Iranian State-Sponsored APT33 Targets US and UAE with Novel Custom Multi-Stage Backdoor
- Security researchers observed a known Iranian state-sponsored threat actor changing its approach toward the US and other targets.
- The threat actor is believed to be focusing on gathering intelligence on organizations and their employees.
- Federal, state, satellite, oil, gas, and communication equipment sectors are among the targets of the group’s new backdoor.
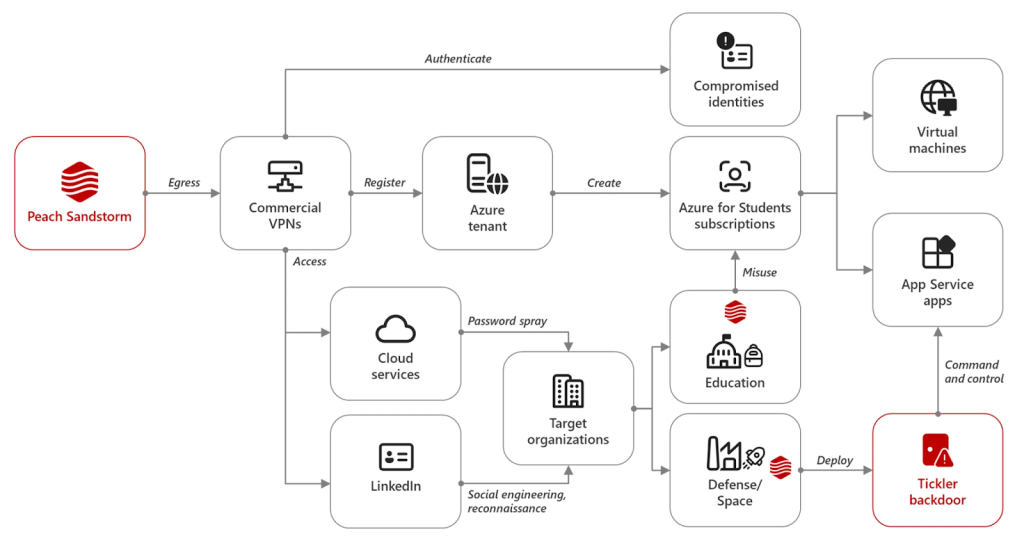
Iranian state-sponsored threat actor Peach Sandstorm, also known as APT33, was seen deploying a new custom multi-stage backdoor, the latest report from Microsoft said. The cybercriminals deploy it in attacks targeting the U.S. and U.A.E. satellite, communications equipment, oil and gas, and federal and state government sectors.
The threat actor focuses on higher education, satellite, and defense organizations and employees, conducting intelligence gathering (possible social engineering) via the professional networking platform LinkedIn and password spray attacks.
APT33 operated several LinkedIn profiles pretending to be students, developers, and talent acquisition managers from the US and Western Europe.
The cybercriminal group deployed a new backdoor, named Tickler by Microsoft, and leveraged Azure infrastructure hosted in attacker-controlled Azure subscriptions for command and control (C2) servers.
One Tickler sample was bundled in a ZIP archive file with decoy PDF documents, and another was a Trojan dropper with identical functionality to the previous sample.
The threat actor created Azure tenants using Microsoft Outlook email accounts, adding Azure for Students subscriptions. They also leveraged compromised user accounts in the Azure tenants of organizations in the education sector in the same way. They then created Azure resources for use as C2 for the backdoor.
APT33 moved laterally via a Server Message Block (SMB) protocol exploit. Multiple Iranian groups were seen using similar techniques in recent months.
Affected organizations were notified, and Microsoft disrupted the fraudulent Azure infrastructure and accounts associated with malicious activity.
Based on the group’s victimology and operational focus, Microsoft assesses that APT33 is connected to the Iranian Islamic Revolutionary Guard Corps (IRGC), harvesting intelligence for the Iranian state.
Iranian state-backed threat actor APT42, which targets high-profile accounts of both political campaigns connected to the upcoming U.S. presidential election, was also associated with IRGC.
The U.S. State Department identified six IRGC-linked Iranian security officials reportedly responsible for the cyberattacks on U.S. water utilities in 2023.
The APT33 hacking group is known to target oil and aviation industries through a new C&C infrastructure that sits behind multiple obfuscation layers, with the most notable campaign being the Shamoon data-wiping malware that targeted oil companies back in 2017. In 2021, researchers found the gang was using a custom VPN network.