Kaspersky Internet Security Tools Could Compromise the Privacy of their Users
- Multiple Kaspersky products followed a URL checking practice that enabled individual user tracking online.
- The issue has been fixed through an update that came out last month, but not all implications have been resolved.
- Users could disable the URL checking in their products and browse the Web without revealing any details about themselves.
A discovery by security researcher Ronald Eikenberg reveals that the privacy of the users of Kaspersky Anti-Virus, Kaspersky Internet Security, and Kaspersky Total Security could be compromised by a flaw that affects all of these products. The particular vulnerability was given the identifier “CVE-2019-8286”, and it affects all versions of the aforementioned products, going up to the 2019 editions. Kaspersky has acknowledged the problem upon the reception of the researcher’s report and pushed a fixing update last month, so everyone is urged to update their tools immediately.
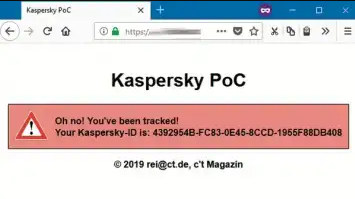
While the severity of the flaw was given a “medium” score, it could cause trouble or open the door to more targeted and devastating attacks. The problem resides in the URL scanning module that is common among the various Kaspersky products, and which deploys a JavaScript file into the HTML code of all websites visited by the user, including those in 'incognito' mode. The purpose of this is to check the URL against a list of blacklisted web addresses and keep the users safe from phishing and malware attacks. However, this JavaScript file contains a unique UUID (Universally Unique Identifier) which is unique to each user.
image source: heise.de
Websites or attackers using other scripts could capture this UUID and then use it for targeted advertising purposes, extensive tracking, analytics, or malicious purposes. Long story short, the UUID compromises the privacy of the users. For his proof-of-concept demonstration, the researcher actually created a website that would grab the visitor’s Kaspersky ID. After logging a couple of test computers used by his colleagues, he showed the persistence of the tracking by serving them with personal greetings even when they used different browsers, had cleared the cookies, or even used the incognito mode to visit the demo webpage.
image source: heise.de
The way that Kaspersky fixed this is by changing the UUID to a constant value that is the same for all users. This way, there can be no separation and identification between the many thousands of Kaspersky customers. However, websites can still tell if their visitors are using a Kaspersky product or not, and this is still a concern for their privacy and security. For example, tailored malware that takes advantage of specific vulnerabilities is one example of the risk that it’s still there. Another one would be a phishing attack, urging victims to pay for a new Kaspersky license as their previous one has expired. If you’re worried about all this, you may simply disable the Kaspersky URL Advisor from the settings, but this would also mean that the suite won’t check the URLs you are visiting against their “known threats database”.
Are you using a Kaspersky product? Have you noticed cases of persistent tracking? Share the details with us in the comments down below, or on our socials, on Facebook and Twitter.