Trail of Bits App Helps iPhone Owners Identify if they are Targeted by Hackers
- Trail of Bits released their “iVerify” app, promising to warn you about iPhone exploits.
- The app looks for hacking “side effects”, and provides advice on how to stay safe and secure.
- Apple was reluctant to approve the app on the App Store and is not willing to share vital info.
Every device and OS platform has it’s flaws and security vulnerabilities, and no matter how much Apple focuses on dealing with them, their presence is inevitable. Sometimes the flaws are known to the public but remain unfixable, and other times they are zero-days that the company has to deal with as soon as possible. No matter what the case is, users are often worried about whether someone could be actively seeking to exploit these flaws, and if they have been victimized without even knowing about it.
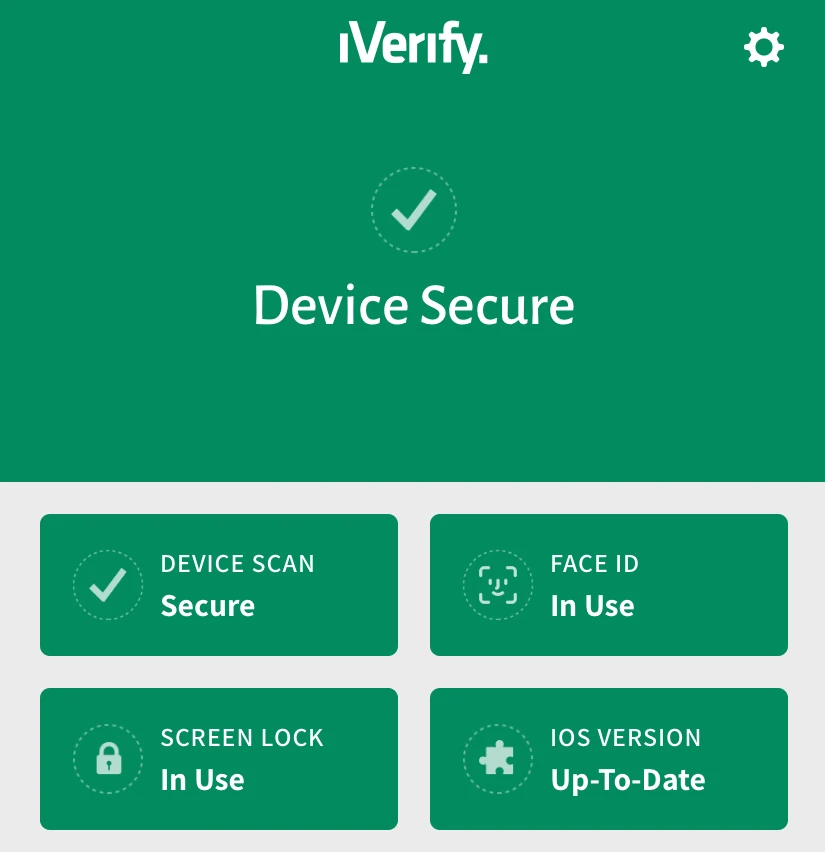
An app created by the security firm “Trail of Bits” promises to help you with that, detecting if your iPhone is being targeted by hackers, and help you stay safe. The app is called “iVerify”, is already trending on the “Utilities” category of the App Store, and has started with positive ratings and reviews that praise its clear user interface, simplicity, and features. The app is also available for the iPad, but the burning interest is to be formed around the iPhone users community. iVerify comes with device scanning capabilities, Face ID and screen lock protection, iOS version update checking, and software exploits monitoring.
Source: Vice
This last part is the key in iVerify’s functionality, as the app has all of the publicly disclosed exploits hardcoded in its database. These exploits result in identifiable side effects or anomalies in the functionality of the device, and this is precisely how iVerify knows if someone is trying to break into an iPhone device, or if they have already managed to do so. However, and due to the closed-source nature of iOS, this is not always easy to achieve. Trail of Bits is playing a cat and mouse game, putting great efforts in reverse engineering, and trying to get around an increasing number of restrictions put in place by Apple.
Apple has allowed the app to enter the App Store after it went through multiple rounds of review, but they could be collaborating with the security firm to make sure that their users are safe against all known vulnerabilities and exploits. In the end, Apple could endorse the app or even make it an integral part of the iOS security, further promoting and supporting their marketing promises with action. Instead, they choose to protect their secrets and bar everyone else outside their products. Threat profiling will gradually get more difficult, and iVerify is destined to become less powerful and irrelevant with time, no matter how hard the Trail of Bits engineers try. For now, though, it is a handy piece of software for iOS users, and we openly suggest that you give it a try.
Are you interested in apps like iVerify, or do you just trust Apple and apply the latest available updates? Let us know where you stand in the comments down below, or on our socials, on Facebook and Twitter.