The Record for the Largest Ever Recorded DDoS Attack Has Just Been Broken
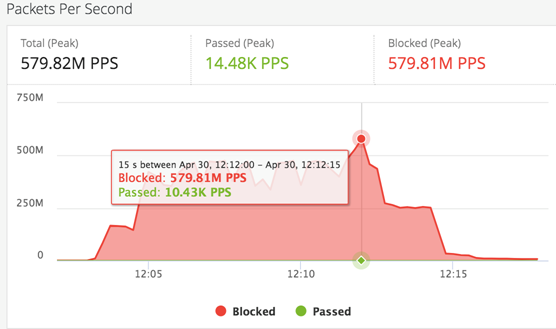
- A DDoS attack that peaked at 580 million packets per second was recorded by Imperva.
- This is 80 million packets per second more than the previous most massive attack, recorded in January.
- The trend will continue to be characterized by an increase in the PPS, as these attacks are harder to deal with.
Imperva has recorded the largest ever DDoS (Distributed Denial of Service) attack against one of their customers on April 30, peaking at 580 million packets per second (PPS), and lasting for about 15 seconds. While the attack was successfully dealt with thanks to the effectiveness of Imperva’s defensive systems, the fact that the DDoS actors went so far to deliver a powerful blow is something that marks the dawn of a new age, one that will involve massive attacks with PPS numbers that will cross the barrier of 500 which was previously considered the ceiling.
image source: imperva.com
As Imperva points out, DDoS bandwidth is something that the media pays attention to, but in reality, it’s the PPS that matters for measuring the intensity of the attack and how difficult it is to block the malicious effort. DDoS attacks are aimed at overwhelming the capacity of the targeted network, rendering it incapable of handling any more requests, bringing its computing and bandwidth resources down to their knees and causing an outage. High numbers of PPS are challenging for the network infrastructure because they require high processing power due to the way the evaluation of the packet headers is being done.
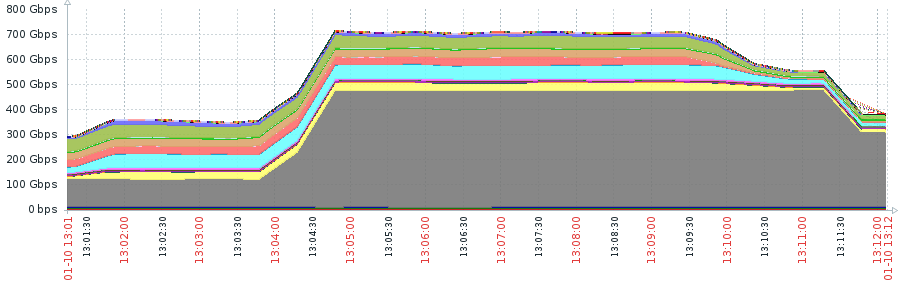
Imperva claims to be handling DDoS attacks that go over 500 Gbps of bandwidth every week, and as long as the PPS number is relatively low, these attacks are easy to mitigate through the defensive mechanisms that are in place on their clients’ networks. However, the trend of generating higher PPS in the conducted DDoS attacks is getting more popular. While the generation of particularly high forwarding rates is harder for malicious actors as well, even older SYN flood tools seem to be adequate to deliver non-manageable attacks when used in combination.
image source: imperva.com
Imperva had seen this combined attack manifesting for the first time against one of their clients back in January, when a syn flood tool was augmented by a second “large-scale” syn flood tool, delivering a “testing blow”. Both tools tried to mimic legitimate operating systems and sent almost identical packets of 800-900 bytes of size. The January attempt was like a test run for this latest record-breaking DDoS attempt, but the chances of this record to stand the test of time are slim to none. We expect to see higher PPS numbers soon, testing the limits of defensive mechanisms, and pushing things to new territories.
Do you believe that defending against DDoS will soon become non-feasible, or are network defense vendor always find ways to offer efficient mitigation solutions? Let us know what you think in the comments down below and also on our socials, on Facebook and Twitter.