Kids’ Apps on Play Store Found Ridden With the Tekya Clicker Malware
- A collection of 56 apps infected with clicker malware was discovered in the Play Store.
- Google has removed them all by now, but a million users have already downloaded and installed them.
- The malware features a high level of persistence and some mechanisms to avoid detection too.
A team of researchers from Checkpoint reported a fresh batch of apps that contain the ‘Tekya’ ad-fraud malware. This adware is emulating user clicks on ads and banners from Google’s AdMob, Facebook, Unity, and AppLovin’, in similar ways as what we have seen time and time again in the recent past. The collection of the 56 applications that contain the Tekya malware is targeting the younger audience, as they are mainly puzzle and racing games, cooking apps, calculators, downloaders, translators, and more. In total, the total number of installations of these apps is almost one million.
The most popular of these dangerous apps are the following:
- “Race in Space” by Caracal Entertainment (Vietnam)
- “Cooking Delicious” also by Caracal
- “Let Me Go” by Leopardus Studio
- “Calculator” by Biscuit Ent
- “Stickman Aquawar” by Pantanal Entertainment
- “Dress Up” by Pantanal
- “Inferno Translator” by World TravelX
- “Translate Travel Map” by Lynx StudioX
Source: CheckPoint
All of the above, as well as the others in the long list that was published by Checkpoint, have been reported to Google which resulted in their removal from the Play Store. If you still have these apps installed on your phone, though, you’ll have to manually remove them immediately.
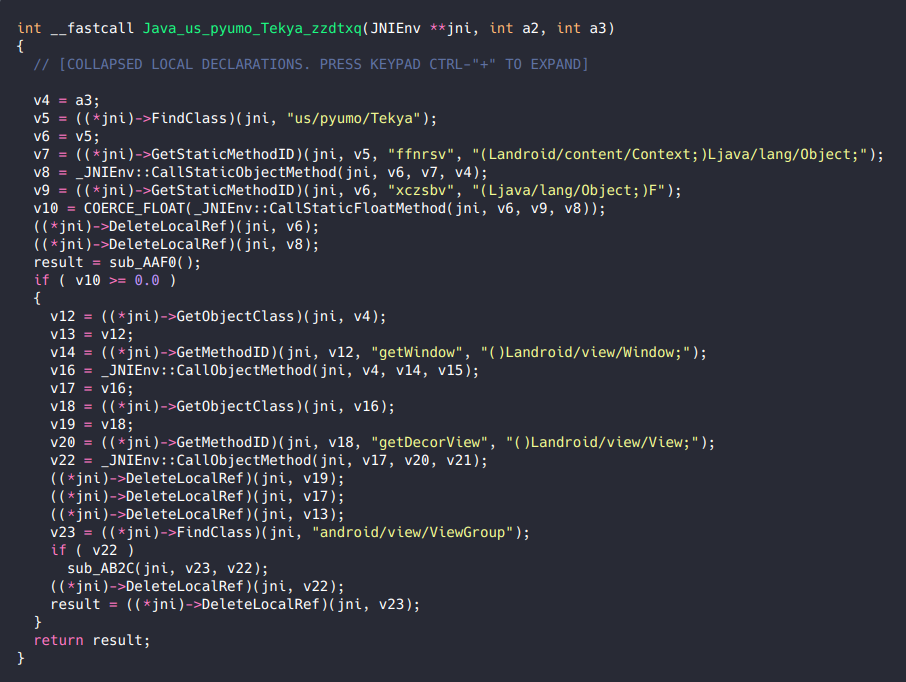
Tekya is basing its operation on three main pillars. First, it establishes persistence by listening for the ‘BOOT_COMPLETED’ broadcast, so the malicious ad-fraud service is initiated immediately upon “cold” startups. Secondly, the malware detects if the user is actively using the infected device through ‘USER_PRESENT.’ Thirdly, there’s the ‘QUICKBOOT_POWERON’ to launch the malicious code after a device restarts. From there, a native library named ‘libtekya.so’ is parsing the configuration file, receives the needed handles, and finally calls a sub-function. This last step is what creates these fraudulent touch events, imitating the ‘MotionEvent’ mechanism.
Source: CheckPoint
These apps were available in the Play Store and carried the Play Protect badge, so this is another story aimed at highlighting the dangers that lurk even in marketplaces that try hard to be a safe place. For this reason, you should not rely on Google’s guarantees and internal checks alone. Pick a powerful mobile security suite from a trusty vendor and keep your apps and OS up to date by applying the latest available patches. Finally, monitor battery usage and internet data consumption, which should help you locate clicker apps soon after their installation.