The latest available version of the Plantronics HUB application for Windows 10 and 8 is vulnerable to EoP attacks.
- As discovered by offensive security researchers, the software activates a component that offers higher levels of authorization.
- The attack can only work for local unauthorized users, but it’s fairly simple to carry out and even automate.
Security researchers have found a privilege escalation flaw on Plantronics HUB 3.21, the latest version of the client app that enables users of Plantronics audio devices to control the settings, customize ringtones, check battery status, update headset firmware, change voice prompt options, activate mute, and more. The flaw, which has a CVSS v3 score of 7.8, was discovered during a red team operation aiming to take over a domain controller server in a Windows network.
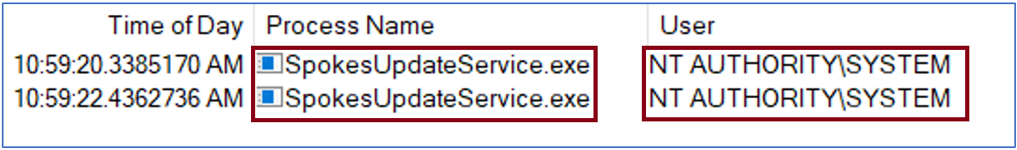
As the pen-testers found out during their offensive security session, Plantronics HUB can be installed by unprivileged users and then run as “NT_AUTHORITY\SYSTEM,” which unlocks all kinds of potential. More specifically, the component that offers this capability is a service called “SpokesUpdateService.exe,” which can be easily “tricked” with Symlink into deleting any file on the system.
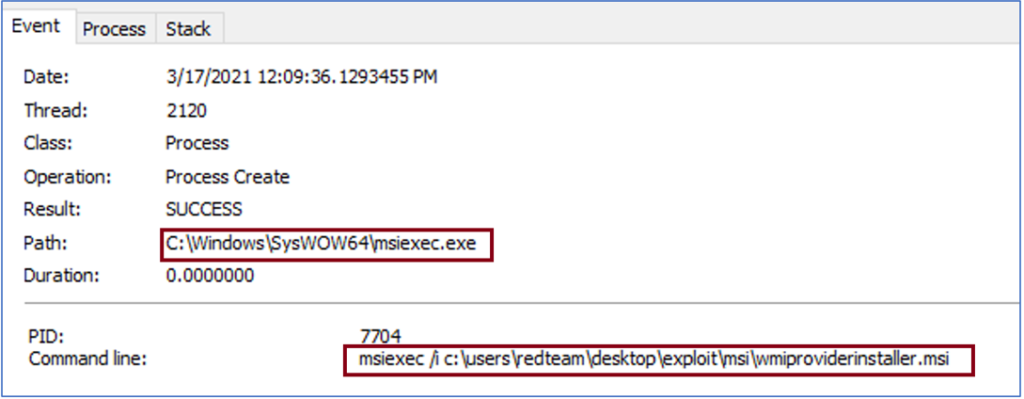
If a malicious actor chooses to delete a configuration file, they could put the app in an uninitialized state after the installation step, potentially opening up the way to remote code execution as NT_AUTHORITY\SYSTEM. Indeed, the researchers found a way to run arbitrary binaries that use the signature validation of the software’s installer MSI package.
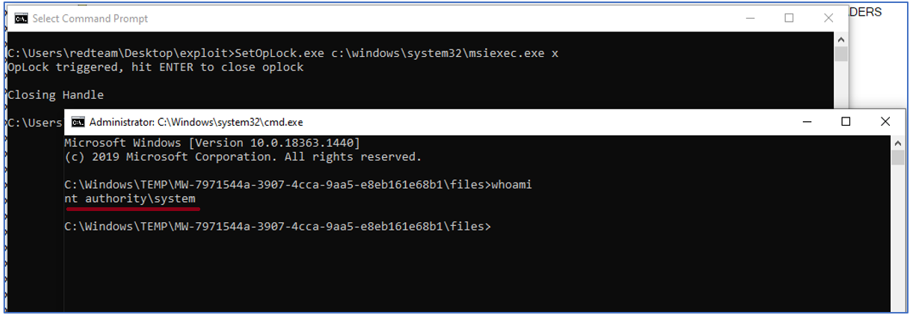
After that, the goal of escalating privileges to dump the memory of the LSASS process inside the compromised Windows server and eventually retrieve the credentials of a domain admin user was simple. So simple that the researchers decided to keep the PoC private for now, as it could lead to mass exploitation. Also, this bug affects the latest available Plantronics HUB, which is version 3.21, so there’s no fix for it when writing this.
One thing to note is that this attack works only for attackers who have local access to the target machine. As such, it is not a remote threat, although it could serve as a subsequent step for actors who have established their presence on a network.
Plantronics devices are typically used by customer support and call centers but are generally widely deployed by all professionals today as they are useful to anyone who engages in teleconferencing. In this period, when large parts of the global workforce are working from home, this is unquestionably a critical finding.
The researchers have promised to give more details about the bug at the upcoming Blackhat conference, which is to take place in the first days of August. That said, Poly, the owner of the Plantronics brand, has until then to fix the flaw. Until that happens, you may want to uninstall the software from your computer.