The “JCrush” Dating App Has Exposed All User Data, Even Messages
- JCrush has exposed a great amount of data around its users, both technical and identification details.
- It appears that only 200,000 out of a total of 1,500,000 users have been exposed, but the set includes “incognito mode” users.
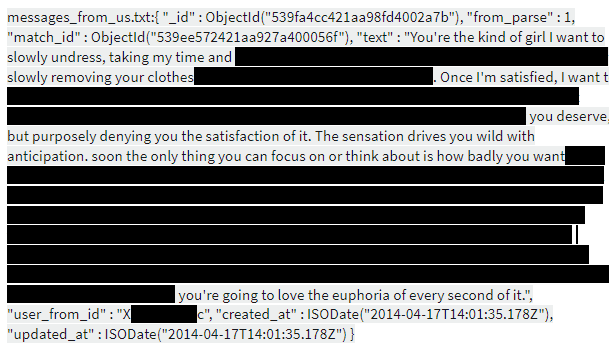
- The data that was leaked includes private messages, and often explicit photos exchanged through the app.
The “JCrush” dating app created by “Crush Mobile” has exposed over 200,000 of its users, leaking out personally identifiable information, preferences, and even the private conversations they had on the platform. The discovery of the data, which is about 18.45 GB in size, came from Noam Rotem and Ran Locar, who immediately contacted the owner on May 31, 2019.
Crush Mobile secured the data on the same day, although they failed to respond to the researchers and explain what happened or if they’re planning to inform their userbase.
Source: VPNMentor
The information that the researchers found in the exposed Mongo database includes the following details:
- First and Last names of users
- Email addresses
- Facebook tokens, which can be used for login
- Full user profiles
- Profile pictures
- Private – sometimes very intimate – messages and sensitive photos sent in those messages
- How many ‘swipes’ a user received per month
- When and where they last logged in from
- Users’ mobile device unique ID numbers
- Users’ mobile device geographic locations while the app is actively running
- Users’ computer IP addresses
- Technical information about users’ computers or mobile devices (such as type of device, web browser or operating system)
- User preferences and settings (time zone, language, privacy preferences, product preferences, etc.)
- The URL of the last web page users visited before coming to the JCrush site
- The buttons, controls and ads users clicked on (if any)
- How long users used JCrush and which services and features users have used
- The online or offline status of JCrush
Source: VPNMentor
Considering that the above constitutes a data treasure in the hands of anyone willing to exploit the set, the researchers dug deeper to find particularly sensitive users. Indeed, they found government employees from various countries, including some employed by the US National Institute of Health, US Veterans Affairs, the Brazilian Ministry of Labor and Employment, the UK’s cultural department, Israel’s Justice Department, and many more.
Moreover, the researchers found that some of the entries they looked into may point to users who paid a premium to hide behind a special “incognito mode,” offered by JCrush as an option for those who want to hide their real identities. The only positive aspect of this data discovery is that 200,000 is only a fraction of JCrush’s userbase, so not every user of the app has been exposed by this security incident.
Read More:
- Hamas Actors Hooked Israeli Soldiers on Dating Apps
- Popular iOS & Android Dating Apps Plagued by Security and Privacy Flaws
- Unprotected Server Contains Sensitive Data From Various Firms
- A Trove of Email Addresses Was Left Exposed and Accessible Online