Japanese SEO Spam Persists in Cleaned WordPress Site via ‘Sitemap’ Root Directory File
- A compromised WordPress website identified Japanese SEO spam persisted by exploiting sitemap submission settings within GSC.
- Even though the domain contained no visible malware, these links kept appearing in Google search results.
- The sitemap instructed Google to crawl over 3,000 spam URLs, which left the malicious campaign unharmed.
A recent investigation into a compromised WordPress site uncovered a persistent case of Japanese SEO spam, where malicious URLs continued to impact search engine results despite thorough website cleaning.
A recent Sucuri security report focuses on the complexity of removing SEO spam and the severe impact it can have on a site's credibility and search rankings.
Japanese SEO spam is a type of attack where malicious actors compromise websites to create deceptive URLs, sitemaps, or links that promote fraudulent or unrelated content—often in Japanese.
These malicious links and sitemaps are then indexed by search engines like Google, prominently displaying misleading content in search results.
The owner of the affected WordPress site initially flagged an influx of Japanese spam links appearing in Google search results. Still, no visible issues were detected on the website itself.
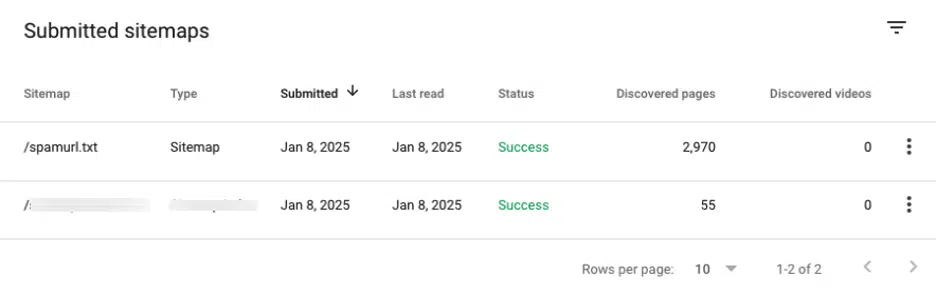
Upon further inspection, security researchers discovered a file in the site's root directory named spamurl.txt. This malicious file was being falsely used as a sitemap and had been submitted to Google Search Console (GSC) by the attackers.
The sitemap instructed Google to crawl over 3,000 spam URLs that kept the campaign going even after the site was cleaned of visible malware.
The report mentions the attackers exploited sitemap submission settings within GSC by injecting the unauthorized spamurl.txt file. This allowed Google to continually crawl and index spam URLs linked to the malicious sitemap.
By leveraging GSC settings, attackers ensured their malicious URLs remained active and impactful even after traditional malware removal efforts were completed, so security researchers recommend updating GSC settings and requesting reindexing to clear indexed spam results.