More Than a Billion Wi-Fi Devices Could be Vulnerable to “Kr00K”
- “Kr00k” is a new vulnerability affecting unpatched Wi-Fi access points and devices using the WPA2 protocol.
- There are over a billion devices that are affected by this flaw, but most of them have already received fixing patches.
- This flaw doesn’t compromise your internet data directly, nor does it enable attackers to launch MITM attacks.
ESET researchers have discovered a previously unknown vulnerability given the identifier “CVE-2019-15126”, and which affects Wi-Fi chips made by Broadcom and Cypress. The serious flaw was given the name “Kr00k”, and concerns the encryption that is used in Wi-Fi devices and how an attacker could cause them to use an all-zero key. This would enable the actor to decrypt the wireless network packets that are transmitted, which opens up multiple possible exploitation paths. Since Broadcom and Cypress are making the vast majority of Wi-Fi chips in the market, Kr00k affects a wide range of devices such as smartphones, laptops, tablets, IoTs, and more.
ESET researchers have tested and confirmed that the following devices are vulnerable to Kr00K:
- Amazon Echo 2nd gen
- Amazon Kindle 8th gen
- Apple iPad mini 2
- Apple iPhone 6, 6S, 8, XR
- Apple MacBook Air Retina 13-inch 2018
- Google Nexus 5
- Google Nexus 6
- Google Nexus 6S
- Raspberry Pi 3
- Samsung Galaxy S4 GT-I9505
- Samsung Galaxy S8
- Xiaomi Redmi 3S
The above are given indicatively, just to make a point about the range of the devices that are affected. Broadcom and Cypress have already released updates that address the discovered vulnerabilities, and the majority of the affected manufacturers have delivered them onto the end-users, so the disclosure can be made now. If you have neglected the application of any pending updates for some time, you should install them immediately now.
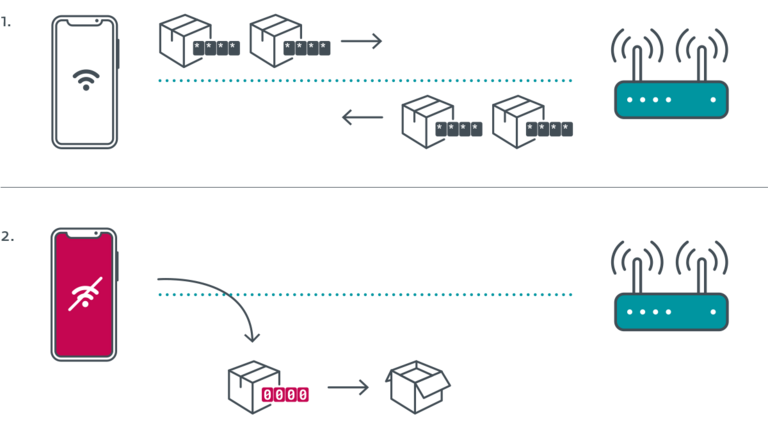
A “Kr00k” attack begins with the actor getting in range of the vulnerable Wi-Fi-enabled device and triggering a disassociation (disconnection from a WPA2 Wi-Fi point). When in this state, devices are using an “all-zero” 128-bit temporal key (TK), so the hacker can capture and easily decrypt some random data packets that are transmitted from the unpatched chips. No Wi-Fi password is required for this, and thus changing it won’t protect you from Kr00k attacks.
Source: WeLiveSecurity
To further complicate things, Kr00k unfortunately also affects Wi-Fi access points. This means that even if you patch your smartphone or tablet if the access point remains unpatched, you continue to be vulnerable to Kr00k attacks. ESET tested the following four access points and found them to be vulnerable to the flaw:
- Asus RT-N12
- Huawei B612S-25d
- Huawei EchoLife HG8245H
- Huawei E5577Cs-321
To clarify, Kr00k is helpful to hackers in the sense that it unlocks your Wi-Fi network and partially lifts its encryption security. It doesn’t directly compromise your internet browsing data, like email and online banking passwords. These are still protected by the TLS encryption, but Kr00k brings malicious actors one step closer to them. Finally, ESET reports that Kr00k concerns WPA2 Personal and Enterprise protocols that AES-CCMP encryption. Devices using the more recent WPA3 protocol aren’t affected by this vulnerability.