SoftServe IT Firm Hacked, Locked Down, and “Plundered”
- The damage done to SoftServe may be more serious than what was initially admitted by the firm.
- Ransomware actors encrypted the company’s files, but they may have stolen source code too.
- The revelations came from Telegram channels, where anonymous tipsters shared details and screenshots.
‘SoftServe,’ one of Ukraine’s largest IT firms offering big data, cloud computing, security, DevOps, and IoT services, has been hit by ransomware actors. The date of the security incident was revealed to be September 1, 2020.
While the firm opted not to publicize anything at the time, it appears that one of its 8,000 employees leaked it on a Ukrainian Telegram channel. The message describes a cyber-attack that involves both ransomware and various malware strains but clarifies that the malicious software was contained in the firm’s systems and so no clients were infected.
This was the message shared on Telegram:
This compelled SoftServe to admit that there was an attack, but they told local news outlets that the services only had to deal with temporary downtimes. More specifically, the damage was reportedly contained to the mail system and some of the auxiliary test environments.
Senior Vice President of IT at SoftServe, Adriyan Pavlikevich, told the press that the spread of ransomware was successfully stopped by isolating some segments of their corporate network and by restricting communication with client networks.
The answer to the question of how hackers managed to breach the security of an IT expert involves Rainmeter, a Windows customization tool that was used in some of SoftServe’s computers. The hackers replaced a legitimate DLL used by Rainmeter with their own malicious version via a DLL side-loading attack, and eventually deployed CobaltStrike on the target machines.
After the statements were given, the idea that was passed to the media was that everything was under control, and customers of SoftServe were convinced of the fact. Soon, this was blown apart by a new post on the same Telegram channel.
Source: Bleeping Computer
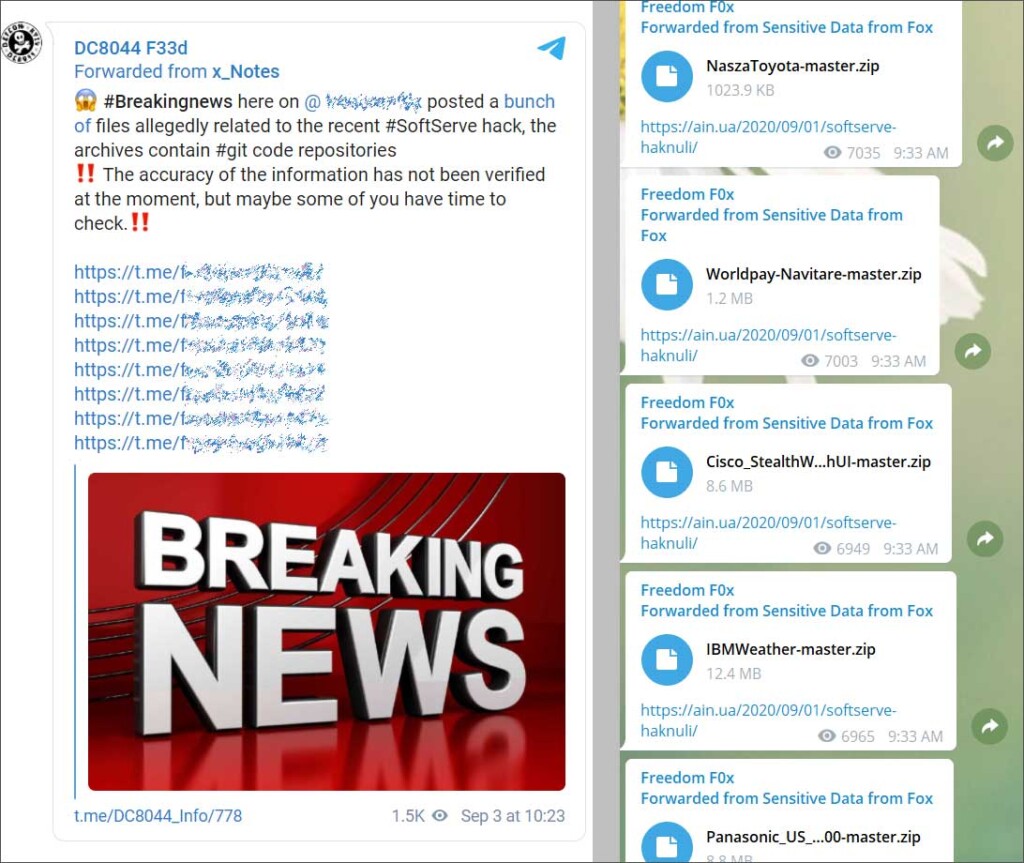
Another anonymous user posted links to source code repositories stolen during the ransomware attack, including precious zip files from projects involving Toyota, Panasonic, IBM, Cisco, WorldPay, and ADT. While there’s no proof that these files actually come from SoftServe, there are multiple references to the company in the source code.
Read More:
- “Telmate” Prison Communications Exposes Personal Data of Millions
- The ‘Warner Music Group’ Announced a Credit Card Data Breach
- ‘View Media’ Exposed 39 Million User Records on Unprotected AWS Database