How an Email Sent to Kindle Could Lead to Root RCE on the Device
- Kindle devices using outdated firmware are vulnerable to root RCE by MOBI files arriving via email.
- The attack called “KindleDrip” involves three individual vulnerabilities chained together.
- The fix came out in December 2020, and there are no indications of this being under active exploitation.
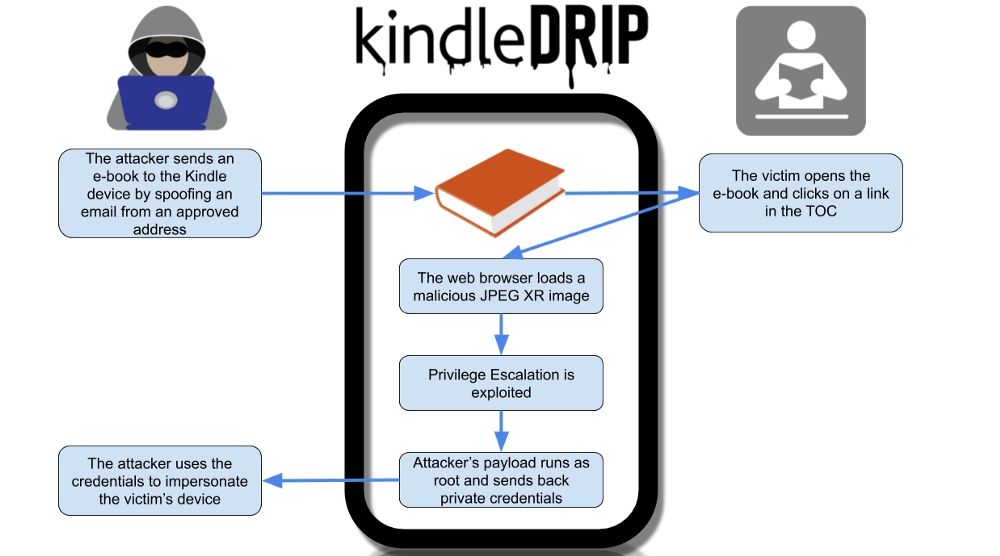
Security researcher Yogen Bar-On has posted a write-up detailing how “KindleDrip” works, an attack based on the exploitation of the “Send to Kindle” function on Amazon’s popular e-book reader device. This function allows someone to send e-books as attachments via email, so inevitably, there’s the potential of receiving a malicious file that is specially crafted to bring trouble. The researcher found three individual vulnerabilities that could be chained together, making up the "KindleDrip" attack.
The first flaw allows an attacker to send an e-book to the victim’s Kindle device. The second vulnerability allows the actor to run arbitrary code when the e-book is parsed but at the level of an unprivileged user. The third bug is where the escalation of privilege happens, allowing the malicious actor to run code as root, essentially doing everything they want on the device. Most notably, jailbreak the device, access the user’s credentials, and make purchases on the Kindle store.
To initiate the KindleDrip attack, the attacker has to send a MOBI e-book to the target device. Amazon generates and assigns a special “kindle.com” email address for each user, so the attack needs to have a valid address for this purpose. Because Amazon doesn’t have a sender authenticity verification system in place, one may set up an email spoofing platform and use addresses for a predefined list of approved emails to send files to Kindle devices.
In the MOBI file, the attacker adds a web link leading to an HTML page that contains a malicious JPEG XR image file, which is what triggers a buffer overflow exploit. The third exploit to complete the attack is based on abusing a vulnerable root process that listens on a local socket, bypassing security checks by starting strings with digits, ending up with the ability to run code under the root user context.
Before you freak out, we should point out that the researcher has informed Amazon of his findings before their publication, he received a bounty of $18k for his reports, and a firmware update that addressed the problem has already been released. That would be firmware version 5.13.4, released on December 10, 2020, so if you haven’t applied the update yet, do it now. The report came out on October 17, 2020, and it is unknown if anyone has exploited “KindleDrip” before that date, but this is considered unlikely.