Kaiser Permanente Employees Targeted via Malicious Google Search Ads to Deploy SocGholish
- A malicious ad campaign was seen targeting Kaiser Permanente employees via Google Search Ads.
- Impersonating the company's HR portal, the campaign’s main goal seemed to be phishing credentials.
- The advertisement ultimately distributed SocGholish malware via a fake browser update notification.
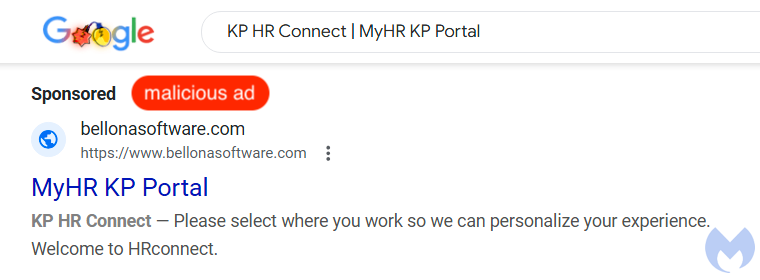
A malicious campaign targeting employees of Kaiser Permanente through Google Search Ads was identified on December 15. The fraudulent ad disguised itself as the company's HR portal, which employees frequently use to check benefits, download paystubs, and other internal purposes.
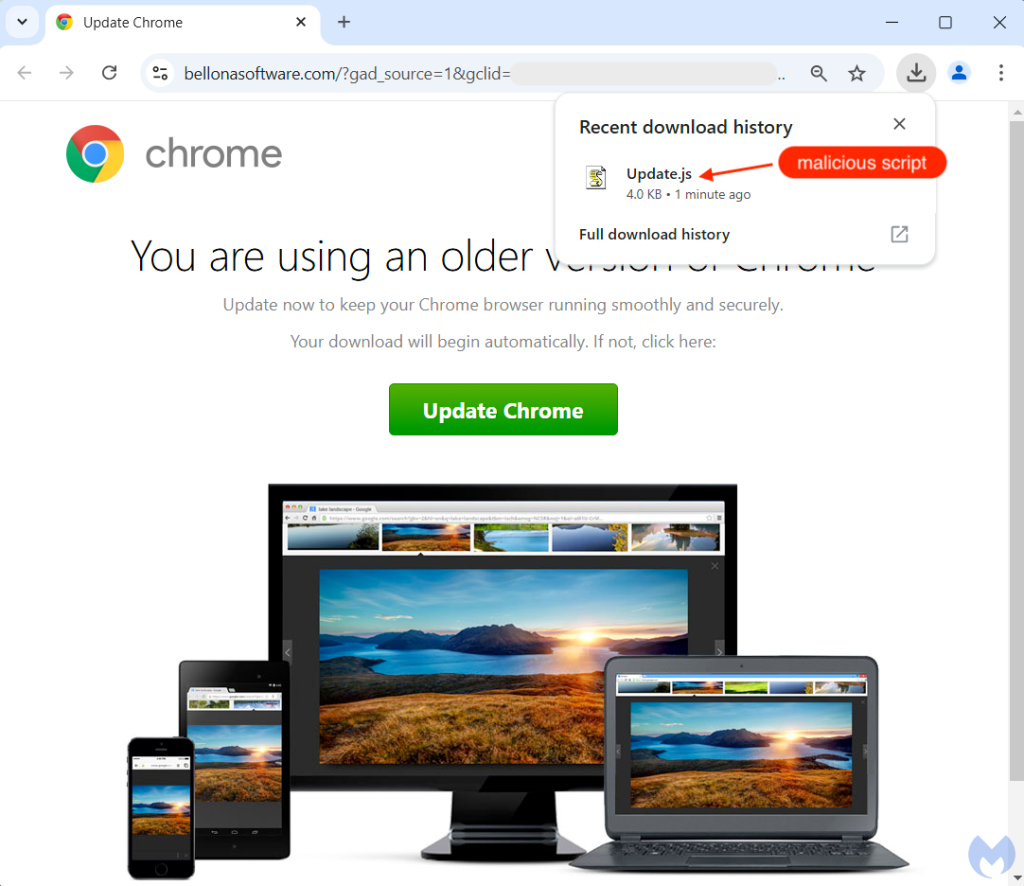
Initially, it seemed the goal of the attack was to phish employees for their login credentials. However, the attack took an unexpected turn. Instead of a standard phishing link, users were redirected to a compromised website that displayed a fake browser update notification—a hallmark of the infamous malware campaign known as SocGholish.
This campaign operates by tricking users into running a malicious script under the guise of updating their browser. Once executed, the script infects the victim's machine, allowing attackers to profile the system and gain human-on-keyboard access for more sophisticated malicious activities.
Cybercriminals leveraged Google Ads to display a malicious sponsored result when employees searched for Kaiser Permanente's HR portal, according to Malwarebytes. The fraudulent ad was created by an account named "Heather Black," as revealed by Google Ads Transparency Center.
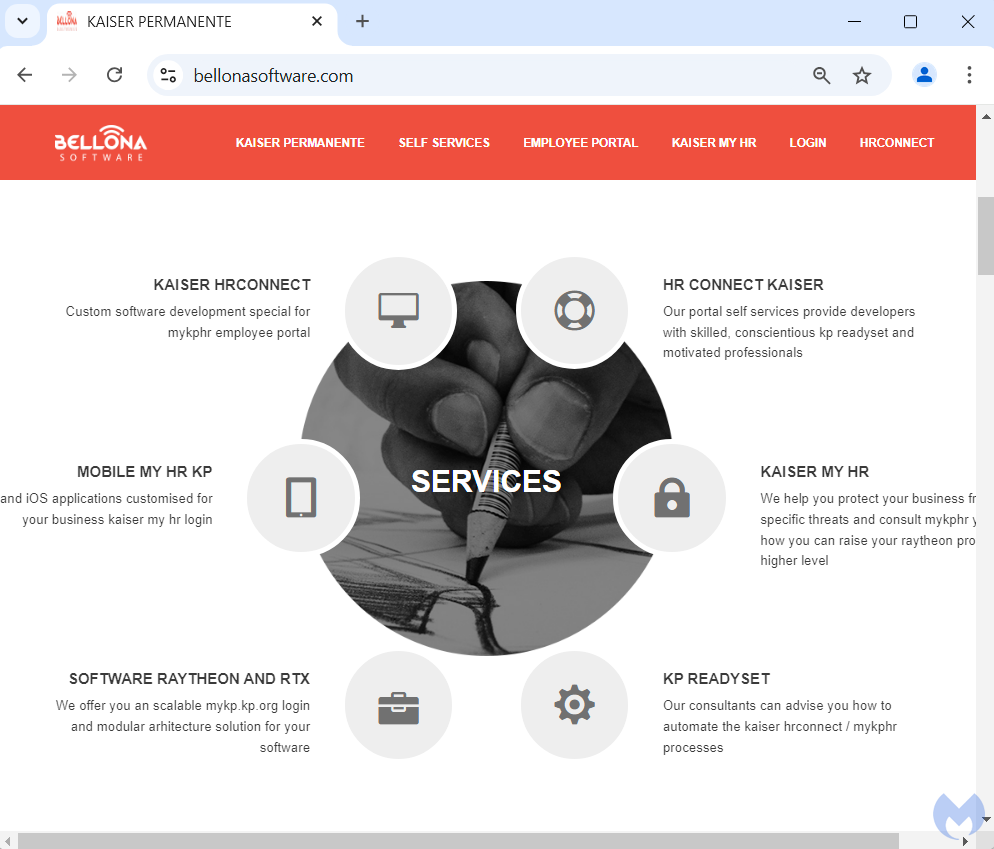
It targeted U.S.-based searches and redirected victims to "https://www.bellonasoftware[.]com," a domain previously owned by a legitimate Romanian company that has since been compromised.
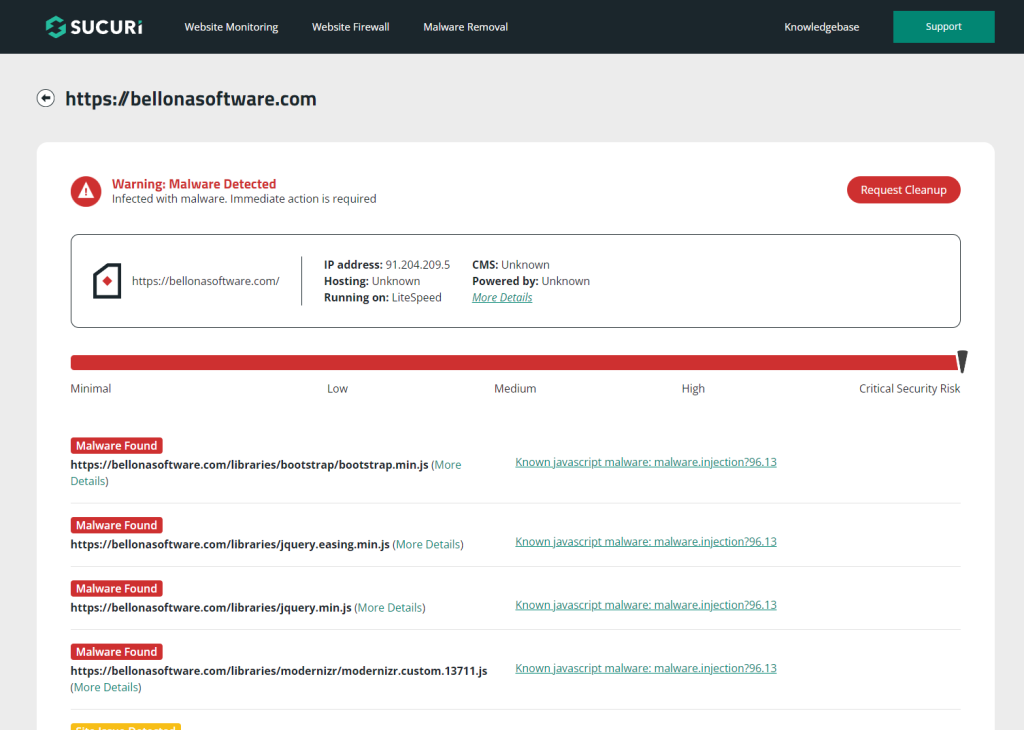
Bellona Software's website, as archived in 2021, was a legitimate professional platform. However, cybercriminals gained control of the domain and transformed it into a phishing toolkit targeting Kaiser Permanente employees. While the phishing site briefly mimicked the legitimate portal, further investigation revealed that it also contained malicious injected code.
This compromised JavaScript redirected potential victims to a SocGholish malware page immediately after engaging with the site. The transition was subtle and nearly instant, leaving users unaware of the pivot from phishing to malware distribution.
SocGholish is a notorious malware campaign that preys on vulnerable websites. It generates fake browser update notifications designed to deceive users into downloading and executing malicious scripts, such as the "Update.js" file discovered in this incident.
Once executed, the malware collects system information and can deploy additional tools like Cobalt Strike for more invasive attacks.
Unlike the original phishing agenda, the SocGholish operators appear to have independently infected the hijacked domain. This unintentional overlap means victims faced dual threats—phishing and malware—amplifying the potential for significant harm.