Jaguar Land Rover Falls Victim to HELLCAT Ransomware Group and Subsequent Hacker Attack
- HELLCAT ransomware group targeted JLR, which suffered a significant data breach.
- The threat actor used old infostealer-obtained Jira credentials to infiltrate the victim’s system.
- A second hacker amplified the damage by exploiting additional infostealer-acquired credentials dating back to 2021.
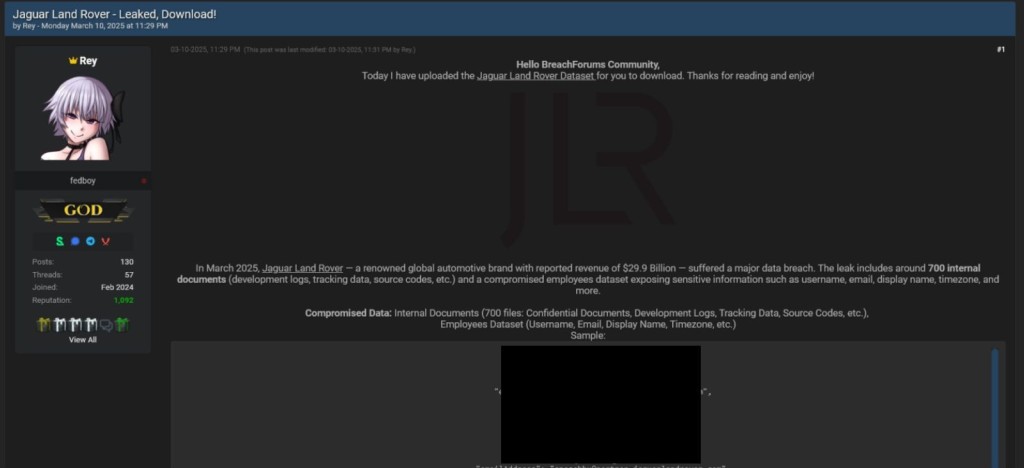
Jaguar Land Rover (JLR) has become the latest high-profile victim of the HELLCAT ransomware group in a breach that has exposed a massive trove of sensitive information, including proprietary documents, source codes, and employee data.
Details of the breach, executed by a threat actor known as “Rey,” matches a pattern of attacks previously linked to enterprises like Telefónica, Schneider Electric, and Orange.
The HELLCAT ransomware group used a signature technique in this breach. The attackers accessed JLR's systems using credentials to its Atlassian Jira software harvested by infostealer malware such as Lumma, which was also implicated in the Schneider Electric breach.
These credentials, originally belonging to an infected computer of an LG Electronics employee with third-party credentials to JLR’s Jira server, allowed the intruders to infiltrate JLR’s internal systems.
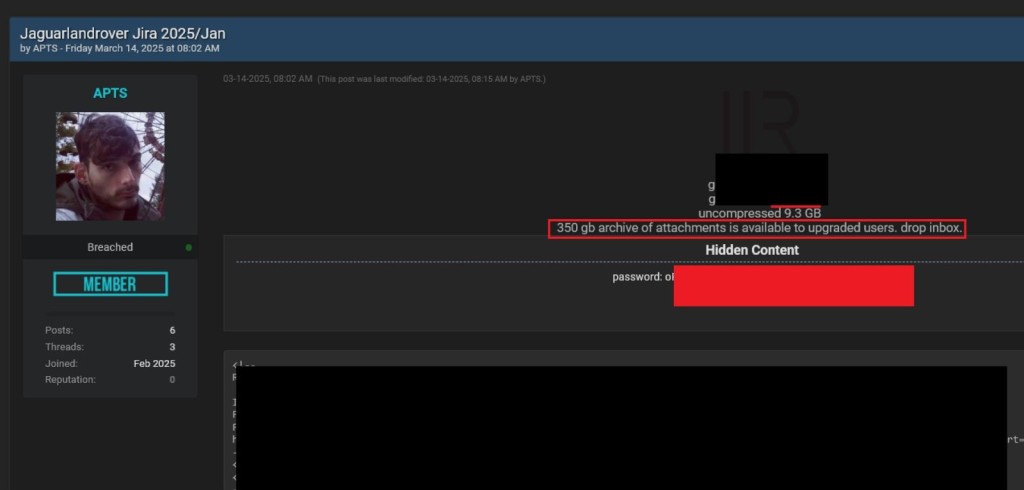
The breach escalated further when a second hacker, using the alias "APTS," exploited additional infostealer-acquired credentials dating back to 2021.
This secondary breach led to the exfiltration of an estimated 350GB of data, expanding the scope of the attack to information not covered in the initial data dump by HELLCAT. APTS even released screenshots of JLR’s Jira dashboard to prove their access.
Common methods of infection include phishing emails, malicious downloads, or compromised websites. Once an infostealer infiltrates a system, it silently harvests login credentials to enterprise tools like Atlassian Jira and sells them to cybercriminals on the dark web.
Hackers can then exploit these credentials for lateral movement, privilege escalation, and data exfiltration, as evident in this breach. The HELLCAT and subsequent APTS intrusions demonstrate how vulnerabilities in widely used software, like Jira, can become significant liabilities when paired with infostealer malware.
The attackers leveraged credentials harvested years ago, highlighting a common enterprise pitfall of neglecting rigorous credential rotation policies. Notably, mismanaged credentials extend the lifespan of these cyber risks, offering malicious actors multiple opportunities over time.
For instance, Hudson Rock’s analysis revealed that the LG employee's compromised credentials from 2021 remained unchanged within JLR’s systems—despite their exposure in prior breaches.