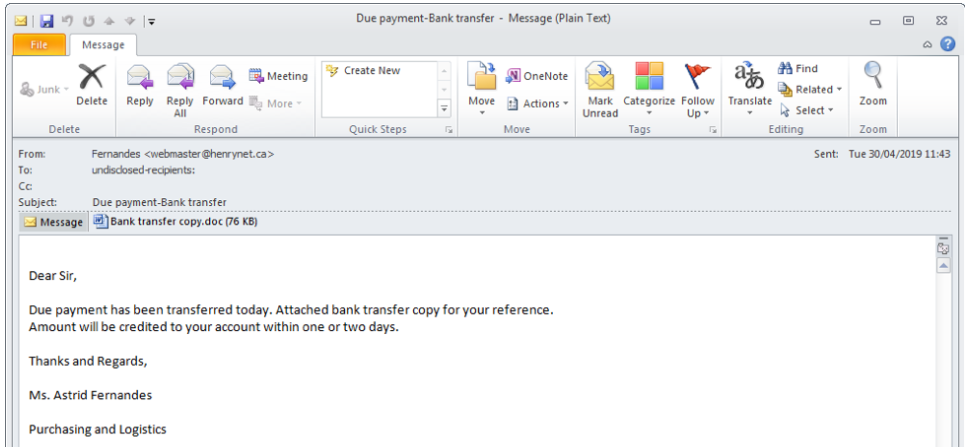
KPOT Stealer Reaches Version 2.0 and Brings New Features
- KPOT v2.0 has been released and comes with several new features, improvements, and additions.
- The new version of the malware stealer costs only $100, so it’s accessible by anyone out there.
- People should remain cautious with their inbox, as email campaigns are still the main way of KPOT distribution.
The KPOT stealer is one dangerous piece of malware targeting account information and other sensitive user data by monitoring and intercepting messenger apps, web browser, email, and even VPN traffic data. Having an already successful record out in the wild, malicious hackers have updated the exploitation kit and now sell KPOT v2.0 for $100 on darknet forums. The changelog of this version is quite extensive, with the following improvements and additions being the most notable:
- Added the ability to grab files from across the entire dist and over the network.
- The grabber is now copying the user directories by maintaining the original folder structure.
- Added Outlook collection from the registry for all users from which it is possible to collect.
- Added collection of x64 and x86 programs in the system information.
- Reworked collection from Windows storage to collect all data packs without filtering.
- Improved resolving of .bit domains with the addition of DNS and dot-bit proxy.
Already, Proofpoint researchers have spotted email campaigns that try to spread the new KPOT, taking advantage of the CVE-2017-11882 exploit through RTF documents that are attached to the emails. There’s also an intermediate downloader that fetches a malicious Powershell script which includes a Base64-encoded payload. The command and control server remains the familiar HTTP one, with the responses from the C&C being encrypted.
image source: proofpoint.com
The information that KPOT 2.0 can exfiltrate from the infected system includes hardware info, user names, external IP, OS version, machine GUID, keyboard layouts, and a list of the installed software. By identifying what’s there, KPOT activates the required credential stealing modules that cover the following software: Chrome, Firefox, Internet Explorer, Skype, Telegram, Discord, Battle.net, Steam, Jabber. Apart from these, KPOT can also steal various cryptocurrency files, FTP client accounts, Windows credentials, and even take screenshots.
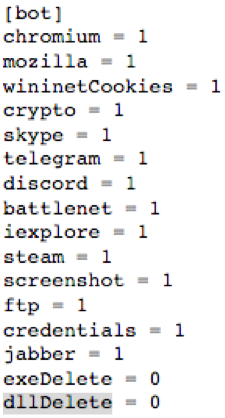
image source: proofpoint.com
The takeaway is that particularly capable stealers like the KPOT are now as cheap as $100, which makes their deployment more accessible and potentially widespread than ever. KPOT v2.0 may be able to exploit a broad spectrum of applications, but it’s important to remember that it all starts with you opening an unsolicited email. Don’t click on links found in email messages that come from addresses that you don’t recognize, don’t download attachments, and don’t run executables. If you don’t need macros on your office suite, disable them. Finally, use an AV solution from a reputable vendor and update it regularly.
Have something to say on the above? Do it by leaving a comment down below, or hop to our socials on Facebook and Twitter for more fresh news and tech stories.