Latest Nvidia GPU Driver Update Fixes High and Medium Severity Flaws
- Two flaws in the Nvidia Control Panel component could result in DoS and sensitive info exfiltration.
- Nvidia has pushed fixes for Windows, but some Tesla products will have to wait until March to get them.
- One of the vulnerabilities require local access on the target machine, but the other can be triggered remotely.
Nvidia has released GPU “Game Ready” GeForce driver version 442.5 and the corresponding versions of the branches that concern the Tesla and Quadro ranges, fixing two critical vulnerabilities. The plugged flaws could enable attackers to engage in privilege escalation attacks or to trigger a denial of service states that open the door to malicious code execution or the exfiltration of sensitive information from the target. Thus, you are advised to update your Nvidia GPU driver immediately, as this is a security patch and not a mere feature or performance upgrade.
The bugs that have been ironed out are the following:
CVE-2020-5957 – CVSS v3 score: 8.4, This is a vulnerability in the Nvidia Control Panel component which enables an attacker to corrupt a system file and impose a denial of service state of the target system. The escalation of privileges through the exploitation of this bug is also possible.
CVE-2020-5958: - CVSS v3 score: 6.7, This is another flaw in the Nvidia Control Panel component, which an attacker could exploit by planting a malicious DLL file on the system. It requires local system access, but if this is met, the attacker could execute code arbitrarily, access any information on the target system, and impose a denial of service state.
The affected products and driver versions all concern Windows, and are the following:
- GeForce – all R440 prior to 442.50
- Quadro – all R440 prior to 442.50, all R430 prior to 432.28, all R418 prior to 426.50, all R390 prior to 392.59
- Tesla – all R440 versions remain vulnerable, as the fixing patch is estimated to arrive on March 9, 2020, all R418 prior to 426.50
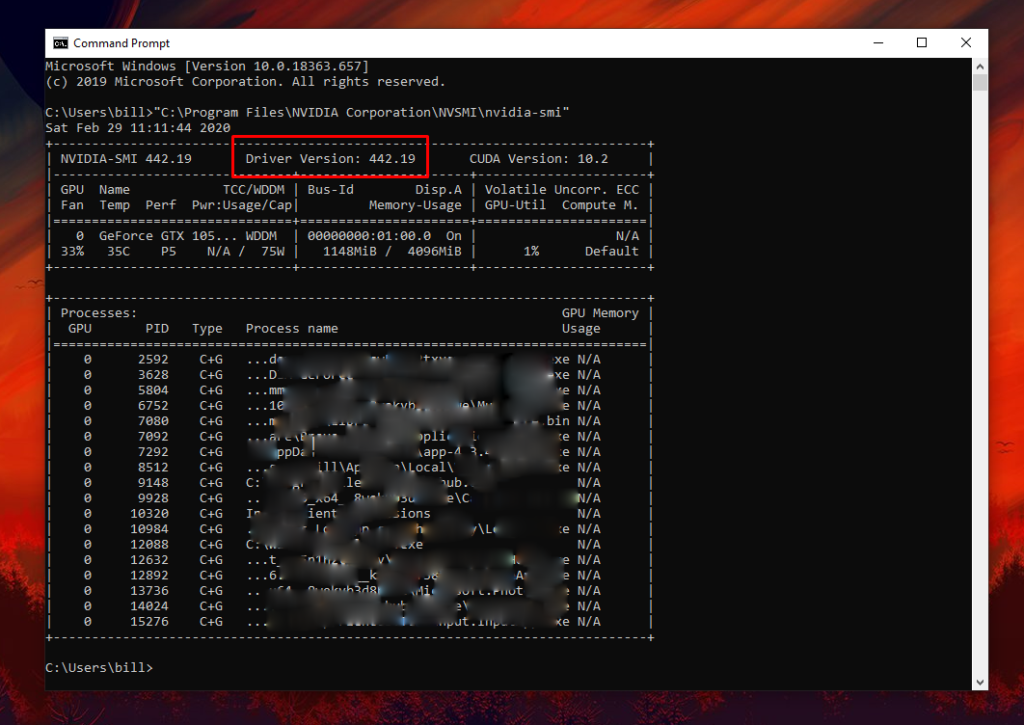
If you’re not sure about which driver you’re using and whether or not you’re vulnerable to the attacks described above, open the command prompt and run the following onto it: "C:\Program Files\NVIDIA Corporation\NVSMI\nvidia-smi". This should display the driver version and the processes that your GPU is handling at the time.
To get the latest version, you should visit Nvidia’s “Driver Downloads” webpage, enter your product details and your OS and download the latest available version for your graphics card. Alternatively, you may install the “GeForce Experience” tool which will serve you pop-ups and reminders when a new driver version is available for your product, but this software comes with its own security vulnerabilities so beware.